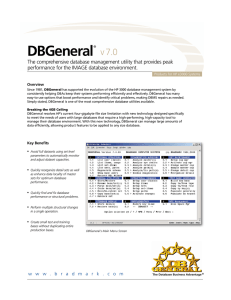
DBGeneral - Bradmark
... schema. Quickly add, delete, sort, and unsort new paths. All item type conversions are supported. ...
... schema. Quickly add, delete, sort, and unsort new paths. All item type conversions are supported. ...
Draw Back of jdbc Connectivity
... In JDBC we need to write Sql commands in various places, after the program has created if the table structure is modified then the JDBC program doesn’t work, again we need to modify and compile and re-deploy required, which is tedious JDBC used to generate database related error codes if an exceptio ...
... In JDBC we need to write Sql commands in various places, after the program has created if the table structure is modified then the JDBC program doesn’t work, again we need to modify and compile and re-deploy required, which is tedious JDBC used to generate database related error codes if an exceptio ...
data warehousing and data mining
... Essential for safety of data Hardware RAID expensive, very high availability for 24x7 applications (24 hrs X 7 days/wk) ...
... Essential for safety of data Hardware RAID expensive, very high availability for 24x7 applications (24 hrs X 7 days/wk) ...
Mid term
... 10. If you were designing a Web-based system to make airline reservations and to sell airline tickets, which DBMS Architecture would you choose from Section 2.5? Why? Why would the other architectures not be a good choice? 11. What is the difference between procedural and nonprocedural DMLs? 12. Dis ...
... 10. If you were designing a Web-based system to make airline reservations and to sell airline tickets, which DBMS Architecture would you choose from Section 2.5? Why? Why would the other architectures not be a good choice? 11. What is the difference between procedural and nonprocedural DMLs? 12. Dis ...
syllabus template - Cumberland County College
... analysis. Students gain hands-on experience in the design and creation of databases and retrieval from a database. SQL will be introduced. Learning Outcomes Upon successful completion of this course, the student should be able to: Demonstrate knowledge of fundamental data design and relational datab ...
... analysis. Students gain hands-on experience in the design and creation of databases and retrieval from a database. SQL will be introduced. Learning Outcomes Upon successful completion of this course, the student should be able to: Demonstrate knowledge of fundamental data design and relational datab ...
Resume for Rolf Martin-Hoster
... Highly qualified Director of Programming Services with proven record of accomplishment in application development and staff management. Keen sense for developing applications and introducing technology to solve business problems, increase customer satisfaction and reduce costs. Strong project manage ...
... Highly qualified Director of Programming Services with proven record of accomplishment in application development and staff management. Keen sense for developing applications and introducing technology to solve business problems, increase customer satisfaction and reduce costs. Strong project manage ...
Client Backup and Restore
... In order to back up files from a client computer that is not hosting the database files for PigCHAMP, you must set up a shared directory that both computers may access. This shared space must be accessible to the local client computer as well as the computer hosting the PigCHAMP database files. Spec ...
... In order to back up files from a client computer that is not hosting the database files for PigCHAMP, you must set up a shared directory that both computers may access. This shared space must be accessible to the local client computer as well as the computer hosting the PigCHAMP database files. Spec ...
ADBC_plugin.pdf
... The Acrobat Database Connectivity (ADBC) plug-in provides some basic JavaScript properties and methods for connecting to a database. These can be used to obtain information about the databases available on the system, the tables contained within each database and the data types used within any given ...
... The Acrobat Database Connectivity (ADBC) plug-in provides some basic JavaScript properties and methods for connecting to a database. These can be used to obtain information about the databases available on the system, the tables contained within each database and the data types used within any given ...
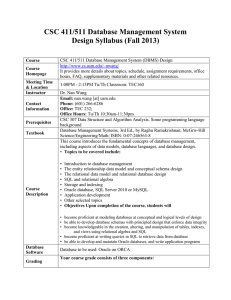
CSC 411/511 Database Management System Design Syllabus (Fall
... and views using relational algebra and SQL • become proficient at writing queries in SQL to retrieve data from database • be able to develop and maintain Oracle databases, and write application programs ...
... and views using relational algebra and SQL • become proficient at writing queries in SQL to retrieve data from database • be able to develop and maintain Oracle databases, and write application programs ...
Transferring data from a local database to a hosted
... Transferring data from a local database to a hosted database This guide is to help with transferring data between a local instance of MS SQL 2005 or 2008 to a database on one of our Shared or Dedicated MS SQL Servers. It is assumed that there is a shared database created, a local database and genera ...
... Transferring data from a local database to a hosted database This guide is to help with transferring data between a local instance of MS SQL 2005 or 2008 to a database on one of our Shared or Dedicated MS SQL Servers. It is assumed that there is a shared database created, a local database and genera ...
JDBC Interfaces
... OORDBMS systems • JDBC certification requires compliance with ANSI SQL-2 spec. • Initial support for access to ODBC through JDBC-ODBC bridge ...
... OORDBMS systems • JDBC certification requires compliance with ANSI SQL-2 spec. • Initial support for access to ODBC through JDBC-ODBC bridge ...
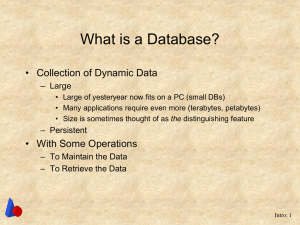
What is a Database? - Brigham Young University
... Traditional: e.g. Airline Res., Banking, Business Records Decision Support Design Knowledge and Scientific Multimedia Information Integration & Data Warehousing ...
... Traditional: e.g. Airline Res., Banking, Business Records Decision Support Design Knowledge and Scientific Multimedia Information Integration & Data Warehousing ...
my presentation at OWASP conference 2008
... 2. Code Injection: Code injection is process of inserting new SQL statements or database commands into the vulnerable SQL statement. One of the code injection attacks is to append a SQL Server EXECUTE command to the vulnerable SQL statement. This type of attack is only possible when multiple SQL sta ...
... 2. Code Injection: Code injection is process of inserting new SQL statements or database commands into the vulnerable SQL statement. One of the code injection attacks is to append a SQL Server EXECUTE command to the vulnerable SQL statement. This type of attack is only possible when multiple SQL sta ...
Using Data Access Objects (DAO)
... Using Active Objects (ADO) First convert your database to Access 97 by using Tools Database Utilities Convert Database To Access 97 Format. Next, start a Standard EXE project and ensure that in Project References you have Microsoft DAO 3.6 Object Library selected and pushed as far up as it w ...
... Using Active Objects (ADO) First convert your database to Access 97 by using Tools Database Utilities Convert Database To Access 97 Format. Next, start a Standard EXE project and ensure that in Project References you have Microsoft DAO 3.6 Object Library selected and pushed as far up as it w ...
Distributed Database
... if any site fails, it is not known by other users at other sites, their transaction goes on as usual ...
... if any site fails, it is not known by other users at other sites, their transaction goes on as usual ...
Tom Masciovecchio, Director of Publishing Systems
... All case studies and testimonials are at: http://www.microsoft.com/sql/migration/custevidence.mspx ...
... All case studies and testimonials are at: http://www.microsoft.com/sql/migration/custevidence.mspx ...
Database (db)
... What is a Database (db)? Database Management System (DBMS) is a software application/tool used by end users to access the data stored in the database files. A DBMS is also used to perform administrative tasks on the database and objects contained within the database. DBMS is a collection of app ...
... What is a Database (db)? Database Management System (DBMS) is a software application/tool used by end users to access the data stored in the database files. A DBMS is also used to perform administrative tasks on the database and objects contained within the database. DBMS is a collection of app ...