Guidance on the Use of E-Mail when Sending Person
... DO NOT USE THIS METHOD Care should still be taken with anything that might be considered sensitive to the organisation, in which case you may wish to use the secure method ...
... DO NOT USE THIS METHOD Care should still be taken with anything that might be considered sensitive to the organisation, in which case you may wish to use the secure method ...
PDF
... The FSA ID ― a username and password ― has replaced the Federal Student Aid PIN and must be used to log in to certain U.S. Department of Education websites. Your FSA ID confirms your identity when you access your financial aid information and electronically sign Federal Student Aid documents. If you ...
... The FSA ID ― a username and password ― has replaced the Federal Student Aid PIN and must be used to log in to certain U.S. Department of Education websites. Your FSA ID confirms your identity when you access your financial aid information and electronically sign Federal Student Aid documents. If you ...
PDF Product Profile CyberEdge PC Overview
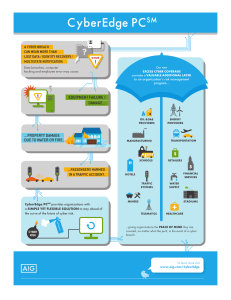
... vulnerability scanning powered by IBM, the CyberEdge Mobile App, a cyber-specific online training and risk management platform, and proactive shunning services. Rapid and Responsive Guidance When Needed Most • 24/7 access to the CyberEdge IBM-supported hotline for IT professionals to consult on iden ...
... vulnerability scanning powered by IBM, the CyberEdge Mobile App, a cyber-specific online training and risk management platform, and proactive shunning services. Rapid and Responsive Guidance When Needed Most • 24/7 access to the CyberEdge IBM-supported hotline for IT professionals to consult on iden ...
Introduction to Healthcare Information Technology
... encrypt and decrypt a message • Asymmetric cryptography uses two keys: a public and a private key • Cryptography can be applied through hardware or software • Encryption can protect data that is stored or being transmitted across a network Introduction to Healthcare Information Technology ...
... encrypt and decrypt a message • Asymmetric cryptography uses two keys: a public and a private key • Cryptography can be applied through hardware or software • Encryption can protect data that is stored or being transmitted across a network Introduction to Healthcare Information Technology ...
Call for Papers The 4th International Workshop on Security and
... challenging problem for computer scientists, social scientists, law experts and policy makers. Appropriate healthcare provision requires specialized knowledge, is information intensive and much patient information is of a particularly sensitive nature. Electronic health record systems provide opport ...
... challenging problem for computer scientists, social scientists, law experts and policy makers. Appropriate healthcare provision requires specialized knowledge, is information intensive and much patient information is of a particularly sensitive nature. Electronic health record systems provide opport ...
The Procurement Process - National 8(a) Association
... was created in 2005 to respond to a Congressional request to make agency planned purchases available to the public. Up to 2011 more than 1.2 million people have visited. 4,000 DHS employees and contractors have created 80,000 plans with anticipated funding of $232 billion • http://apfs.dhs.gov/ - Ne ...
... was created in 2005 to respond to a Congressional request to make agency planned purchases available to the public. Up to 2011 more than 1.2 million people have visited. 4,000 DHS employees and contractors have created 80,000 plans with anticipated funding of $232 billion • http://apfs.dhs.gov/ - Ne ...
MYDIGIPASS for Healthcare
... permit patient access to patient portals via username and password plus knowledge-based attributes or emerging technologies in lieu of passwords to reduce vulnerabilities in identity theft. HHS’s 2018-2020 milestone is to have at least 50% of health care organizations have implemented identity proof ...
... permit patient access to patient portals via username and password plus knowledge-based attributes or emerging technologies in lieu of passwords to reduce vulnerabilities in identity theft. HHS’s 2018-2020 milestone is to have at least 50% of health care organizations have implemented identity proof ...
Prevent Online Fraud and Identity Theft
... information from Identity Theft is crucial. There are many ways the unscrupulous can gain access to information such as your name, Social Security Number, credit card or bank account numbers, or other identifying information to commit fraud or other crimes. E-Mail Phishing - Involves you receiving a ...
... information from Identity Theft is crucial. There are many ways the unscrupulous can gain access to information such as your name, Social Security Number, credit card or bank account numbers, or other identifying information to commit fraud or other crimes. E-Mail Phishing - Involves you receiving a ...
Delivering Value Through Non-Traditional Responsibilities
... • To provide the attendee of this presentation with a nugget of information that enables their healthcare technology management team to develop, enhance and/or exploit skill-sets that will provide the patients served with a better experience while in their facilities and to enhance the value and sat ...
... • To provide the attendee of this presentation with a nugget of information that enables their healthcare technology management team to develop, enhance and/or exploit skill-sets that will provide the patients served with a better experience while in their facilities and to enhance the value and sat ...
Challenges of protecting safety internet enviroment for children in
... Forum and Chat room are comfortable communication channels for all children, Easy to build, so many dangerous website, forum and chat room are propagating unsuitable information for children. These channels allows criminals to hide effectively their traces. But It’s very difficulty to censor a ...
... Forum and Chat room are comfortable communication channels for all children, Easy to build, so many dangerous website, forum and chat room are propagating unsuitable information for children. These channels allows criminals to hide effectively their traces. But It’s very difficulty to censor a ...
Breach Detection in Healthcare
... Digital records of patients have become part of our daily reality. In hospitals, doctors’ offices, insurance companies, and other related organizations, many people need access to patient records to do their jobs. However, how do we know someone else cannot gain unauthorized access to these files? P ...
... Digital records of patients have become part of our daily reality. In hospitals, doctors’ offices, insurance companies, and other related organizations, many people need access to patient records to do their jobs. However, how do we know someone else cannot gain unauthorized access to these files? P ...
TMDE Web Site
... Pacific since late March ’03 • Stable – Infrequent minor problems have been dealt with quickly • Reliable – Site off-line briefly (< 10 minutes each occurrence) 2 times in last 6 months • Secure – Strictly follows current Navy security requirements regarding access ...
... Pacific since late March ’03 • Stable – Infrequent minor problems have been dealt with quickly • Reliable – Site off-line briefly (< 10 minutes each occurrence) 2 times in last 6 months • Secure – Strictly follows current Navy security requirements regarding access ...
Member services - Scottish Public Pensions Agency
... Philippa Brosnan Member Web Services Project Team Presentation By: ...
... Philippa Brosnan Member Web Services Project Team Presentation By: ...
Data Analytics for Evidence-based Healthcare (DAEBH 2015)
... coupled applications and data; inadequate data and knowledge standards; insufficient analytics capabilities; unsatisfactory security and privacy methodologies; absence of a clinical decisionmaking foundation. Knowledge discovery and data mining techniques, especially data analytics, have been proven ...
... coupled applications and data; inadequate data and knowledge standards; insufficient analytics capabilities; unsatisfactory security and privacy methodologies; absence of a clinical decisionmaking foundation. Knowledge discovery and data mining techniques, especially data analytics, have been proven ...
HealthCare.gov

HealthCare.gov is a health insurance exchange website operated under the United States federal government under the provisions of the Patient Protection and Affordable Care Act (ACA, often known as 'Obamacare'), designed to serve the residents of the thirty-six U.S. states that opted not to create their own state exchanges. The exchange facilitates the sale of private health insurance plans to residents of the United States and offers subsidies to those who earn less than four times the federal poverty line. The website also assists those persons who are eligible to sign up for Medicaid, and has a separate marketplace for small businesses.The October 1, 2013 roll-out of HealthCare.gov went through as planned, despite the concurrent partial government shutdown. However, the launch was marred by serious technological problems, making it difficult for the public to sign up for health insurance. The deadline to sign up for coverage that would begin January 2014 was December 23, 2013, by which time the problems had largely been fixed. The open enrollment period for 2016 coverage runs from October 1, 2015 to January 31, 2016. State exchanges also have had the same deadlines; their performance has been varied.The design of the website was overseen by the Centers for Medicare and Medicaid Services and built by a number of federal contractors, most prominently CGI Group of Canada. The original budget for CGI was $93.7 million, however this grew to $292 million prior to launch of the website. While estimates that the overall cost for building the website had reached over $500 million prior to launch, the Office of Inspector General released a report finding that the total cost of the HealthCare.gov website had reached $1.7 billion. On July 30, 2014, the Government Accountability Office released a non-partisan study that concluded the administration did not provide ""effective planning or oversight practices"" in developing the HealthCare.gov website.