bhoot pres1
... so less interference with radio signals from other nodes. The network is able to benefit from channel reuse, resulting in improved spatial capacity. Traffic balancing by dynamically routing traffic around a congested node. Less broadband connections required. ...
... so less interference with radio signals from other nodes. The network is able to benefit from channel reuse, resulting in improved spatial capacity. Traffic balancing by dynamically routing traffic around a congested node. Less broadband connections required. ...
Assignment-3
... Gateways are the best option to achieve the multimedia communications between dissimilar networks Gateways are also a key mechanism of any telephony communications. Gateway is offering bridge between telephone network and internet A network gateway work like a firewall and filters packets A ...
... Gateways are the best option to achieve the multimedia communications between dissimilar networks Gateways are also a key mechanism of any telephony communications. Gateway is offering bridge between telephone network and internet A network gateway work like a firewall and filters packets A ...
LAN / WAN / Extranet และ Network Topology แบบต่าง ๆ
... Example: X.25 standard for network access procedures on packet-switching networks ...
... Example: X.25 standard for network access procedures on packet-switching networks ...
History of the Internet
... The Birth of the Internet 1962-1968 - Packet-switching (PS) networks developed • The Internet relies on packets to transfer data. • Data is split into tiny packets that may take different routes to a destination. • The origin is military : for utmost security in transferring information of networks ...
... The Birth of the Internet 1962-1968 - Packet-switching (PS) networks developed • The Internet relies on packets to transfer data. • Data is split into tiny packets that may take different routes to a destination. • The origin is military : for utmost security in transferring information of networks ...
Congestion Control
... Slides adapted from: Congestion slides for Computer Networks: A Systems Approach (Peterson and Davis) Chapter 3 slides for Computer Networking: A Top Down Approach Featuring the Internet (Kurose and Ross) ...
... Slides adapted from: Congestion slides for Computer Networks: A Systems Approach (Peterson and Davis) Chapter 3 slides for Computer Networking: A Top Down Approach Featuring the Internet (Kurose and Ross) ...
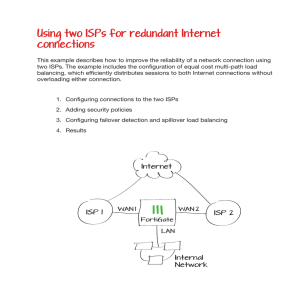
Using two ISPs for redundant Internet connections
... This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without overloading either connection. ...
... This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without overloading either connection. ...
CS4514 Course Objectives
... broadcast :: a single communications channel shared by all machines (addresses) on the network. Broadcast can be both a logical or a physical concept (e.g. Media Access ...
... broadcast :: a single communications channel shared by all machines (addresses) on the network. Broadcast can be both a logical or a physical concept (e.g. Media Access ...
Document
... System) or a domain sharing routing information – RIP: based on DVR (outdated) – OSPF: THE protocol ...
... System) or a domain sharing routing information – RIP: based on DVR (outdated) – OSPF: THE protocol ...
Review() - Personal.psu.edu
... Scheduled Contacts • If potentially communicating nodes move along predictable paths, they can predict or receive time schedules of their future positions and thereby arrange their future communication sessions • Require time-synchronization ...
... Scheduled Contacts • If potentially communicating nodes move along predictable paths, they can predict or receive time schedules of their future positions and thereby arrange their future communication sessions • Require time-synchronization ...
physcial_sci_networks_part2
... – EAP extensible Authentication Protocol • Authentication framework not a protocol • Can integrate with existing authentication systems • 802.1x ...
... – EAP extensible Authentication Protocol • Authentication framework not a protocol • Can integrate with existing authentication systems • 802.1x ...
Network Layer
... Link State Routing Algorithm 1. Each router is responsible for meeting its neighbors and learning their names. 2. Each router constructs a link state packet (LSP) which consists of a list of names and cost for each of its neighbors. 3. The LSP is transmitted to all other routers. Each router stores ...
... Link State Routing Algorithm 1. Each router is responsible for meeting its neighbors and learning their names. 2. Each router constructs a link state packet (LSP) which consists of a list of names and cost for each of its neighbors. 3. The LSP is transmitted to all other routers. Each router stores ...
Chapter 7
... – IP addresses such as 204.127.129.1 are divided by periods into four segments called octets – Static IP addresses are permanently assigned and are used by ISPs and Web sites that need to be found at the same address – Dynamic IP address are used by most other users and are temporarily assigned by y ...
... – IP addresses such as 204.127.129.1 are divided by periods into four segments called octets – Static IP addresses are permanently assigned and are used by ISPs and Web sites that need to be found at the same address – Dynamic IP address are used by most other users and are temporarily assigned by y ...
Chapter07.pdf
... – IP addresses such as 204.127.129.1 are divided by periods into four segments called octets – Static IP addresses are permanently assigned and are used by ISPs and Web sites that need to be found at the same address – Dynamic IP address are used by most other users and are temporarily assigned b ...
... – IP addresses such as 204.127.129.1 are divided by periods into four segments called octets – Static IP addresses are permanently assigned and are used by ISPs and Web sites that need to be found at the same address – Dynamic IP address are used by most other users and are temporarily assigned b ...
Border Gateway Protocol (BGP4)
... Note: iBGP Peers don’t have to be directly connected. Loopback interface are normally used as peer connection end-points.41In this case, recursive route look-up is needed. ...
... Note: iBGP Peers don’t have to be directly connected. Loopback interface are normally used as peer connection end-points.41In this case, recursive route look-up is needed. ...
Chapter 3 - Computer and Information Science | Brooklyn College
... of the message will arrive (even if some failures occur within the network) software at the destination can recognize which packets are missing and request retransmission ...
... of the message will arrive (even if some failures occur within the network) software at the destination can recognize which packets are missing and request retransmission ...
Chapter3
... of the message will arrive (even if some failures occur within the network) software at the destination can recognize which packets are missing and request retransmission ...
... of the message will arrive (even if some failures occur within the network) software at the destination can recognize which packets are missing and request retransmission ...
ch01 - Montana State University
... Reproduction or translation of this work beyond that named in Section 117 of the United States Copyright Act without the express written consent of the copyright owner is unlawful. Requests for further information should be addressed to the Permissions Department, John Wiley & Sons, Inc. Adopters of ...
... Reproduction or translation of this work beyond that named in Section 117 of the United States Copyright Act without the express written consent of the copyright owner is unlawful. Requests for further information should be addressed to the Permissions Department, John Wiley & Sons, Inc. Adopters of ...
DELAY-TOLERANT NETWORKS Volodymyr Goncharov Freiburg
... [2] Warthman, F. 2003 Tutorial. Delay-Tolerant Networks (DTNs) ...
... [2] Warthman, F. 2003 Tutorial. Delay-Tolerant Networks (DTNs) ...
Chapter 4 slides - Uppsala University
... Note: X can control incoming traffic by controlling it route advertisements to peers: e.g., don’t want to route traffic to Z -> don’t advertise any routes to Z Network Layer 4-18 ...
... Note: X can control incoming traffic by controlling it route advertisements to peers: e.g., don’t want to route traffic to Z -> don’t advertise any routes to Z Network Layer 4-18 ...
RIP
... Note: X can control incoming traffic by controlling it route advertisements to peers: e.g., don’t want to route traffic to Z -> don’t advertise any routes to Z Network Layer 4-18 ...
... Note: X can control incoming traffic by controlling it route advertisements to peers: e.g., don’t want to route traffic to Z -> don’t advertise any routes to Z Network Layer 4-18 ...
network
... connected to work together via networking. Classifications Local area network (LAN) --on a single building or a group of buildings. Such as university campus, a manufacture plant, or the like. Wide area network (WAN)—one LANs can be connected to other LANs over any distance through telephone lines o ...
... connected to work together via networking. Classifications Local area network (LAN) --on a single building or a group of buildings. Such as university campus, a manufacture plant, or the like. Wide area network (WAN)—one LANs can be connected to other LANs over any distance through telephone lines o ...