Powerpoint
... Enable SNAPSHOT isolation in the source database Or create a source snapshot database ...
... Enable SNAPSHOT isolation in the source database Or create a source snapshot database ...
USE-FOR-IGRAPH-_-Performance-Analysis-Review
... Managing poor performance, migrating databases into cost effective cloud environments, increased maintenance and software investment are all problems challenging IT budgets. These may be due to the following possible reasons: ...
... Managing poor performance, migrating databases into cost effective cloud environments, increased maintenance and software investment are all problems challenging IT budgets. These may be due to the following possible reasons: ...
Advanced Programming JDBC
... Based on adapters (drivers) between the client and the DBMS java.sql – the core JDBC API ...
... Based on adapters (drivers) between the client and the DBMS java.sql – the core JDBC API ...
Blind SQL Injection - Biblioteca [Blackploit]
... isolate the web application from SQL altogether. All SQL statements required by the application should be in stored procedures and kept on the database server. The application should execute the stored procedures using a safe interface such as JDBC’s CallableStatement or ADO’s Command Object. If arb ...
... isolate the web application from SQL altogether. All SQL statements required by the application should be in stored procedures and kept on the database server. The application should execute the stored procedures using a safe interface such as JDBC’s CallableStatement or ADO’s Command Object. If arb ...
CS352 Lecture - Commercial Query Languages: SQL, QBE last
... (3) It is also possible for any system that has the db2 JDBC driver installed to access the database via JDBC - for example, this is the case with my laptop. The JDBC driver is written in Java, and hence runs on any system that runs Java - it does not have to be running db2. For a JDBC connection, ...
... (3) It is also possible for any system that has the db2 JDBC driver installed to access the database via JDBC - for example, this is the case with my laptop. The JDBC driver is written in Java, and hence runs on any system that runs Java - it does not have to be running db2. For a JDBC connection, ...
SQL Server 7.0 Strategy Deck
... What if it was both a general purpose proc and embedded on disk controller? ...
... What if it was both a general purpose proc and embedded on disk controller? ...
SELECT Statements in PL/SQL
... allocated by the Oracle server. There are two types of cursors: – Implicit cursors: Created and managed internally by the Oracle server to process SQL statements – Explicit cursors: Explicitly declared by the ...
... allocated by the Oracle server. There are two types of cursors: – Implicit cursors: Created and managed internally by the Oracle server to process SQL statements – Explicit cursors: Explicitly declared by the ...
- TehraTechnologies
... VT has decided to let students take copies and printouts up to a certain limit. This database holds the current number of copies and printouts taken by each student identified with the unique pid field 4) Schema management Module: This module manages the schema of the database spreaded across in all ...
... VT has decided to let students take copies and printouts up to a certain limit. This database holds the current number of copies and printouts taken by each student identified with the unique pid field 4) Schema management Module: This module manages the schema of the database spreaded across in all ...
Insert Title Here
... – Atomicity: a transaction is executed completely or not at all – Consistency: a transaction creates a new consistent DB state, i.e., in which all integrity constraints are maintained – Isolation: to the user, a transaction seems to run in isolation – Durability: the effect of a successful (“committ ...
... – Atomicity: a transaction is executed completely or not at all – Consistency: a transaction creates a new consistent DB state, i.e., in which all integrity constraints are maintained – Isolation: to the user, a transaction seems to run in isolation – Durability: the effect of a successful (“committ ...
CIS 8040 – Fundamentals of Database Management Systems
... Class sessions will comprise (1) lecture/discussion of certain database software concepts and features, (2) instructor demonstrations of these same database software concepts and features, and (3) student lab sessions working with these same database software concepts and features. The purpose of th ...
... Class sessions will comprise (1) lecture/discussion of certain database software concepts and features, (2) instructor demonstrations of these same database software concepts and features, and (3) student lab sessions working with these same database software concepts and features. The purpose of th ...
Mirroring at Baker Hostetler
... • Witness can be SQL Express • Mirror server can be unlicensed – as long as you do not have anything running queries against the instance. • No snapshots allowed. • See SQL Licensing White paper for more details ...
... • Witness can be SQL Express • Mirror server can be unlicensed – as long as you do not have anything running queries against the instance. • No snapshots allowed. • See SQL Licensing White paper for more details ...
Outline of topics covered in the SQL fundamental series
... Prepared by Jennifer Kreie, Associate Professor Accounting & Information Systems Department College of Business, New Mexico State University The purpose of this set of Power Point slides and videos is to introduce SQL fundamentals using the Oracle database software and Oracle’s SQL Developer as the ...
... Prepared by Jennifer Kreie, Associate Professor Accounting & Information Systems Department College of Business, New Mexico State University The purpose of this set of Power Point slides and videos is to introduce SQL fundamentals using the Oracle database software and Oracle’s SQL Developer as the ...
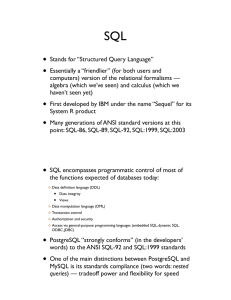
• Stands for “Structured Query Language” • Essentially a “friendlier
... psql: Enters a command-line SQL environment that is “connected” to some logical database as some database user programming interfaces (embedded SQL, dynamic SQL, ODBC, JDBC, etc.): Provides access to the SQL environment from assorted general-purpose programming languages and platforms SQL statements ...
... psql: Enters a command-line SQL environment that is “connected” to some logical database as some database user programming interfaces (embedded SQL, dynamic SQL, ODBC, JDBC, etc.): Provides access to the SQL environment from assorted general-purpose programming languages and platforms SQL statements ...
outline
... 1) Full in-memory object model with bulk updates a. Load object model from disk at startup b. Application features run off of in-memory object model c. Save object model to disk in bulk at appropriate times (e.g., user “Save”, app exit) d. Crash causes data loss e. Complete in-memory model and bulk ...
... 1) Full in-memory object model with bulk updates a. Load object model from disk at startup b. Application features run off of in-memory object model c. Save object model to disk in bulk at appropriate times (e.g., user “Save”, app exit) d. Crash causes data loss e. Complete in-memory model and bulk ...
Lecture 19
... the encryption keys in a security module (that is, a wallet) external to the database. Protecting data from this type of theft is required for most compliance regulations. The benefit to using transparent data encryption is that it requires little coding and is quick and easy to implement. ...
... the encryption keys in a security module (that is, a wallet) external to the database. Protecting data from this type of theft is required for most compliance regulations. The benefit to using transparent data encryption is that it requires little coding and is quick and easy to implement. ...
An Unexpected Journey: SQL Server 2000 to 2014
... upgrade Model database check & test server-level properties ...
... upgrade Model database check & test server-level properties ...
Using SAS with a SQL Server Database
... either Windows NT® or SQL Server authentication, but must match the ones used to establish the ODBC data source. For multi-user systems, each station must be configured with its own ODBC connection, and if Windows NT authentication is used, it is important to make sure that all users have access to ...
... either Windows NT® or SQL Server authentication, but must match the ones used to establish the ODBC data source. For multi-user systems, each station must be configured with its own ODBC connection, and if Windows NT authentication is used, it is important to make sure that all users have access to ...
Link to Slides
... over some form of network to bring down the cost or the difficulty in accessing data and to increase the efficiency of the whole system. The software that runs it is called a Distributed Database Management ...
... over some form of network to bring down the cost or the difficulty in accessing data and to increase the efficiency of the whole system. The software that runs it is called a Distributed Database Management ...
ppt
... • Do as few calls as possible over the net • Prefer asynchronous approaches – problem: success/failure indications – send lots of stuff, then synchronize ...
... • Do as few calls as possible over the net • Prefer asynchronous approaches – problem: success/failure indications – send lots of stuff, then synchronize ...
SQL Server 2016 and Power BI Presentation Materials
... Row-Level Security (RLS) simplifies the design and coding of security in your applications. RLS enables you to transparently implement restrictions on data row access by user at the data tier. ...
... Row-Level Security (RLS) simplifies the design and coding of security in your applications. RLS enables you to transparently implement restrictions on data row access by user at the data tier. ...
IS 331-Spring 2017 - Information Systems
... Course Description: Businesses use databases extensively for analysis and decision-making because they provide efficient, large-scale information storage and rapid retrieval. Databases support the "back end functionality" of most large web systems. This course gives students extensive, pragmatic exp ...
... Course Description: Businesses use databases extensively for analysis and decision-making because they provide efficient, large-scale information storage and rapid retrieval. Databases support the "back end functionality" of most large web systems. This course gives students extensive, pragmatic exp ...
Power Point - Arizona State University
... Support the relational data model Use SQL as the primary mechanism for application interaction ACID support for transactions A non-locking concurrency control mechanism so real-time reads will not conflict with writes, and thereby cause them to stall 5. A scale-out, shared-nothing architecture, capa ...
... Support the relational data model Use SQL as the primary mechanism for application interaction ACID support for transactions A non-locking concurrency control mechanism so real-time reads will not conflict with writes, and thereby cause them to stall 5. A scale-out, shared-nothing architecture, capa ...



![Blind SQL Injection - Biblioteca [Blackploit]](http://s1.studyres.com/store/data/007760495_1-5008242d679a28d527046b664a8c2177-300x300.png)