Lecture16_Databases
... Connecting Database Tables by Relationships • Student and Home_Base tables – Can have different security access restrictions • Access Home_Base data without having access to more sensitive data in Student ...
... Connecting Database Tables by Relationships • Student and Home_Base tables – Can have different security access restrictions • Access Home_Base data without having access to more sensitive data in Student ...
The Why and How of the iModernize(d) Application
... in an e-mail but making it appear to be a photo, for example. Neither of these two attacks can be done to software compiled as IBM i programs, because those operations are simply not allowed by the architecture. ...
... in an e-mail but making it appear to be a photo, for example. Neither of these two attacks can be done to software compiled as IBM i programs, because those operations are simply not allowed by the architecture. ...
AuditWizard v8 SQL Maintenance
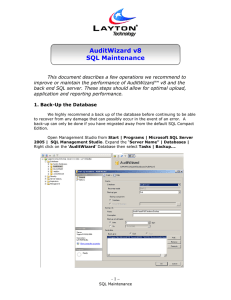
... the “General” page, choose a destination path and file name for the back up file, say ‘AuditWizard.bak’. If you intend to keep archives of the database, you may want to give the backup set a naming scheme with numbers or dates to show when it was backed up. This should also be performed for the ‘Tra ...
... the “General” page, choose a destination path and file name for the back up file, say ‘AuditWizard.bak’. If you intend to keep archives of the database, you may want to give the backup set a naming scheme with numbers or dates to show when it was backed up. This should also be performed for the ‘Tra ...
Page 1 of 3 COSC 2210 – Business Data
... Course Description: Study of relational database design techniques. Skills learned include relational table design, user interface design, and Visual Basic scripting. Microsoft Access, Microsoft SQL Server, and other relational databases will be used. Statement of Prerequisites: CMAP 1815, COSC 1010 ...
... Course Description: Study of relational database design techniques. Skills learned include relational table design, user interface design, and Visual Basic scripting. Microsoft Access, Microsoft SQL Server, and other relational databases will be used. Statement of Prerequisites: CMAP 1815, COSC 1010 ...
Data_Security
... extends to any other view, function, procedure or table owned by that object’s owner. No extra authority needs to be granted. ...
... extends to any other view, function, procedure or table owned by that object’s owner. No extra authority needs to be granted. ...
Document
... organization and processing in computer based-information systems. The emphasis in the course will be on the application of data management software for designing, creating, and manipulating databases. In the process, concepts involved in analysis, design, and administration of large databases will ...
... organization and processing in computer based-information systems. The emphasis in the course will be on the application of data management software for designing, creating, and manipulating databases. In the process, concepts involved in analysis, design, and administration of large databases will ...
ppt
... – Write special code to protect against system crashes – Optimize applications for efficient access and query – May often rewrite applications ...
... – Write special code to protect against system crashes – Optimize applications for efficient access and query – May often rewrite applications ...
GeoTools
... – Bridging the gap between raw data collection and the organization and sharing of data using previously developed products, services and standards(leveraging earlier work against new data providers) – Fostering a standardization of products and services via a common openly shared technical infrastr ...
... – Bridging the gap between raw data collection and the organization and sharing of data using previously developed products, services and standards(leveraging earlier work against new data providers) – Fostering a standardization of products and services via a common openly shared technical infrastr ...
Databases
... 4. A Record is a complete description of all of the fields related to one item in a table. ...
... 4. A Record is a complete description of all of the fields related to one item in a table. ...
บทที่ 6 ฐานข้อมูลและการสืบ
... characteristics of information, facilitate saving information in the database, update and search for information and designate rights to use the database so that users can get access to the information easily and effectively. It acts as the media between database users to communicate with each other ...
... characteristics of information, facilitate saving information in the database, update and search for information and designate rights to use the database so that users can get access to the information easily and effectively. It acts as the media between database users to communicate with each other ...
database
... subsystem that is responsible for recovery from hardware and software failures. For example, if the failure occurs in between the transaction, the DBMS recovery subsystem either reverts back the database to the state which existed prior to the start of the transaction or resumes the transaction ...
... subsystem that is responsible for recovery from hardware and software failures. For example, if the failure occurs in between the transaction, the DBMS recovery subsystem either reverts back the database to the state which existed prior to the start of the transaction or resumes the transaction ...
Chapter 4 Intro
... A bank account is a financial account between a bank customer and a financial institution. The financial institution, as represented by the branch, promised to maintain that account. It can happen that some branches have no accounts. A customer have many accounts, and an account is associated with ...
... A bank account is a financial account between a bank customer and a financial institution. The financial institution, as represented by the branch, promised to maintain that account. It can happen that some branches have no accounts. A customer have many accounts, and an account is associated with ...
Data Modeling
... • Performance: How fast can the DBMS access or update records? • Integration: Which operating system can it run under? • Features: Which security procedures or privacy policies are in place? • Vendor: Size and reputation of the vendor • Cost: Initial cost, maintenance costs, hardware costs, personne ...
... • Performance: How fast can the DBMS access or update records? • Integration: Which operating system can it run under? • Features: Which security procedures or privacy policies are in place? • Vendor: Size and reputation of the vendor • Cost: Initial cost, maintenance costs, hardware costs, personne ...
Data Modeling - Gonzaga University
... relatively stable, compared, for example, to the set of operational procedures or organizational structure, which changes frequently. • Therefore, basing the implementation of the future system upon a well-defined data model is a good first step towards developing a system that meets the real requir ...
... relatively stable, compared, for example, to the set of operational procedures or organizational structure, which changes frequently. • Therefore, basing the implementation of the future system upon a well-defined data model is a good first step towards developing a system that meets the real requir ...
September 2010 - NVidia GPU Technology Conference
... – Sequence data from the DBMS can be processed using GPU implementations • GPU sequence alignment implementations can exploit task parallelism and execute 10x (or more) faster than equivalent CPU implementations ...
... – Sequence data from the DBMS can be processed using GPU implementations • GPU sequence alignment implementations can exploit task parallelism and execute 10x (or more) faster than equivalent CPU implementations ...
Versant FastObjects .NET
... FastObjects .NET consists of a core database server that provides the essential database functionality, and a set of client-side application libraries used by your application. With FastObjects .NET, the database schema and all database access code are generated directly from the object model. This ...
... FastObjects .NET consists of a core database server that provides the essential database functionality, and a set of client-side application libraries used by your application. With FastObjects .NET, the database schema and all database access code are generated directly from the object model. This ...
Slide 1
... • Large amount of native Solaris tools to provide observability. • DTrace provides deeper observability to Solaris and your application. No other OS can do what DTrace does. > DTrace is a dynamic tracing framework that lets users turn on and off thousands of probe points inside the kernel and user a ...
... • Large amount of native Solaris tools to provide observability. • DTrace provides deeper observability to Solaris and your application. No other OS can do what DTrace does. > DTrace is a dynamic tracing framework that lets users turn on and off thousands of probe points inside the kernel and user a ...
Database
... Database Management System A database management system or DBMS consists of a group of programs that manipulate the data within a database. It provides an interface between the database and the user, or the database and application programs. ...
... Database Management System A database management system or DBMS consists of a group of programs that manipulate the data within a database. It provides an interface between the database and the user, or the database and application programs. ...
BWA Simulator 4.0
... Scalability: the client/server database architecture allows more than one user to concurrently access the database; all the accesses to the database are efficiently managed by the server; Security: Access control techniques can be implemented. Only authorized users can write the database; Server ...
... Scalability: the client/server database architecture allows more than one user to concurrently access the database; all the accesses to the database are efficiently managed by the server; Security: Access control techniques can be implemented. Only authorized users can write the database; Server ...
Slide 1
... Minimizing Data Redundancy and Data Inconsistency Eliminates the same data being stored in multiple files, thus reducing inconsistency in multiple versions of the same data. ...
... Minimizing Data Redundancy and Data Inconsistency Eliminates the same data being stored in multiple files, thus reducing inconsistency in multiple versions of the same data. ...
Field name Data Type
... data is stored in several tables with links between the tables to enable the data in the separate tables to be combined together if needed. c Describe an application where a flat-file database would be suitable. use to simple data storage and retrieval systems such as storing a list of names, addres ...
... data is stored in several tables with links between the tables to enable the data in the separate tables to be combined together if needed. c Describe an application where a flat-file database would be suitable. use to simple data storage and retrieval systems such as storing a list of names, addres ...
Chapter 1
... Describes how the data is stored in the database. Schema and Instances The overall description of the database is called the schema. There are three different types of schema, external, conceptual and internal. The data at any particular point in time is called the database ...
... Describes how the data is stored in the database. Schema and Instances The overall description of the database is called the schema. There are three different types of schema, external, conceptual and internal. The data at any particular point in time is called the database ...
Standards and Macros: The Keystroke Busters!
... Our group has many macros that we use all the time, too numerous to present in one paper. I have shown you the ones that are very common and straightforward. Hopefully, I have convinced you that by establishing standards and naming conventions-and adheringtothem-prograrnmers can develop generic macr ...
... Our group has many macros that we use all the time, too numerous to present in one paper. I have shown you the ones that are very common and straightforward. Hopefully, I have convinced you that by establishing standards and naming conventions-and adheringtothem-prograrnmers can develop generic macr ...
Quiz 1 Review Slides
... • Partial credit: if less than half the class gets a question right, he’ll give half-credit for the next best answer • Not easy! ...
... • Partial credit: if less than half the class gets a question right, he’ll give half-credit for the next best answer • Not easy! ...