Introduction to Database Systems - Chen Li -
... What attributes are unique (i.e., identify their associated entity instances)? What are the rules about (the much coveted) parking passes? What are the rules (constraints) about professors being in departments? And, what are the rules about professors heading departments? ...
... What attributes are unique (i.e., identify their associated entity instances)? What are the rules about (the much coveted) parking passes? What are the rules (constraints) about professors being in departments? And, what are the rules about professors heading departments? ...
Configuring the Apache web server
... It’s desirable that the data cache should include the major data amount used by the product. For the proper database functioning, about 60-80% of free memory are usually allocated in the system. It’s also recommended to perform MySQL multithreading. Note for administrators. Converting data to InnoDB ...
... It’s desirable that the data cache should include the major data amount used by the product. For the proper database functioning, about 60-80% of free memory are usually allocated in the system. It’s also recommended to perform MySQL multithreading. Note for administrators. Converting data to InnoDB ...
AlwaysOn Design Patterns and Lessons Learned.ppt
... • With SQL Server 2012 and AGs, it is a single Windows cluster spanning the two sites, instead of a different Windows cluster at each site. • NOTE: Asymmetric Storage requires Windows Server 2008 R2 + SP1 or QFE’s ...
... • With SQL Server 2012 and AGs, it is a single Windows cluster spanning the two sites, instead of a different Windows cluster at each site. • NOTE: Asymmetric Storage requires Windows Server 2008 R2 + SP1 or QFE’s ...
Data/Application integration
... Replication performance has been significantly boosted in IBM i environments. The replication queues have been rearchitected in order to minimize the performance impact of Share replication, and multiple change selectors can now be configured in a replication model. Support for IBM i 7.2, IBM’s late ...
... Replication performance has been significantly boosted in IBM i environments. The replication queues have been rearchitected in order to minimize the performance impact of Share replication, and multiple change selectors can now be configured in a replication model. Support for IBM i 7.2, IBM’s late ...
Chap.14
... – Also known as a data source – Represents the data management application • Used to store data generated by an application program ...
... – Also known as a data source – Represents the data management application • Used to store data generated by an application program ...
Exam Discussion-AIC
... • Will each topic contain questions from all subjects mentioned in the title? – No. They represent the pool of information from which questions are asked. See also last year’s exam. ...
... • Will each topic contain questions from all subjects mentioned in the title? – No. They represent the pool of information from which questions are asked. See also last year’s exam. ...
week 3 normalisation
... Data per taining to the publisher is extracted and held in a dif ferent table. This allows the data to be maintained separately If name changes, address moves etc you update the PUBLISHER table rather than every single record affected in the book table. ...
... Data per taining to the publisher is extracted and held in a dif ferent table. This allows the data to be maintained separately If name changes, address moves etc you update the PUBLISHER table rather than every single record affected in the book table. ...
Module #4 - Высшая школа экономики
... business intelligence tools and XML, which will prove to be invaluable as them progress further in computer science studies. This course studies different database models and their properties. The models that will be discussed are: ...
... business intelligence tools and XML, which will prove to be invaluable as them progress further in computer science studies. This course studies different database models and their properties. The models that will be discussed are: ...
University at Buffalo Combining Keyword Search and Forms for Ad Hoc
... way without the requirement of knowledge of building structural queries. It describes a method where the system makes use of forms to input required parameters and build queries which are later sent to the database to get back the results. The forms are presented based on an initial set of keywords ...
... way without the requirement of knowledge of building structural queries. It describes a method where the system makes use of forms to input required parameters and build queries which are later sent to the database to get back the results. The forms are presented based on an initial set of keywords ...
TRUNCATE TABLE
... log, going from the last checkpoint to the point at which the server was shut down or failed. Committed transactions that have not been written to the database are rolled forward and written to the database. Uncommitted transactions are rolled back and not written to the database. ...
... log, going from the last checkpoint to the point at which the server was shut down or failed. Committed transactions that have not been written to the database are rolled forward and written to the database. Uncommitted transactions are rolled back and not written to the database. ...
Table Names and Properties
... Therefore, the indexes are defined so as to optimize the processing of SELECT statements. ; an index is never explicitly referenced in a SELECT statement; the syntax of SQL does not allow this; during the processing of a statement, SQL itself determines whether an existing index will be used; ...
... Therefore, the indexes are defined so as to optimize the processing of SELECT statements. ; an index is never explicitly referenced in a SELECT statement; the syntax of SQL does not allow this; during the processing of a statement, SQL itself determines whether an existing index will be used; ...
Wrapping Relational Data Model to Object
... SOFSEM-SRF 2006, January 21-26, Merin, Czech Republic ...
... SOFSEM-SRF 2006, January 21-26, Merin, Czech Republic ...
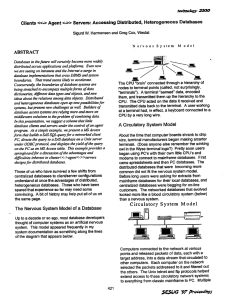
Clients <<-> Agent <->> Servers: Accessing Distributed, Heterogeneous Databases
... Databases in thefoture will certainly become more widely distributed across applications and platforms. Even now we are seeing on intranets and the Internet a surge in database implementations that cross DBMS and system boundaries. That trend seems likely to accelerate. Concurrently, the boundaries ...
... Databases in thefoture will certainly become more widely distributed across applications and platforms. Even now we are seeing on intranets and the Internet a surge in database implementations that cross DBMS and system boundaries. That trend seems likely to accelerate. Concurrently, the boundaries ...
SNS COLLEGE OF ENGINEERING ,COIMBATORE - 107
... An understanding of the context, phases and techniques for designing and building database information systems in business. An understanding of the components of a computerized database information system (application). An ability to correctly use the techniques, components and tools of a typica ...
... An understanding of the context, phases and techniques for designing and building database information systems in business. An understanding of the components of a computerized database information system (application). An ability to correctly use the techniques, components and tools of a typica ...
WebSecurity
... This application implements basic security in which the authenticated user has access to one or more application roles. There are three database tables to implement the role-based security. ...
... This application implements basic security in which the authenticated user has access to one or more application roles. There are three database tables to implement the role-based security. ...
SQL 1. What are the types of SQL statement? Data Manipulation
... reaches its MAXVALUE, it will start over at the MINVALUE. This is not wise if using the sequence for primary key creation. When you create a sequence with NOCYCLE option, you are saying that when the sequence reaches its MAXVALUE, it will NOT start over at the MINVALUE. This option is safest if usin ...
... reaches its MAXVALUE, it will start over at the MINVALUE. This is not wise if using the sequence for primary key creation. When you create a sequence with NOCYCLE option, you are saying that when the sequence reaches its MAXVALUE, it will NOT start over at the MINVALUE. This option is safest if usin ...
The Relational Model - inst.eecs.berkeley.edu
... a history of the account •Figures out the best way to answer a question -> There is always nore than 1 way to skin a cat…! •Provides generic ways to combine data ...
... a history of the account •Figures out the best way to answer a question -> There is always nore than 1 way to skin a cat…! •Provides generic ways to combine data ...
jdbc
... Guide (3rd ed) 1999 Ch.11 p.237-249 • www.javasoft.com • Orfali, R. and Harkey, D (1998) Client/Server Programming with JAVA and CORBA (2nd Ed.) Wiley Ch. 23, 25 ...
... Guide (3rd ed) 1999 Ch.11 p.237-249 • www.javasoft.com • Orfali, R. and Harkey, D (1998) Client/Server Programming with JAVA and CORBA (2nd Ed.) Wiley Ch. 23, 25 ...
CH1 - Favorite
... PHP includes strengths of relatively older languages, such as Perl and Tcl, and does away their weaknesses. Although it is known for its advanced features, its fundamental features should be considered first. The advanced features of PHP will be discussed later in the chapter under the topic “PHP ...
... PHP includes strengths of relatively older languages, such as Perl and Tcl, and does away their weaknesses. Although it is known for its advanced features, its fundamental features should be considered first. The advanced features of PHP will be discussed later in the chapter under the topic “PHP ...
ADBC_plugin.pdf
... and methods for connecting to a database. These can be used to obtain information about the databases available on the system, the tables contained within each database and the data types used within any given table. More importantly, JavaScript can be used to execute SQL commands and retrieve data, ...
... and methods for connecting to a database. These can be used to obtain information about the databases available on the system, the tables contained within each database and the data types used within any given table. More importantly, JavaScript can be used to execute SQL commands and retrieve data, ...
ReadMe document
... o We could have joined in the Subcategory and Category in that same query—it’s not very much data, so we’re not worried about query performance or impacting the source system. Instead, we chose to use a Lookup transform in a later step to bring in that information. o You might wonder why we have sev ...
... o We could have joined in the Subcategory and Category in that same query—it’s not very much data, so we’re not worried about query performance or impacting the source system. Instead, we chose to use a Lookup transform in a later step to bring in that information. o You might wonder why we have sev ...