Enterprise Data Auditing with Lumigent® Entegra™
... Unimpeachable audit trail Meets audit requirements Segregation of duties Separation of audit system Audits privileged users ...
... Unimpeachable audit trail Meets audit requirements Segregation of duties Separation of audit system Audits privileged users ...
Open-source analytics development
... • Major outstanding need: to establish a community of individuals based on shared attitudes, interests and goals where everyone has equal opportunity to participate and contribute ...
... • Major outstanding need: to establish a community of individuals based on shared attitudes, interests and goals where everyone has equal opportunity to participate and contribute ...
Building a Data Warehouse With SAS Software in the UNIX Environment
... allows easy access to the database, freeing all users from the need to know the details of the database implementation. This ease of access makes it possible to allow non-technical users to utilize the data warehouse. Efforts are currently underway to build an application that will give users point- ...
... allows easy access to the database, freeing all users from the need to know the details of the database implementation. This ease of access makes it possible to allow non-technical users to utilize the data warehouse. Efforts are currently underway to build an application that will give users point- ...
Introduction “Structured Query Language” (SQL)
... – Effective use also requires knowledge of the underlying fields and tables ...
... – Effective use also requires knowledge of the underlying fields and tables ...
CGI
... Overview • A plain HTML document is static • A CGI program is executed in real-time, so that it can output dynamic information. • CGI (Common Gateway Interface) is the language or protocol that the browser uses to communicate the data from the form to the web server. • A standard for interfacing ex ...
... Overview • A plain HTML document is static • A CGI program is executed in real-time, so that it can output dynamic information. • CGI (Common Gateway Interface) is the language or protocol that the browser uses to communicate the data from the form to the web server. • A standard for interfacing ex ...
Database Security: What Students Need to Know
... down in the United States to three perpetrators accused of carrying out the single largest data security breach recorded to date. These hackers allegedly stole over 130 million credit and debit card numbers by exploiting a well known database vulnerability, a SQL injection (Phifer, 2010). The Verizo ...
... down in the United States to three perpetrators accused of carrying out the single largest data security breach recorded to date. These hackers allegedly stole over 130 million credit and debit card numbers by exploiting a well known database vulnerability, a SQL injection (Phifer, 2010). The Verizo ...
MayBMS: A Probabilistic Database Management System
... They are available at the MayBMS website. We next discuss an implemented application for risk management in the human resources space, in the context of basketball. Using PHP, we have built on top of MayBMS a web-based application that offers NBA-related decision support functionality based on what- ...
... They are available at the MayBMS website. We next discuss an implemented application for risk management in the human resources space, in the context of basketball. Using PHP, we have built on top of MayBMS a web-based application that offers NBA-related decision support functionality based on what- ...
2008-2009 Assessment for the Computer Science Degree Program
... 66% 84% Program Objective #5 (PO5): Students will demonstrate knowledge and understanding of professional ethics and responsible behavior, and will develop strong communication skills. Assessment will be measured through testing the following course objectives: CSCI 251 Introduction to Information S ...
... 66% 84% Program Objective #5 (PO5): Students will demonstrate knowledge and understanding of professional ethics and responsible behavior, and will develop strong communication skills. Assessment will be measured through testing the following course objectives: CSCI 251 Introduction to Information S ...
Who Dares Wins – SQL Server Consolidation in the Cloud
... Managed backup Granular control of the backup schedule Local staging support for faster recovery and resilient to transient network issues Support for system databases Supports simple recovery mode Hybrid solutions ...
... Managed backup Granular control of the backup schedule Local staging support for faster recovery and resilient to transient network issues Support for system databases Supports simple recovery mode Hybrid solutions ...
16 Java Database Connectivity
... Row Set A JDBC RowSet object holds tabular data in a way that makes it more flexible and easier to use than a result set. A Row Set is an object which encapsulates a set of rows. Kinds of RowSet Objects Connected RowSet object uses a driver based on JDBC technology (“JDBC Driver”) to make a connect ...
... Row Set A JDBC RowSet object holds tabular data in a way that makes it more flexible and easier to use than a result set. A Row Set is an object which encapsulates a set of rows. Kinds of RowSet Objects Connected RowSet object uses a driver based on JDBC technology (“JDBC Driver”) to make a connect ...
Database Security and Auditing: Protecting Data Integrity and
... _____________________________ is a collection of security policies and procedures, data constraints, security methods, and security tools blended together to implement all necessary measures to secure the integrity, accessibility, and confidentiality of every component of the database environment. ...
... _____________________________ is a collection of security policies and procedures, data constraints, security methods, and security tools blended together to implement all necessary measures to secure the integrity, accessibility, and confidentiality of every component of the database environment. ...
Database Engines on Multicores Scale
... Sessions proceed by interacting with the transaction manager for executing the statement in isolation (line 19 of Figure 2). Both engines provide different isolation levels, offering lock based or multi-version schemes. For simplicity reasons we will focus on lock-based ones. For lock schemes, both ...
... Sessions proceed by interacting with the transaction manager for executing the statement in isolation (line 19 of Figure 2). Both engines provide different isolation levels, offering lock based or multi-version schemes. For simplicity reasons we will focus on lock-based ones. For lock schemes, both ...
FastStats - Creativ Direkt
... → Building FastStats databases • Graphical Extract, Transform and Load tool for configuring and loading FastStats systems. • You can build FastStats system with just a few mouse clicks OR we can help you to structure your marketing databases into FastStats system. • It could connect to all standard ...
... → Building FastStats databases • Graphical Extract, Transform and Load tool for configuring and loading FastStats systems. • You can build FastStats system with just a few mouse clicks OR we can help you to structure your marketing databases into FastStats system. • It could connect to all standard ...
Moving Object Databases — Dynamic Flight Route
... represents an object’s location in space. Examples of point objects are airports, cities. A line is the basic type for moving through space or junctions in space. Examples of line objects are a route of a plane, a borderline of a country. Lastly, a region is the type for an entity having an area in ...
... represents an object’s location in space. Examples of point objects are airports, cities. A line is the basic type for moving through space or junctions in space. Examples of line objects are a route of a plane, a borderline of a country. Lastly, a region is the type for an entity having an area in ...
catalog Optimization Logical Expression
... - e.g. Exhaustively considering join ordering: alternatives are exponential ...
... - e.g. Exhaustively considering join ordering: alternatives are exponential ...
MSSE
... This course introduces the object-oriented methodology in detail on UNIX-like platform. High level OOP concepts such as abstract data types, encapsulation, inheritance, polymorphism, and template will be covered. Various UNIX tools will be used in the class. Participants study examples using object- ...
... This course introduces the object-oriented methodology in detail on UNIX-like platform. High level OOP concepts such as abstract data types, encapsulation, inheritance, polymorphism, and template will be covered. Various UNIX tools will be used in the class. Participants study examples using object- ...
Test Driven Development and Automated Unit Testing in
... to a commercial .Net application framework Member of a team submitting a response to the OMG request for a method for formalizing business rules XSLT transformations from ORM conceptual models into .NET entity business object implementation ...
... to a commercial .Net application framework Member of a team submitting a response to the OMG request for a method for formalizing business rules XSLT transformations from ORM conceptual models into .NET entity business object implementation ...
Queries - DePaul QRC
... Let’s create a form for our Real Estate database, for the Listings table Download the Real Estate database to the desktop and unzip the file ...
... Let’s create a form for our Real Estate database, for the Listings table Download the Real Estate database to the desktop and unzip the file ...
Running SQL Scripts
... There is a number of ways to run SQL scripts (i.e. the statements in SQL files). So you can always choose the way that suits you best. Running an SQL script without opening the database console Running SQL statements by means of an intention action Running SQL statements as in the database console R ...
... There is a number of ways to run SQL scripts (i.e. the statements in SQL files). So you can always choose the way that suits you best. Running an SQL script without opening the database console Running SQL statements by means of an intention action Running SQL statements as in the database console R ...
adbms tutorial 2 lahore leads university
... and use AUTO_INCREMENT for the rest of records by inserting a NULL, or with a missing column value. Take note that strings must be enclosed with a pair of single quotes (or double quotes). -- Insert a row with all the column values mysql> INSERT INTO products VALUES (1001, 'PEN', 'Pen Red', 5000, 1. ...
... and use AUTO_INCREMENT for the rest of records by inserting a NULL, or with a missing column value. Take note that strings must be enclosed with a pair of single quotes (or double quotes). -- Insert a row with all the column values mysql> INSERT INTO products VALUES (1001, 'PEN', 'Pen Red', 5000, 1. ...
Randtronics Data Privacy Manager
... DPM File allows users to secure files, folders, applications and databases in a Windows or Linux environment. The software is designed so that end users do not need to change their behaviour in order to secure their files. The product has the following features: ...
... DPM File allows users to secure files, folders, applications and databases in a Windows or Linux environment. The software is designed so that end users do not need to change their behaviour in order to secure their files. The product has the following features: ...
Bioinformatics Data Representation and
... INSERT INTO features VALUES ( 'NG_002690[1..174707]', 'AC090602.16' ); INSERT INTO features VALUES ( 'NG_002690[174707..324834]', 'AC124312.5' ); INSERT INTO features VALUES ( 'NG_002690[324835..478258]', 'AC124303.5' ); INSERT INTO features VALUES ( 'NG_002690[478259..606120]', 'AC100774.2' ); INSE ...
... INSERT INTO features VALUES ( 'NG_002690[1..174707]', 'AC090602.16' ); INSERT INTO features VALUES ( 'NG_002690[174707..324834]', 'AC124312.5' ); INSERT INTO features VALUES ( 'NG_002690[324835..478258]', 'AC124303.5' ); INSERT INTO features VALUES ( 'NG_002690[478259..606120]', 'AC100774.2' ); INSE ...
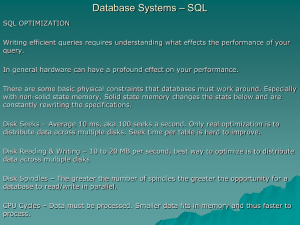
Optimizing SQL
... Problem: The planner has decided its faster to do a table scan than an index scan : This can happen if a) your table is relatively small, or the field you are indexing has a lot of duplicates. Solution: Case in point, boolean fields are not terribly useful to index since 50% of your data is one thin ...
... Problem: The planner has decided its faster to do a table scan than an index scan : This can happen if a) your table is relatively small, or the field you are indexing has a lot of duplicates. Solution: Case in point, boolean fields are not terribly useful to index since 50% of your data is one thin ...