Structured Database Running on Appaserver
... enforcement are: * Implementational restrictions (bad) ...
... enforcement are: * Implementational restrictions (bad) ...
SQL: Queries, Programming, Triggers
... A schema in BCNF avoids the above anomalies. A given schema can be decomposed into subsets of attributes such that the resulting tables are all in BCNF and the join of these tables recovers the original table. ...
... A schema in BCNF avoids the above anomalies. A given schema can be decomposed into subsets of attributes such that the resulting tables are all in BCNF and the join of these tables recovers the original table. ...
QuotesDBAdapter.java
... import java.util.Random; import android.content.ContentValues; import android.content.Context; import android.database.Cursor; import android.database.SQLException; import android.database.sqlite.SQLiteDatabase; import android.database.sqlite.SQLiteOpenHelper; import android.util.Log; ...
... import java.util.Random; import android.content.ContentValues; import android.content.Context; import android.database.Cursor; import android.database.SQLException; import android.database.sqlite.SQLiteDatabase; import android.database.sqlite.SQLiteOpenHelper; import android.util.Log; ...
Database Build Book - Office of the Chief Information Officer
... be rebuilt and installed from scratch. Application Portfolio Number Project Name Project Number ...
... be rebuilt and installed from scratch. Application Portfolio Number Project Name Project Number ...
The SQL Query Language COS 597A: Principles of Database and Information Systems
... To understand semantics of nested queries, think of a nested loops evaluation: For each Acct tuple, check the qualification by computing the subquery. Based on slides for Database Management Systems by R. Ramakrishnan and J. Gehrke ...
... To understand semantics of nested queries, think of a nested loops evaluation: For each Acct tuple, check the qualification by computing the subquery. Based on slides for Database Management Systems by R. Ramakrishnan and J. Gehrke ...
marked - Kansas State University
... Consider a person who needs to know a customer’s loan number but has no need to see the loan amount. This person should see a relation described, in SQL, by ...
... Consider a person who needs to know a customer’s loan number but has no need to see the loan amount. This person should see a relation described, in SQL, by ...
AIS PowerPoint Presentations
... Ensuring Valid and Accurate Data Entry Data Definition Language (DDL) Enables users to define record structure Define individual fields of each record ...
... Ensuring Valid and Accurate Data Entry Data Definition Language (DDL) Enables users to define record structure Define individual fields of each record ...
Document
... parts, each with active systems that can’t talk to other parts) Brewer’s CAP Theorem: You can have at most two of these three properties for any distributed system. Very large systems will partition at some point Choose one of consistency or availability Traditional database choose consistency ...
... parts, each with active systems that can’t talk to other parts) Brewer’s CAP Theorem: You can have at most two of these three properties for any distributed system. Very large systems will partition at some point Choose one of consistency or availability Traditional database choose consistency ...
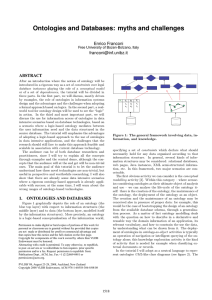
Ontologies and Databases: myths and challenges
... should be solved in the ontology-as-object scenario. More challenging are the activities that involve an ontology together with its information source. Here, typical problems are the verification of the consistency of the data with respect to the knowledge, the reasoning involving both the query and ...
... should be solved in the ontology-as-object scenario. More challenging are the activities that involve an ontology together with its information source. Here, typical problems are the verification of the consistency of the data with respect to the knowledge, the reasoning involving both the query and ...
Gancho_DB_Futures_June2011 - Indico
... However I do not see it as being activated for all quieries, but rather per specific use cases. A particular interest could for the DQ2, PanDa and TAGs systems As you know, the best metric to consider when tuning queries, is the number of Oracle block reads. Queries for which result has been gotten ...
... However I do not see it as being activated for all quieries, but rather per specific use cases. A particular interest could for the DQ2, PanDa and TAGs systems As you know, the best metric to consider when tuning queries, is the number of Oracle block reads. Queries for which result has been gotten ...
Chapter 19: Distributed Databases
... parts, each with active systems that can’t talk to other parts) Brewer’s CAP Theorem: You can have at most two of these three properties for any distributed system. Very large systems will partition at some point Choose one of consistency or availability Traditional database choose consistency ...
... parts, each with active systems that can’t talk to other parts) Brewer’s CAP Theorem: You can have at most two of these three properties for any distributed system. Very large systems will partition at some point Choose one of consistency or availability Traditional database choose consistency ...
Chapter 10 Power Points
... collection of data which can be shared by many individual users as well as by multiple applications. Users and application software access a data base through an interface – a database management system (DBMS). © 2005 Prentice Hall ...
... collection of data which can be shared by many individual users as well as by multiple applications. Users and application software access a data base through an interface – a database management system (DBMS). © 2005 Prentice Hall ...
Distributed Query Processing
... • Deal with unpredictable events at run time – delays in arrival of data, burstiness of network – autonomity of nodes, change in policies ...
... • Deal with unpredictable events at run time – delays in arrival of data, burstiness of network – autonomity of nodes, change in policies ...
Structured Query Language (SQL)
... Instuitionistic fuzzy logic is widely accepted method to analyse the imprecise and vague data. There are number of database management systems (DBMS) are available to facilitate the users to store and organize the data for the future purpose. DBMS lacks to understand the user queries in distributed ...
... Instuitionistic fuzzy logic is widely accepted method to analyse the imprecise and vague data. There are number of database management systems (DBMS) are available to facilitate the users to store and organize the data for the future purpose. DBMS lacks to understand the user queries in distributed ...
CENG 351 Introduction to Data Management and File Structures
... • logical file: a "channel" (like a telephone line) that connects the program to a physical file • The program (application) sends (or receives) bytes to (from) a file through the logical file. The program knows nothing about where the bytes go (came from). • The operating system is responsible for ...
... • logical file: a "channel" (like a telephone line) that connects the program to a physical file • The program (application) sends (or receives) bytes to (from) a file through the logical file. The program knows nothing about where the bytes go (came from). • The operating system is responsible for ...
Lecture2
... relationships are simply stated, not specified, so we simply know that two entities are related, but we do not specify what attributes are used for this relationship. ...
... relationships are simply stated, not specified, so we simply know that two entities are related, but we do not specify what attributes are used for this relationship. ...
Software architecture
... objects with well-defined interfaces. Object-oriented decomposition is concerned with identifying object classes, their attributes and operations. When implemented, objects are created from these classes and some control model used to coordinate object operations. ...
... objects with well-defined interfaces. Object-oriented decomposition is concerned with identifying object classes, their attributes and operations. When implemented, objects are created from these classes and some control model used to coordinate object operations. ...
Slide
... Those who actually use and control the database content, and those who design, develop and maintain database applications (called “Actors on the Scene”), and Those who design and develop the DBMS software and related tools, and the computer systems operators (called “Workers Behind the ...
... Those who actually use and control the database content, and those who design, develop and maintain database applications (called “Actors on the Scene”), and Those who design and develop the DBMS software and related tools, and the computer systems operators (called “Workers Behind the ...
DataServer Best Practices and Performance Considerations with
... Use Schema Pull to create schema holder definitions of foreign database objects. There is no single source copy of OpenEdge database. Schema Pull is a server based objects OE application model e.g. stored procedures, views are foreign database specifics. New independent schema pull in batch mo ...
... Use Schema Pull to create schema holder definitions of foreign database objects. There is no single source copy of OpenEdge database. Schema Pull is a server based objects OE application model e.g. stored procedures, views are foreign database specifics. New independent schema pull in batch mo ...
Database Security
... Organizations considering this should thoroughly test that data which is encrypted before storage offline can be decrypted and re-imported successfully before embarking on large-scale encryption of ...
... Organizations considering this should thoroughly test that data which is encrypted before storage offline can be decrypted and re-imported successfully before embarking on large-scale encryption of ...
Project management
... database • For example, an “employee” entity bean may have a Social Security number as primary key • You can only use entity beans when your objects have a unique identifier field, or when you can add such a field (or set of fields) ...
... database • For example, an “employee” entity bean may have a Social Security number as primary key • You can only use entity beans when your objects have a unique identifier field, or when you can add such a field (or set of fields) ...
Interactive Reporting Enhancements V 11
... choose as data model topics. While ODBC/ODBC continue to work, a new Server Code, ‘Oracle BI Server’ was introduced so that some of the options/ interactions can be disabled in Interactive Reporting. Note that ODBC/ODBC can always be used, and is not handled in any special way for connecting to ‘Ora ...
... choose as data model topics. While ODBC/ODBC continue to work, a new Server Code, ‘Oracle BI Server’ was introduced so that some of the options/ interactions can be disabled in Interactive Reporting. Note that ODBC/ODBC can always be used, and is not handled in any special way for connecting to ‘Ora ...
Relational model
The relational model for database management is an approach to managing data using a structure and language consistent with first-order predicate logic, first described in 1969 by Edgar F. Codd. In the relational model of a database, all data is represented in terms of tuples, grouped into relations. A database organized in terms of the relational model is a relational database.The purpose of the relational model is to provide a declarative method for specifying data and queries: users directly state what information the database contains and what information they want from it, and let the database management system software take care of describing data structures for storing the data and retrieval procedures for answering queries.Most relational databases use the SQL data definition and query language; these systems implement what can be regarded as an engineering approximation to the relational model. A table in an SQL database schema corresponds to a predicate variable; the contents of a table to a relation; key constraints, other constraints, and SQL queries correspond to predicates. However, SQL databases deviate from the relational model in many details, and Codd fiercely argued against deviations that compromise the original principles.