IBM Database Conversion Workbench 2.0 Oracle to DB2 Conversion Guide IBM Software
... © Copyright IBM Corp. 2013. All rights reserved ...
... © Copyright IBM Corp. 2013. All rights reserved ...
ACCESS Chapter 4
... Objective: to import an Access table from an Excel workbook; create a one-to-many relationship, and create a multiple-table query ...
... Objective: to import an Access table from an Excel workbook; create a one-to-many relationship, and create a multiple-table query ...
PowerCenter 9.x: Developer, Level 2
... Explain types of data type conversion: port-to-port, expression-to-port, and explicit Identify which transformations increase or decrease the number of rows Explain the performance implications of the Stored Procedure vs. the SQL transformation ...
... Explain types of data type conversion: port-to-port, expression-to-port, and explicit Identify which transformations increase or decrease the number of rows Explain the performance implications of the Stored Procedure vs. the SQL transformation ...
Query Engine
... A Query Engine handles the individual features and limitations of each data source involved while processing search requests and creating native query statements. It may also translate ref erences to a domain model into references to a data model. A Query Engine might be built as a reusable compone ...
... A Query Engine handles the individual features and limitations of each data source involved while processing search requests and creating native query statements. It may also translate ref erences to a domain model into references to a data model. A Query Engine might be built as a reusable compone ...
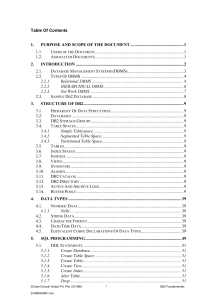
3. Structure Of DB2
... parent supplier. Each tree can be called a supplier record occurrence. Similarly you can see part record occurrence and shipment record occurrence. Shipment database contains the shipment quantity. The logical child of shipment database consists of supplier number , part number and pointers to cor ...
... parent supplier. Each tree can be called a supplier record occurrence. Similarly you can see part record occurrence and shipment record occurrence. Shipment database contains the shipment quantity. The logical child of shipment database consists of supplier number , part number and pointers to cor ...
2160707 - Advanced Java - Darshan Institute of Engineering
... interface cannot accept parameters. Use when you plan to use the SQL statements many times. The PreparedStatement interface accepts input parameters at runtime. Use when you want to access database stored procedures. The CallableStatement interface can also accept runtime input parameters. Table 2.2 ...
... interface cannot accept parameters. Use when you plan to use the SQL statements many times. The PreparedStatement interface accepts input parameters at runtime. Use when you want to access database stored procedures. The CallableStatement interface can also accept runtime input parameters. Table 2.2 ...
Oracle Database 11g Family
... All four editions of Oracle Database 11g are built using the same reliable database engine architecture and are completely compatible with each other. They are also available on a choice of operating systems and include a common set of application development tools and programming interfaces. Using ...
... All four editions of Oracle Database 11g are built using the same reliable database engine architecture and are completely compatible with each other. They are also available on a choice of operating systems and include a common set of application development tools and programming interfaces. Using ...
JDBC
... JDBC - queries • A result set object has a cursor, which points to a specific row in the set • The cursor can be moved in the result set, by calling certain methods • For instance the next() method – Returns a boolean value (any more rows?) – Advances the cursor one row ...
... JDBC - queries • A result set object has a cursor, which points to a specific row in the set • The cursor can be moved in the result set, by calling certain methods • For instance the next() method – Returns a boolean value (any more rows?) – Advances the cursor one row ...
Achieving Efficient Query Privacy for Location Based Services*
... Location cloaking in general seeks to prevent an attacker from being able to match queries to particular users and to thus compromise their privacy. The attacker may be in a position to observe traffic flowing through the network or even be situated at the LBS provider endpoint. One popular cloaking ...
... Location cloaking in general seeks to prevent an attacker from being able to match queries to particular users and to thus compromise their privacy. The attacker may be in a position to observe traffic flowing through the network or even be situated at the LBS provider endpoint. One popular cloaking ...
Oracle Migration Workbench Reference Guide for Microsoft SQL
... Oracle Migration Workbench Reference Guide for Microsoft SQL Server and Sybase Adaptive Server Migrations, Release 9.2.0 for Microsoft Windows 98/2000 and Microsoft Windows NT. Part Number: A97248-01 Copyright © 1998, 2002 Oracle Corporation. All rights reserved. The Programs (which include both th ...
... Oracle Migration Workbench Reference Guide for Microsoft SQL Server and Sybase Adaptive Server Migrations, Release 9.2.0 for Microsoft Windows 98/2000 and Microsoft Windows NT. Part Number: A97248-01 Copyright © 1998, 2002 Oracle Corporation. All rights reserved. The Programs (which include both th ...
Chapter 1: Introduction
... Allows the specification of not only a set of relations but also information about each relation, including: The schema for each relation. The domain of values associated with each attribute. Integrity constraints Security and authorization information for each relation. The set of indices ...
... Allows the specification of not only a set of relations but also information about each relation, including: The schema for each relation. The domain of values associated with each attribute. Integrity constraints Security and authorization information for each relation. The set of indices ...
Generating Program Inputs for Database Application Testing
... query’s concrete string and its abstract form, symbolic expressions of program variables, and path conditions) collected by DSE. There are two major challenges here. First, program input values are often combined into the executed query after a chain of computations. In our illustrative example, we ...
... query’s concrete string and its abstract form, symbolic expressions of program variables, and path conditions) collected by DSE. There are two major challenges here. First, program input values are often combined into the executed query after a chain of computations. In our illustrative example, we ...
Understanding SAS/ACCESS® Software's Role with Querying and Reporting in a Business Intelligence Environment
... Sometimes, SAS® software users encounter errors when they use business intelligence (BI) clients to query database tables. For example, a user who queries an Oracle table using SAS® Enterprise Guide® or the SAS® Add-In for Microsoft Office might receive an error that indicates that the data file can ...
... Sometimes, SAS® software users encounter errors when they use business intelligence (BI) clients to query database tables. For example, a user who queries an Oracle table using SAS® Enterprise Guide® or the SAS® Add-In for Microsoft Office might receive an error that indicates that the data file can ...
RDF Parser/Serializer
... Based on the relational algebra of Look more like statements in predicate joins and foreign key references calculus Unification variables are used to express constraints between the patterns Describes a new data table that is Describe a new graph that is formed by formed by combining two or describi ...
... Based on the relational algebra of Look more like statements in predicate joins and foreign key references calculus Unification variables are used to express constraints between the patterns Describes a new data table that is Describe a new graph that is formed by formed by combining two or describi ...
Chapter 10
... • Transaction log keeps track of all transactions that modify database • Concurrency control coordinates simultaneous execution of transactions • Scheduler is responsible for establishing order in which concurrent transaction operations are executed ...
... • Transaction log keeps track of all transactions that modify database • Concurrency control coordinates simultaneous execution of transactions • Scheduler is responsible for establishing order in which concurrent transaction operations are executed ...
Document
... • Assigning a query to an IEnumerable
variable doesn’t execute the query
• When user iterates over members of the
collection, each query operator executes as
many times as needed to retrieve the next
element
– Hence the data can change while elements are still
being retrieved
...
... • Assigning a query to an IEnumerable
Architecture of Transaction Processing Systems
... number of client requests might be pending at the same time. Hence, the application server must handle requests concurrently in order to maintain an adequate level of performance. It might do this by allocating a process for each user. Unfortunately, processes carry substantial overhead, and thus th ...
... number of client requests might be pending at the same time. Hence, the application server must handle requests concurrently in order to maintain an adequate level of performance. It might do this by allocating a process for each user. Unfortunately, processes carry substantial overhead, and thus th ...
Mājas Darbs #2 Rezultāti
... Controls – define control channel for rndc control utility. Include - can be used to merge a lot of configuration file in one. Key – use information to check identity using TSIG technology. Logging – use to control logging options of DNS server. Options - different DNS server options. Use mainly for ...
... Controls – define control channel for rndc control utility. Include - can be used to merge a lot of configuration file in one. Key – use information to check identity using TSIG technology. Logging – use to control logging options of DNS server. Options - different DNS server options. Use mainly for ...
Parallel Databases
... Shared-nothing multiprocessors can be scaled up to thousands of processors without interference. Main drawback: cost of communication and non-local disk access; sending data involves software interaction ...
... Shared-nothing multiprocessors can be scaled up to thousands of processors without interference. Main drawback: cost of communication and non-local disk access; sending data involves software interaction ...