Flexible Database Generators
... in the number of duplicates per distinct value. Note that histograms are not just used to estimate the cardinality of range queries, but also to approximate the result size of complex queries that might involve joins and aggregations. Therefore, a thorough validation of a new histogram technique nee ...
... in the number of duplicates per distinct value. Note that histograms are not just used to estimate the cardinality of range queries, but also to approximate the result size of complex queries that might involve joins and aggregations. Therefore, a thorough validation of a new histogram technique nee ...
All-Flash Arrays for Improving Database Performance to
... Databases are used to extract the required information from large amounts of data at high speed. To achieve high-speed data access, database operations should be performed on the server as much as possible. The access frequency to the storage system can be reduced by keeping and buffering an index i ...
... Databases are used to extract the required information from large amounts of data at high speed. To achieve high-speed data access, database operations should be performed on the server as much as possible. The access frequency to the storage system can be reduced by keeping and buffering an index i ...
R - Kansas State University - Laboratory for Knowledge Discovery in
... Drop and Alter Table Constructs: Review The drop table command deletes all information about the dropped relation from the database. The alter table command is used to add attributes to an existing relation: alter table r add A D where A is the name of the attribute to be added to relation r an ...
... Drop and Alter Table Constructs: Review The drop table command deletes all information about the dropped relation from the database. The alter table command is used to add attributes to an existing relation: alter table r add A D where A is the name of the attribute to be added to relation r an ...
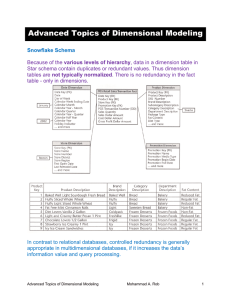
Dimensional Modeling
... The major difference between the snowflake and star schemas is that the dimension tables in the snowflake schema may be kept in normalized form. This reduces redundancies and as such, the tables are easy to maintain. For example, if a department name is changed, it will require only to change in one ...
... The major difference between the snowflake and star schemas is that the dimension tables in the snowflake schema may be kept in normalized form. This reduces redundancies and as such, the tables are easy to maintain. For example, if a department name is changed, it will require only to change in one ...
Transaction Management and Concurrency Control
... Restores database from a given state, usually inconsistent, to a previously consistent state Based on the atomic transaction property All portions of the transaction must be treated as a single logical unit of work, in which all operations must be applied and completed to produce a consistent ...
... Restores database from a given state, usually inconsistent, to a previously consistent state Based on the atomic transaction property All portions of the transaction must be treated as a single logical unit of work, in which all operations must be applied and completed to produce a consistent ...
Introduction to SQL
... the data in that column must have a different value (no duplicates) for each row of data within that table. Where a column or set of columns is designated as UNIQUE, this is a candidate key. Only one candidate key may be designated as a PRIMARY KEY • 4. Identify all primary key-foreign key mates. Fo ...
... the data in that column must have a different value (no duplicates) for each row of data within that table. Where a column or set of columns is designated as UNIQUE, this is a candidate key. Only one candidate key may be designated as a PRIMARY KEY • 4. Identify all primary key-foreign key mates. Fo ...
S3_Chapters4
... A session is started when a customer inserts an ATM card into the card reader slot of the machine. The ATM pulls the card into the machine and reads it. (If the reader cannot read the card due to improper insertion or a damaged stripe, the card is ejected, an error screen is displayed, and the sessi ...
... A session is started when a customer inserts an ATM card into the card reader slot of the machine. The ATM pulls the card into the machine and reads it. (If the reader cannot read the card due to improper insertion or a damaged stripe, the card is ejected, an error screen is displayed, and the sessi ...
Detailed Functional Model of the OAIS Reference
... Currently, this takes the form of periodic reports and updates as requested by DISC, followed by documents being added to Digital Projects page. Not a formal activity of any particular department, staff member, or cross-departmental group other than DISC. ...
... Currently, this takes the form of periodic reports and updates as requested by DISC, followed by documents being added to Digital Projects page. Not a formal activity of any particular department, staff member, or cross-departmental group other than DISC. ...
Maintaining Database Integrity with Refinement Types
... Database integrity in this example amounts to three constraints: marriage is monogamous (you cannot have two spouses), symmetric (if you marry someone they must be married to you), and irreflexive (you cannot marry yourself). – The primary key constraint PK Marriage in conjunction with the uniquenes ...
... Database integrity in this example amounts to three constraints: marriage is monogamous (you cannot have two spouses), symmetric (if you marry someone they must be married to you), and irreflexive (you cannot marry yourself). – The primary key constraint PK Marriage in conjunction with the uniquenes ...
Transferring Data with DB Connect
... The database-dependent part of the SAP database interface can be found in its own library that is dynamically linked to the SAP kernel. This database library contains the Database Shared Library (DBSL), as well as libraries belonging to the corresponding database manufacturer. These are either stati ...
... The database-dependent part of the SAP database interface can be found in its own library that is dynamically linked to the SAP kernel. This database library contains the Database Shared Library (DBSL), as well as libraries belonging to the corresponding database manufacturer. These are either stati ...
Instructions - Class Pages
... where applicable. The database file for this assignment is on the class web site as a zipped archive file. You must download the indicated file for this assignment and extract it. ...
... where applicable. The database file for this assignment is on the class web site as a zipped archive file. You must download the indicated file for this assignment and extract it. ...
Disk and I/O Tuning on SQL Server 2005
... • Anyone with access to notepad/wordpad can view potentially sensitive data contained in a backup file • Same care taken to secure database should be taken to secure backup file ...
... • Anyone with access to notepad/wordpad can view potentially sensitive data contained in a backup file • Same care taken to secure database should be taken to secure backup file ...
VPARS DataBase - Virtual Software Systems, Inc.
... Loosely-Coupled VPARS • All participating loosely-coupled TPF virtual machines write to the same VPARS database. ...
... Loosely-Coupled VPARS • All participating loosely-coupled TPF virtual machines write to the same VPARS database. ...
Optimization of Data Warehouse Design and Architecture
... When designing a data warehouse or a database system there are a number of desirable characteristics that one is keen to optimize. It should be scalable, accessible, response time should always be in acceptable limits. It should be easy to maintain and so on. There are a number of design and archite ...
... When designing a data warehouse or a database system there are a number of desirable characteristics that one is keen to optimize. It should be scalable, accessible, response time should always be in acceptable limits. It should be easy to maintain and so on. There are a number of design and archite ...
Report Footer
... • Reports allow you to group related information from one or more tables • Reports provide hard copy output that summarizes and subtotals data found in the database • Reports can produce mailing labels on standard label maker forms in postal ...
... • Reports allow you to group related information from one or more tables • Reports provide hard copy output that summarizes and subtotals data found in the database • Reports can produce mailing labels on standard label maker forms in postal ...
TinyDB Documentation
... This will remove the key key1 from all matching elements. TinyDB comes with these operations: • delete(key): delete a key from the element • increment(key): increment the value of a key • decrement(key): decrement the value of a key Of course you also can write your own operations: ...
... This will remove the key key1 from all matching elements. TinyDB comes with these operations: • delete(key): delete a key from the element • increment(key): increment the value of a key • decrement(key): decrement the value of a key Of course you also can write your own operations: ...
Document
... extreme performance demands on the concurrency control and recovery components of a database -- it exposes hotspots and high-overhead code. Concurrency control: The dequeue transaction typically involves deleting a record from the queue, processing the request, enqueuing results in other queues, and ...
... extreme performance demands on the concurrency control and recovery components of a database -- it exposes hotspots and high-overhead code. Concurrency control: The dequeue transaction typically involves deleting a record from the queue, processing the request, enqueuing results in other queues, and ...
Big Data Frameworks: At a Glance - Academic Science,International
... from different sources like enterprise, government organization and business organizing, data from telecom industries and social networking sites is carried out in the first step of the processing for big data where different activities like data processing, Data cleaning, Integration, Normalization ...
... from different sources like enterprise, government organization and business organizing, data from telecom industries and social networking sites is carried out in the first step of the processing for big data where different activities like data processing, Data cleaning, Integration, Normalization ...
Enterprise Reporting with Reporting Services
... Strong Management Story SOAP Web Service APIs Report Manager portal Extensible security model Integration with AS, IS, management tools ...
... Strong Management Story SOAP Web Service APIs Report Manager portal Extensible security model Integration with AS, IS, management tools ...
SQL Databases
... SQLite Simple Queries - Template Based Queries Simple SQLite queries use a template oriented schema whose goal is to ‘help’ non-SQL developers in their process of querying a database. This template exposes all the components of a basic SQL-select statement. Simple queries can only retrieve data from ...
... SQLite Simple Queries - Template Based Queries Simple SQLite queries use a template oriented schema whose goal is to ‘help’ non-SQL developers in their process of querying a database. This template exposes all the components of a basic SQL-select statement. Simple queries can only retrieve data from ...
PostGIS Analysis Tool (PGAT)
... relationship grouping of the disjointed polygons. PGAT incorporates an algorithm that runs until 1 000 times faster than using the SQL aggregate 'geomunion' (see the 'not join disjointed geometries' checkbox in Fig. 6). This algorithm appears in detail in the paper which title is ‘Improving dissolve ...
... relationship grouping of the disjointed polygons. PGAT incorporates an algorithm that runs until 1 000 times faster than using the SQL aggregate 'geomunion' (see the 'not join disjointed geometries' checkbox in Fig. 6). This algorithm appears in detail in the paper which title is ‘Improving dissolve ...
Selecting SRM tools
... • Database vs. flat file: DBMS key for data export • A single database for all capabilities (capacity management, performance management, etc.) not separate utilities glued together with a common look and feel and a console. ...
... • Database vs. flat file: DBMS key for data export • A single database for all capabilities (capacity management, performance management, etc.) not separate utilities glued together with a common look and feel and a console. ...
Database model

A database model is a type of data model that determines the logical structure of a database and fundamentally determines in which manner data can be stored, organized, and manipulated. The most popular example of a database model is the relational model, which uses a table-based format.