Database Security
... • When CHECKSUM is enabled for the PAGE_VERIFY database option, the SQL Server Database Engine calculates a checksum over the contents of the whole page, and stores the value in the page header when a page is written to disk. When the page is read from disk, the checksum is recomputed and compared t ...
... • When CHECKSUM is enabled for the PAGE_VERIFY database option, the SQL Server Database Engine calculates a checksum over the contents of the whole page, and stores the value in the page header when a page is written to disk. When the page is read from disk, the checksum is recomputed and compared t ...
Concepts for Object-Oriented Databases
... should not change. This preserves the identity of the realworld object being represented. ...
... should not change. This preserves the identity of the realworld object being represented. ...
mod-9
... Use the union rule to replace any dependencies in F a1 1 and a1 2 with a1 1 2 Find a functional dependency a with an extraneous attribute either in a or in /* Note: test for extraneous attributes done using Fc, not F*/ If an extraneous attribute is found, delete it from a until F ...
... Use the union rule to replace any dependencies in F a1 1 and a1 2 with a1 1 2 Find a functional dependency a with an extraneous attribute either in a or in /* Note: test for extraneous attributes done using Fc, not F*/ If an extraneous attribute is found, delete it from a until F ...
Data security best practices ® A practical guide to implementing
... to address the shortcomings of traditional row and column access control methods. They represent a second layer of security that complements the current table-privileges security model. More specifically, the table-privileges security model is applied first to determine whether a user is allowed to ...
... to address the shortcomings of traditional row and column access control methods. They represent a second layer of security that complements the current table-privileges security model. More specifically, the table-privileges security model is applied first to determine whether a user is allowed to ...
Buffer Management in Distributed Database Systems: A Data Mining
... Associated access Another observation from the user access pattern is that, ...
... Associated access Another observation from the user access pattern is that, ...
Understanding and Selecting a Database Assessment
... database internals in sufficient detail. Database assessment tools bridge this gap by capturing DBA utilities for automation of complex tasks, analysis of obscure settings, and separation of duties between audit and administrative roles — in such a way that non-DBAs can use them. When we started our ...
... database internals in sufficient detail. Database assessment tools bridge this gap by capturing DBA utilities for automation of complex tasks, analysis of obscure settings, and separation of duties between audit and administrative roles — in such a way that non-DBAs can use them. When we started our ...
HadoopDB: An Architectural Hybrid of MapReduce and
... partly due to the increased automation with which data can be produced (more business processes are becoming digitized), the proliferation of sensors and data-producing devices, Web-scale interactions with customers, and government compliance demands along with strategic corporate initiatives requir ...
... partly due to the increased automation with which data can be produced (more business processes are becoming digitized), the proliferation of sensors and data-producing devices, Web-scale interactions with customers, and government compliance demands along with strategic corporate initiatives requir ...
Generalized Search Trees for Database Systems
... The effort required to implement and maintain such data structures is high. As new applications need to be supported, new tree structures have to be developed from scratch, requiring new implementations of the usual tree facilities for search, maintenance, concurrency control and recovery. 2. Search ...
... The effort required to implement and maintain such data structures is high. As new applications need to be supported, new tree structures have to be developed from scratch, requiring new implementations of the usual tree facilities for search, maintenance, concurrency control and recovery. 2. Search ...
Elmasri/Navathe, Fundamentals of Database Systems, Fourth
... Information stored in databases is known as structured data because it is represented in a strict format. The DBMS then checks to ensure that all data follows the structures and constraints specified in the schema. In some applications, data is collected in an ad-hoc manner before it is known ho ...
... Information stored in databases is known as structured data because it is represented in a strict format. The DBMS then checks to ensure that all data follows the structures and constraints specified in the schema. In some applications, data is collected in an ad-hoc manner before it is known ho ...
IBM Software Group Presentation Template
... Simply upgrade to the latest version of CSDK and run the application. The new libraries will get loaded providing you enhanced functionality (like ...
... Simply upgrade to the latest version of CSDK and run the application. The new libraries will get loaded providing you enhanced functionality (like ...
FHIRFarm – How to build a FHIR Server Farm (quickly) Robert Worden
... common FHIR representation). • An application can interrogate the different FHIR servers, and compare the results • The Open Source Comparative Query Tool can compare across the servers, in terms of the FHIR Patient class model • Bulk data matching and de-duplication can be done across databases (pr ...
... common FHIR representation). • An application can interrogate the different FHIR servers, and compare the results • The Open Source Comparative Query Tool can compare across the servers, in terms of the FHIR Patient class model • Bulk data matching and de-duplication can be done across databases (pr ...
Analytical databases
... in February, and 10 computers in March, then typical query would ask for total number (i.e. sum) sold for the first quarter. On the other side, if a company had employeed 10 people in January, 7 in February, and 10 again in March, then we would usually ask about the average count for the quarter. Zb ...
... in February, and 10 computers in March, then typical query would ask for total number (i.e. sum) sold for the first quarter. On the other side, if a company had employeed 10 people in January, 7 in February, and 10 again in March, then we would usually ask about the average count for the quarter. Zb ...
Table of Contents
... 1. Install SQL Server 2005 on one or more machines connected by a local network. The basic configuration is one instance per machine. Later you can configure each of these instances as an SD-SQL Server client, server or peer (client and server). You can also install several instances per machine. Ho ...
... 1. Install SQL Server 2005 on one or more machines connected by a local network. The basic configuration is one instance per machine. Later you can configure each of these instances as an SD-SQL Server client, server or peer (client and server). You can also install several instances per machine. Ho ...
An FP Tree based Approach for Extracting Frequent Pattern from
... is a good result to the above two problems. The biggest advantage of the FP-Growth algorithm is that it only scans database twice. It directly compresses the database into a frequent pattern tree instead of using a candidate set and finally generates association rules through FP-tree [6]. FPGrowth T ...
... is a good result to the above two problems. The biggest advantage of the FP-Growth algorithm is that it only scans database twice. It directly compresses the database into a frequent pattern tree instead of using a candidate set and finally generates association rules through FP-tree [6]. FPGrowth T ...
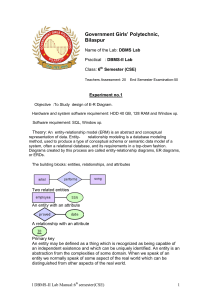
l DBMS-II Lab Manual
... make sense. The check clause in the Teradata RDBMS permit data to be restricted in powerful way that most programming language type systems do not permit. Specifically, the check clause permits the schema designer to specify a predicate that must be satisfied by any value assigned to a variable. The ...
... make sense. The check clause in the Teradata RDBMS permit data to be restricted in powerful way that most programming language type systems do not permit. Specifically, the check clause permits the schema designer to specify a predicate that must be satisfied by any value assigned to a variable. The ...
Database creation and/or reorganization over multiple database
... a complete set of algorithms for the data-language translations ...
... a complete set of algorithms for the data-language translations ...
DBAdminFund_PPT_5.2
... An incremental backup backs up only those files that have changed since the last backup. Only the changes are written to the backup media. If there has not been any changes, then no backup is made. Incremental backups should be made every day since the last full backup. ...
... An incremental backup backs up only those files that have changed since the last backup. Only the changes are written to the backup media. If there has not been any changes, then no backup is made. Incremental backups should be made every day since the last full backup. ...
Class Activity - Pearson Education
... • A user view is the set of necessary requirements to support a particular user’s operations • A database design is represented in a language called Database Design Language (DBDL) • Designs can be represented pictorially using entityrelationship (E-R) diagrams ...
... • A user view is the set of necessary requirements to support a particular user’s operations • A database design is represented in a language called Database Design Language (DBDL) • Designs can be represented pictorially using entityrelationship (E-R) diagrams ...
Beyond the Data Model: Designing the Data Warehouse
... ordered items where. Notice that in the relational model, orders have order details, and the order details contain the relationship to the actual product, since a single order can have more than one product. Additionally, orders are placed by customers, but we have a fairly simple entity storing tha ...
... ordered items where. Notice that in the relational model, orders have order details, and the order details contain the relationship to the actual product, since a single order can have more than one product. Additionally, orders are placed by customers, but we have a fairly simple entity storing tha ...
Database Management for Life Sciences Research
... much more useful than consuming a single commodity at a time. It is trivial to see that data management systems are much more useful if they contain data. Consider also what how limited the utility of genomic sequence data would be if we could only publish it in books, and manually compare it. The a ...
... much more useful than consuming a single commodity at a time. It is trivial to see that data management systems are much more useful if they contain data. Consider also what how limited the utility of genomic sequence data would be if we could only publish it in books, and manually compare it. The a ...
Relational model
The relational model for database management is an approach to managing data using a structure and language consistent with first-order predicate logic, first described in 1969 by Edgar F. Codd. In the relational model of a database, all data is represented in terms of tuples, grouped into relations. A database organized in terms of the relational model is a relational database.The purpose of the relational model is to provide a declarative method for specifying data and queries: users directly state what information the database contains and what information they want from it, and let the database management system software take care of describing data structures for storing the data and retrieval procedures for answering queries.Most relational databases use the SQL data definition and query language; these systems implement what can be regarded as an engineering approximation to the relational model. A table in an SQL database schema corresponds to a predicate variable; the contents of a table to a relation; key constraints, other constraints, and SQL queries correspond to predicates. However, SQL databases deviate from the relational model in many details, and Codd fiercely argued against deviations that compromise the original principles.