PDF (997 Kbytes) - The Smart Computing Review
... Routing is a process between nodes to establish an up-to-date and efficient path for information exchange. The major concern is to discover and maintain the paths among mobile nodes, while maintaining unidirectional links in a dynamic topology, particularly in infrastructure-less networks where all ...
... Routing is a process between nodes to establish an up-to-date and efficient path for information exchange. The major concern is to discover and maintain the paths among mobile nodes, while maintaining unidirectional links in a dynamic topology, particularly in infrastructure-less networks where all ...
Ad hoc and Sensor Networks Chapter 11: Routing protocols
... destination is reached – in effect: orient edges between neighbors Necessary: resulting directed graph has to be cycle free ...
... destination is reached – in effect: orient edges between neighbors Necessary: resulting directed graph has to be cycle free ...
ppt
... – Constrained forwarding: Repair data can be suppressed downstream if no NAK seen on that port – Forward-error correction: Reduce need to NAK ...
... – Constrained forwarding: Repair data can be suppressed downstream if no NAK seen on that port – Forward-error correction: Reduce need to NAK ...
paper
... thousands of people share an international link bandwidth equivalent to an average residential ADSL connection. Various fast TCP variants such as H-TCP [4] and Hybla [5] attempt to establish a stable flow across long-latency connections, but are generally aimed at large-bandwidth scenarios to transf ...
... thousands of people share an international link bandwidth equivalent to an average residential ADSL connection. Various fast TCP variants such as H-TCP [4] and Hybla [5] attempt to establish a stable flow across long-latency connections, but are generally aimed at large-bandwidth scenarios to transf ...
ip-shiv2004-routing-I
... hence acceptance of service by customers Simplified topology: Very highly connected network Hierarchy + full mesh at each level: simple routing High cost to achieve this degree of connectivity Organizational aspects: Single organization controls entire core Afford the scale economics to ...
... hence acceptance of service by customers Simplified topology: Very highly connected network Hierarchy + full mesh at each level: simple routing High cost to achieve this degree of connectivity Organizational aspects: Single organization controls entire core Afford the scale economics to ...
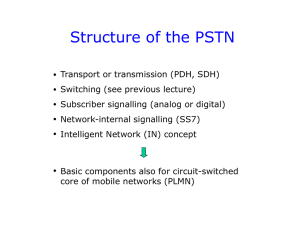
Transport and Signaling in the PSTN
... The packet-switched signalling network is totally separated from the circuit-switched connections. Consequently: • Signalling to/from databases is possible anytime. • End-to-end signalling is possible before call setup and also during the conversation phase of a call. There is one drawback: It is di ...
... The packet-switched signalling network is totally separated from the circuit-switched connections. Consequently: • Signalling to/from databases is possible anytime. • End-to-end signalling is possible before call setup and also during the conversation phase of a call. There is one drawback: It is di ...
IPv6 and Dual Stack in Mobile wireless communications
... enables the transport of IPv4 and IPv6 packets within a single PDP context between the mobile station and the gateway. • The current generation of deployed networks can support dual-stack connectivity if the packet core network elements such as the SGSN and GGSN have the capability. • As devices and ...
... enables the transport of IPv4 and IPv6 packets within a single PDP context between the mobile station and the gateway. • The current generation of deployed networks can support dual-stack connectivity if the packet core network elements such as the SGSN and GGSN have the capability. • As devices and ...
GISFI_CSeON_201309395
... The U.S. Trade and Development Agency (USTDA) provided a grant to the Ministry of Home Affairs (MHA), Government of India to partially fund a feasibility study to establish an Integrated Emergency Communications System (IECS) and supporting infrastructure in Hyderabad, Andhra Pradesh, India [68]. Th ...
... The U.S. Trade and Development Agency (USTDA) provided a grant to the Ministry of Home Affairs (MHA), Government of India to partially fund a feasibility study to establish an Integrated Emergency Communications System (IECS) and supporting infrastructure in Hyderabad, Andhra Pradesh, India [68]. Th ...
Firewall
... on one or more bastion hosts, all connected to a small, dedicated LAN between the two routers. The external router blocks attacks that use IP to break security (IP address spoofing, source routing, packet fragments), while proxy servers block attacks that would exploit a vulnerability in a higher la ...
... on one or more bastion hosts, all connected to a small, dedicated LAN between the two routers. The external router blocks attacks that use IP to break security (IP address spoofing, source routing, packet fragments), while proxy servers block attacks that would exploit a vulnerability in a higher la ...
Chapter 4
... run routing algorithms/protocol (RIP, OSPF, BGP) forwarding datagrams from incoming to outgoing link ...
... run routing algorithms/protocol (RIP, OSPF, BGP) forwarding datagrams from incoming to outgoing link ...
15-744: Computer Networking
... • Interleave packets from different sources • Efficient: resources used on demand • Statistical multiplexing ...
... • Interleave packets from different sources • Efficient: resources used on demand • Statistical multiplexing ...
SweetBait: Zero-Hour Worm Detection and Containment Using Honeypots
... flags to indicate whether it has been verified by an expert to be a valid or a false signature. The latter is essential information that permits humans to affect the decision making process that is described later on to increase the effectiveness of the system. The CC also collects alerts generated ...
... flags to indicate whether it has been verified by an expert to be a valid or a false signature. The latter is essential information that permits humans to affect the decision making process that is described later on to increase the effectiveness of the system. The CC also collects alerts generated ...
EE29 Shilpi Agrawal - RJIT paper
... can move from one place to another place and thus have no fix infrastructure or topology. This type of networks crate dynamic topology. The nodes of these types of networks find or search the route dynamically in case when a node wants to communicate with other node and thus use adaptive or dynamic ...
... can move from one place to another place and thus have no fix infrastructure or topology. This type of networks crate dynamic topology. The nodes of these types of networks find or search the route dynamically in case when a node wants to communicate with other node and thus use adaptive or dynamic ...
Document
... • A collection of peers that have agreed upon a common set of services. • Peers self-organize into peer groups, each identified by a unique peer group ID. • Each peer group can establish its own membership policy • Peers may belong to more than one peer group simultaneously. • All peers belong to th ...
... • A collection of peers that have agreed upon a common set of services. • Peers self-organize into peer groups, each identified by a unique peer group ID. • Each peer group can establish its own membership policy • Peers may belong to more than one peer group simultaneously. • All peers belong to th ...
Performance Enhancement of TFRC in Wireless Networks
... Spec says can use four separate twisted pairs of Cat 3 UTP (now Cat 5e). Utilize three pair in both directions (at 33 1/3 Mbps) with other pair for carrier sense/collision detection. Three-level ternary code is used 8B/6T:: Prior to transmission each set of 8 bits is converted into 6 ternary symbols ...
... Spec says can use four separate twisted pairs of Cat 3 UTP (now Cat 5e). Utilize three pair in both directions (at 33 1/3 Mbps) with other pair for carrier sense/collision detection. Three-level ternary code is used 8B/6T:: Prior to transmission each set of 8 bits is converted into 6 ternary symbols ...
COMP680E by M. Hamdi
... • Differentiated Services (DiffServ) is proposed by IETF as a scalable QoS solution for the next generation Internet. • Developed for relatively simple, coarse methods of providing different levels of service for Internet traffic. • Divides traffic into a small number of classes and allocates resour ...
... • Differentiated Services (DiffServ) is proposed by IETF as a scalable QoS solution for the next generation Internet. • Developed for relatively simple, coarse methods of providing different levels of service for Internet traffic. • Divides traffic into a small number of classes and allocates resour ...
Routing-distancevector
... • Solution 2: Never advertise the cost to a neighbor if this neighbor is the next hop on the current path (Split Horizon) – Example: A would not send the first routing update to B, since B is the next hop on A’s current route to C – Split Horizon does not solve count-to-infinity in all cases! ...
... • Solution 2: Never advertise the cost to a neighbor if this neighbor is the next hop on the current path (Split Horizon) – Example: A would not send the first routing update to B, since B is the next hop on A’s current route to C – Split Horizon does not solve count-to-infinity in all cases! ...
18 - UTRGV Faculty Web
... topology. We know that router R1 has three interfaces: m0, m1, and m2. We know that there are three networks directly connected to router R1. We know that there are two networks indirectly connected to R1. There must be at least three other routers involved (see next-hop column). We know to which ne ...
... topology. We know that router R1 has three interfaces: m0, m1, and m2. We know that there are three networks directly connected to router R1. We know that there are two networks indirectly connected to R1. There must be at least three other routers involved (see next-hop column). We know to which ne ...
PHD Proposal Draft
... reliability for potentially vast numbers of heterogeneous clients. However, the network connections between two network nodes in current Internet are mostly single path connections. The single path connection model is simple and easy to implement. But it may under-utilizes network resources, and doe ...
... reliability for potentially vast numbers of heterogeneous clients. However, the network connections between two network nodes in current Internet are mostly single path connections. The single path connection model is simple and easy to implement. But it may under-utilizes network resources, and doe ...
Putting BGP on the Right Path: Better Performance via Next-Hop Routing
... Section 3 shows that next-hop routing significantly reduces convergence time and router overhead. Section 4 shows how next-hop routing greatly simplifies support for multipath routing. Section 5 shows that next-hop routing reduces the attack surface for BGP and provides incentives for rational ASes ...
... Section 3 shows that next-hop routing significantly reduces convergence time and router overhead. Section 4 shows how next-hop routing greatly simplifies support for multipath routing. Section 5 shows that next-hop routing reduces the attack surface for BGP and provides incentives for rational ASes ...
Slide 1
... b. TFTP server (netboot) - The router uses the configuration register value to form a filename from which to boot a default system image stored on a network server. c. ROM (partial IOS) or keep retrying TFTP depending upon router model - If no IOS located, get partial IOS version from ROM 4. Locate ...
... b. TFTP server (netboot) - The router uses the configuration register value to form a filename from which to boot a default system image stored on a network server. c. ROM (partial IOS) or keep retrying TFTP depending upon router model - If no IOS located, get partial IOS version from ROM 4. Locate ...
Topic 16: Routing in IP over ATM networks
... The packet encapsulation has been defined in RFC1483 ([9], now obsoleted by [10]), which also takes into account the saving of virtual connections by multiplexing different protocols into a single VC. The LLC/SNAP encapsulation defined in RFC1483 is the most common encapsulation in IP over ATM netwo ...
... The packet encapsulation has been defined in RFC1483 ([9], now obsoleted by [10]), which also takes into account the saving of virtual connections by multiplexing different protocols into a single VC. The LLC/SNAP encapsulation defined in RFC1483 is the most common encapsulation in IP over ATM netwo ...
Generalized MPLS
... Deletion/ Modification (today: manual and step-by-step provisioning - doesn’t provide “bandwidth on demand” capability) Network resource optimization when using a peer interconnection model with multi-layer traffic-engineering and protection/restoration (today: provisioned model implies at least was ...
... Deletion/ Modification (today: manual and step-by-step provisioning - doesn’t provide “bandwidth on demand” capability) Network resource optimization when using a peer interconnection model with multi-layer traffic-engineering and protection/restoration (today: provisioned model implies at least was ...