Jumping Jiving GCD - the School of Mathematics, Applied
... Let’s suppose that the fraction is what you call improper, so the denominator (bottom) is smaller than the numerator (top). Then 1) We divide the numerator by the denominator, then discard the integer parts. 2) We turn the resulting fraction upside down, to get its reciprocal. 3) The new fraction ca ...
... Let’s suppose that the fraction is what you call improper, so the denominator (bottom) is smaller than the numerator (top). Then 1) We divide the numerator by the denominator, then discard the integer parts. 2) We turn the resulting fraction upside down, to get its reciprocal. 3) The new fraction ca ...
Computing the Greatest Common Divisor of - CECM
... degree 0 in x. Thus, p = 3 is bad. If we choose p = 7, then gcd(A mod 3, B mod 3) = (x + y + 4)(3x + y + 1). Thus, p = 7 is unlucky. ...
... degree 0 in x. Thus, p = 3 is bad. If we choose p = 7, then gcd(A mod 3, B mod 3) = (x + y + 4)(3x + y + 1). Thus, p = 7 is unlucky. ...
Solutions to Midterm 1
... We need to nd two elements x ∈ U (999) = {a ∈ N | a < 999 & gcd (a, 999) = 1} such that x2 = 1, the identity element of U (999). Let us forget about modular arithmetic for a moment and solve x2 = 1 with algebra: x = 1 and x = −1. x = 1 ∈ U (999) (gcd(1, 999) = 1), but −1 ∈ / U (999) since −1 is not ...
... We need to nd two elements x ∈ U (999) = {a ∈ N | a < 999 & gcd (a, 999) = 1} such that x2 = 1, the identity element of U (999). Let us forget about modular arithmetic for a moment and solve x2 = 1 with algebra: x = 1 and x = −1. x = 1 ∈ U (999) (gcd(1, 999) = 1), but −1 ∈ / U (999) since −1 is not ...
pdf file
... Although carrying out an algorithm can seem boring (and this is why we usually let computers do them), being able to do them precisely and carefully is an important part of doing mathematics. In the next chapter, we’ll meet another algorithm which solves an even more important problem. ...
... Although carrying out an algorithm can seem boring (and this is why we usually let computers do them), being able to do them precisely and carefully is an important part of doing mathematics. In the next chapter, we’ll meet another algorithm which solves an even more important problem. ...
pdf file
... φ(n) = |G|, the cardinality of the set G. By 2.6.12 on p. 58 of Artin, since 1 is the identity of G, for each a ∈ G, then aφ(n) = 1. The following theorem of Euler is an easy consequence (groups did not exist yet when Euler was around). Theorem 4.1. aφ(n) ≡ 1 (mod n). For this statement to be useful ...
... φ(n) = |G|, the cardinality of the set G. By 2.6.12 on p. 58 of Artin, since 1 is the identity of G, for each a ∈ G, then aφ(n) = 1. The following theorem of Euler is an easy consequence (groups did not exist yet when Euler was around). Theorem 4.1. aφ(n) ≡ 1 (mod n). For this statement to be useful ...
TCSS 343: Large Integer Multiplication Suppose we want to multiply
... Since we can multiply two 1-bit integers in constant time, T(1) = 1. (If we wanted to be more accurate, we would say T(1) = d, for some constant d.) In the recursive case, in order to multiply two n-bit integers, we need to solve three instances of the problem of multiplying two (n/2)-bit integers a ...
... Since we can multiply two 1-bit integers in constant time, T(1) = 1. (If we wanted to be more accurate, we would say T(1) = d, for some constant d.) In the recursive case, in order to multiply two n-bit integers, we need to solve three instances of the problem of multiplying two (n/2)-bit integers a ...
The Probability of Relatively Prime Polynomials
... so the original polynomials are relatively prime, since the constant term, 11/2, is not zero. As with the integers, we can reverse this procedure startingwith the final pair of polynomials, and backtracking through the quotients to obtain the original pair. Notice that the Euclidean Algorithm works ...
... so the original polynomials are relatively prime, since the constant term, 11/2, is not zero. As with the integers, we can reverse this procedure startingwith the final pair of polynomials, and backtracking through the quotients to obtain the original pair. Notice that the Euclidean Algorithm works ...
A+B
... Every positive integer greater than 1 can be written uniquely as a prime or as the product of two or more primes where the prime factors are written in order of nondecreasing size. • Example 2: The prime factorizations of 100, 641 , 999 and 1024 are given by ...
... Every positive integer greater than 1 can be written uniquely as a prime or as the product of two or more primes where the prime factors are written in order of nondecreasing size. • Example 2: The prime factorizations of 100, 641 , 999 and 1024 are given by ...
Lecture 9 - MyCourses
... Wiener (1989) showed how to exploit this information to solve (1) for the private exponent a and all other parameters k , p and q provided that a is sufficiently small. Wiener’s method is based on continued fractions. ...
... Wiener (1989) showed how to exploit this information to solve (1) for the private exponent a and all other parameters k , p and q provided that a is sufficiently small. Wiener’s method is based on continued fractions. ...
Jumping Jiving GCD - the School of Mathematics, Applied
... A group of friends are playing the following game: They form new numbers by using any of the symbols in the list any number of times, but no other symbols. a) How many numbers can they get this way? b) What is the smallest positive number they can get in this way? c) Think about all the numbers they ...
... A group of friends are playing the following game: They form new numbers by using any of the symbols in the list any number of times, but no other symbols. a) How many numbers can they get this way? b) What is the smallest positive number they can get in this way? c) Think about all the numbers they ...
The Collatz Conjecture - HAL
... Corollary 2.1. Let x > 1 be a positive integer then (1) If x is pair, x satisfies the stuck condition, (2) If x = 4k + 1 for some k, x satisfies the stuck condition, (3) If x = 16k + 3, for some k, x satisfies the stuck condition. Proof. The first case is pretty obvious, divide x by two to obtain a ...
... Corollary 2.1. Let x > 1 be a positive integer then (1) If x is pair, x satisfies the stuck condition, (2) If x = 4k + 1 for some k, x satisfies the stuck condition, (3) If x = 16k + 3, for some k, x satisfies the stuck condition. Proof. The first case is pretty obvious, divide x by two to obtain a ...
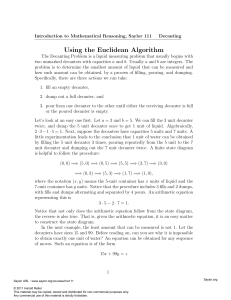
Here
... the solution to the decanting problem is to fill the a capacity decanter x times, repeatedly pouring its contents into the b unit decanter. The b unit decanter will be dumped y times, so the total liquid on hand at the end is the difference ax − by = c. Let’s look at another specific example. Again ...
... the solution to the decanting problem is to fill the a capacity decanter x times, repeatedly pouring its contents into the b unit decanter. The b unit decanter will be dumped y times, so the total liquid on hand at the end is the difference ax − by = c. Let’s look at another specific example. Again ...
from Terrel Smith`s class, MS-Powerpoint slide set
... • For starters, mathematical induction is one of the most powerful methods of proof in existence. Add to it that it lies almost exclusively at the heart of computer science. The ability of a program to recognize, interpret, and capitalize on distinguishable patterns is essential for that program to ...
... • For starters, mathematical induction is one of the most powerful methods of proof in existence. Add to it that it lies almost exclusively at the heart of computer science. The ability of a program to recognize, interpret, and capitalize on distinguishable patterns is essential for that program to ...
gcd( 0,6)
... • Recursive method calls itself, directly or indirectly (almost always directly in practice) • Recursion is based on divide and conquer: – Reduce an original problem to a sequence of smaller instances, until they are small enough to ...
... • Recursive method calls itself, directly or indirectly (almost always directly in practice) • Recursion is based on divide and conquer: – Reduce an original problem to a sequence of smaller instances, until they are small enough to ...
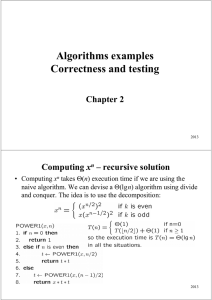
Algorithms examples Correctness and testing
... • An algorithm for solving a problem P is totally correct iff for all problem instances i ∈ I it terminates and produces the correct output o ∈ O (i.e. the pair (i,o) ∈ R). • An algorithm for solving a problem P is partially correct iff for all problem instances i ∈ I if it terminates then it produc ...
... • An algorithm for solving a problem P is totally correct iff for all problem instances i ∈ I it terminates and produces the correct output o ∈ O (i.e. the pair (i,o) ∈ R). • An algorithm for solving a problem P is partially correct iff for all problem instances i ∈ I if it terminates then it produc ...
Logarithms in running time
... Solution 2: O(logN) Find the middle element Amid in the list and compare it with X If they are equal, stop If X < Amid consider the left part If X > Amid consider the right part Do until the list is reduced to one element ...
... Solution 2: O(logN) Find the middle element Amid in the list and compare it with X If they are equal, stop If X < Amid consider the left part If X > Amid consider the right part Do until the list is reduced to one element ...
here
... Problem 1: Write a MATLAB program to perform exponent factorization; in particular, the input should be positive integers a, k, and n such that ak = 1 mod n, and the output (if all goes well) should be nontrivial factors d1 and d2 such that n = d1 · d2 . Use your algorithm to factor n = 68309797 usi ...
... Problem 1: Write a MATLAB program to perform exponent factorization; in particular, the input should be positive integers a, k, and n such that ak = 1 mod n, and the output (if all goes well) should be nontrivial factors d1 and d2 such that n = d1 · d2 . Use your algorithm to factor n = 68309797 usi ...
Partial-Quotient Division Algorithm
... -Are there at least 10 (7s) in 127? ______________________________________________ -Are there at least 20 (7s) in 127? ______________________________________________ -10 (7s) = 70 is the closest to 127 without going over 4) Find out how much is left to divide. Subtract 70 from 127. 5) Now find the n ...
... -Are there at least 10 (7s) in 127? ______________________________________________ -Are there at least 20 (7s) in 127? ______________________________________________ -10 (7s) = 70 is the closest to 127 without going over 4) Find out how much is left to divide. Subtract 70 from 127. 5) Now find the n ...
Finding the Greatest Common Divisor by repeated
... Corollary: If a = GCD( b , c ) where b c , then then a divides (c b) ...
... Corollary: If a = GCD( b , c ) where b c , then then a divides (c b) ...
Elementary Properties of the Integers
... Theorem (2-2). If a and b are integers, not both zero, then gcd(a, b) exists and is unique. Note that this result is trivial if either a or b is zero. Also note that changing the sign of a or b or swapping a for b does not change the gcd. Without loss of generality, we may thus assume that 0 < b ≤ a ...
... Theorem (2-2). If a and b are integers, not both zero, then gcd(a, b) exists and is unique. Note that this result is trivial if either a or b is zero. Also note that changing the sign of a or b or swapping a for b does not change the gcd. Without loss of generality, we may thus assume that 0 < b ≤ a ...
Euclidean algorithm

In mathematics, the Euclidean algorithm, or Euclid's algorithm, is an efficient method for computing the greatest common divisor (GCD) of two numbers, the largest number that divides both of them without leaving a remainder. It is named after the ancient Greek mathematician Euclid, who first described it in Euclid's Elements (c. 300 BC).It is an example of an algorithm, a step-by-step procedure for performing a calculation according to well-defined rules,and is one of the oldest numerical algorithms in common use. It can be used to reduce fractions to their simplest form, and is a part of many other number-theoretic and cryptographic calculations.The Euclidean algorithm is based on the principle that the greatest common divisor of two numbers does not change if the larger number is replaced by its difference with the smaller number. For example, 21 is the GCD of 252 and 105 (252 = 21 × 12 and 105 = 21 × 5), and the same number 21 is also the GCD of 105 and 147 = 252 − 105. Since this replacement reduces the larger of the two numbers, repeating this process gives successively smaller pairs of numbers until one of the two numbers reaches zero. When that occurs, the other number (the one that is not zero) is the GCD of the original two numbers. By reversing the steps, the GCD can be expressed as a sum of the two original numbers each multiplied by a positive or negative integer, e.g., 21 = 5 × 105 + (−2) × 252. The fact that the GCD can always be expressed in this way is known as Bézout's identity.The version of the Euclidean algorithm described above (and by Euclid) can take many subtraction steps to find the GCD when one of the given numbers is much bigger than the other. A more efficient version of the algorithm shortcuts these steps, instead replacing the larger of the two numbers by its remainder when divided by the smaller of the two. With this improvement, the algorithm never requires more steps than five times the number of digits (base 10) of the smaller integer. This was proven by Gabriel Lamé in 1844, and marks the beginning of computational complexity theory. Additional methods for improving the algorithm's efficiency were developed in the 20th century.The Euclidean algorithm has many theoretical and practical applications. It is used for reducing fractions to their simplest form and for performing division in modular arithmetic. Computations using this algorithm form part of the cryptographic protocols that are used to secure internet communications, and in methods for breaking these cryptosystems by factoring large composite numbers. The Euclidean algorithm may be used to solve Diophantine equations, such as finding numbers that satisfy multiple congruences according to the Chinese remainder theorem, to construct continued fractions, and to find accurate rational approximations to real numbers. Finally, it is a basic tool for proving theorems in number theory such as Lagrange's four-square theorem and the uniqueness of prime factorizations. The original algorithm was described only for natural numbers and geometric lengths (real numbers), but the algorithm was generalized in the 19th century to other types of numbers, such as Gaussian integers and polynomials of one variable. This led to modern abstract algebraic notions such as Euclidean domains.