Cisco TrustSec How-To Guide: Segmenting Clients and Servers in
... Virtual server - physical server segmentation using SGFW (Figure 2). For this use case, we will deny all network traffic between the engineering server connected to the Cisco Nexus 7000 distribution switch and the virtual servers hosted behind the Cisco Nexus 7000 end-of-row switch. While SGFW is th ...
... Virtual server - physical server segmentation using SGFW (Figure 2). For this use case, we will deny all network traffic between the engineering server connected to the Cisco Nexus 7000 distribution switch and the virtual servers hosted behind the Cisco Nexus 7000 end-of-row switch. While SGFW is th ...
Cisco Catalyst 4500E Supervisor Engine 7
... medianet, Flexible NetFlow, Cisco EnergyWise, Cisco Powered Workspace - and other feature enhancements enabled by the Cisco Catalyst 4500E Supervisor Engine 7-E. Backward and forward compatibility with most existing Cisco Catalyst 4500 and 4500E line cards assures deeper customer satisfaction with t ...
... medianet, Flexible NetFlow, Cisco EnergyWise, Cisco Powered Workspace - and other feature enhancements enabled by the Cisco Catalyst 4500E Supervisor Engine 7-E. Backward and forward compatibility with most existing Cisco Catalyst 4500 and 4500E line cards assures deeper customer satisfaction with t ...
PDF
... IP SLA IP SLA is embedded in Cisco IOS Software for active monitoring. IP SLA generates and analyzes the traffic to measure performance between Cisco IOS Software devices or between Cisco IOS Software devices and network application servers. IP SLA offers a unique set of performance measurements, ty ...
... IP SLA IP SLA is embedded in Cisco IOS Software for active monitoring. IP SLA generates and analyzes the traffic to measure performance between Cisco IOS Software devices or between Cisco IOS Software devices and network application servers. IP SLA offers a unique set of performance measurements, ty ...
Chapter 5 - Ethernet
... • If signals are then detected that show another device was transmitting at the same time, all devices stop sending and try again later • While Ethernet networks are designed with CSMA/CD technology, with today’s intermediate devices, collisions do not occur and the processes utilized by CSMA/CD are ...
... • If signals are then detected that show another device was transmitting at the same time, all devices stop sending and try again later • While Ethernet networks are designed with CSMA/CD technology, with today’s intermediate devices, collisions do not occur and the processes utilized by CSMA/CD are ...
IPv6 Addressing
... the public address space to a few hundred million (<1/10th the mathematical possibility) The increase of Internet-connected devices and appliances will eventually deplete the IPv4 address space ...
... the public address space to a few hundred million (<1/10th the mathematical possibility) The increase of Internet-connected devices and appliances will eventually deplete the IPv4 address space ...
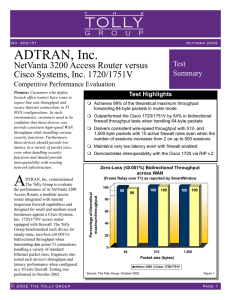
NetVanta 3200 Tolly Group Report
... using the SmartBits SmartWindow and the latency test defined in the RFC 2544 test suite. Traffic was generated at 10% of T1 line rate with 2 sessions running for baseline latency tests. For firewall latency tests, traffic was generated at 10%, 13% and 39% of the T1 line rate, while using 64-, 512- a ...
... using the SmartBits SmartWindow and the latency test defined in the RFC 2544 test suite. Traffic was generated at 10% of T1 line rate with 2 sessions running for baseline latency tests. For firewall latency tests, traffic was generated at 10%, 13% and 39% of the T1 line rate, while using 64-, 512- a ...
Presentation Deck - Cisco Connect Toronto 2015
... Goals of APIC Service Insertion and Automation Configure and Manage VLAN allocation for service insertion Configure the network to redirect traffic through service device Configure network and service function parameters on service device ...
... Goals of APIC Service Insertion and Automation Configure and Manage VLAN allocation for service insertion Configure the network to redirect traffic through service device Configure network and service function parameters on service device ...
PDF
... Cisco VACS provides you with a choice of ready-to-use application container templates that define the rules for deploying a collection of virtual machines (VMs) within a private network secured by a firewall. An application container is a set of virtual services such as virtual switches, routers, fi ...
... Cisco VACS provides you with a choice of ready-to-use application container templates that define the rules for deploying a collection of virtual machines (VMs) within a private network secured by a firewall. An application container is a set of virtual services such as virtual switches, routers, fi ...
Basic Switching and Switch Configuration
... • Another way to increase the speed at which a LAN operates is to upgrade from Ethernet to Fast Ethernet • Full duplex can also improve Ethernet performance CCNA Guide to Cisco Networking Fundamentals, Fourth Edition ...
... • Another way to increase the speed at which a LAN operates is to upgrade from Ethernet to Fast Ethernet • Full duplex can also improve Ethernet performance CCNA Guide to Cisco Networking Fundamentals, Fourth Edition ...
PDF
... Obtaining Technical Assistance Cisco provides Cisco.com as a starting point for all technical assistance. Customers and partners can obtain online documentation, troubleshooting tips, and sample configurations from online tools by using the Cisco Technical Assistance Center (TAC) Web Site. Cisco.com ...
... Obtaining Technical Assistance Cisco provides Cisco.com as a starting point for all technical assistance. Customers and partners can obtain online documentation, troubleshooting tips, and sample configurations from online tools by using the Cisco Technical Assistance Center (TAC) Web Site. Cisco.com ...
PDF
... more network connections or offer application optimization technologies (for example, Cisco Wide Area Application Services [WAAS]). Additional WAN bandwidth may improve aggregate throughput but may not improve delay or loss for critical applications. Application optimization technologies such as Cis ...
... more network connections or offer application optimization technologies (for example, Cisco Wide Area Application Services [WAAS]). Additional WAN bandwidth may improve aggregate throughput but may not improve delay or loss for critical applications. Application optimization technologies such as Cis ...
Cisco AS5300/Voice Gateway
... infrastructure to deploy VoIP. The Cisco packet telephony solution is based on H.323, an ITU standard that provides a foundation for data, audio, and video, and communications across IP-based networks. Because SPs already offer Internet access, they can readily offer long-distance service by increme ...
... infrastructure to deploy VoIP. The Cisco packet telephony solution is based on H.323, an ITU standard that provides a foundation for data, audio, and video, and communications across IP-based networks. Because SPs already offer Internet access, they can readily offer long-distance service by increme ...
Curriculum Review - YSU Computer Science & Information Systems
... DDR Considerations Dial on Demand Routing provides: – Network routing and directory services. – The illusion of full-time connectivity over circuitswitched connections. ...
... DDR Considerations Dial on Demand Routing provides: – Network routing and directory services. – The illusion of full-time connectivity over circuitswitched connections. ...
Title: First Slide in a Presentation
... the PIX with a security level of 100 to the outside interface of the PIX with a security level of 0, all IP-based traffic is allowed unless it is restricted by ACLs, authentication, or authorization. ICMP does not follow this rule. • Lower security level interface to a higher security level interfac ...
... the PIX with a security level of 100 to the outside interface of the PIX with a security level of 0, all IP-based traffic is allowed unless it is restricted by ACLs, authentication, or authorization. ICMP does not follow this rule. • Lower security level interface to a higher security level interfac ...
Objectives
... Multiple OSPFv3 protocol instances can now run over a single link: This allows for separate autonomous systems, each running OSPF, to use a common link. A single link could belong to multiple areas. Instance ID is a new field that is used to have multiple OSPFv3 protocol instances per link. In ...
... Multiple OSPFv3 protocol instances can now run over a single link: This allows for separate autonomous systems, each running OSPF, to use a common link. A single link could belong to multiple areas. Instance ID is a new field that is used to have multiple OSPFv3 protocol instances per link. In ...
Before You Begin: Assign Information Classification
... The Elastic Compute Unit (ECU) was introduced by Amazon EC2 as an abstraction of compute resources. Amazon’s Definition of ECU notes “We use several benchmarks and tests to manage the consistency and predictability of the performance of an EC2 Compute Unit. One EC2 Compute Unit provides the equivale ...
... The Elastic Compute Unit (ECU) was introduced by Amazon EC2 as an abstraction of compute resources. Amazon’s Definition of ECU notes “We use several benchmarks and tests to manage the consistency and predictability of the performance of an EC2 Compute Unit. One EC2 Compute Unit provides the equivale ...
Cisco TrustSec 3.0 How-To Guide: Introduction to MACSec and NDAC Guide
... endpoint (such as the Cisco AnyConnect Network Access Manager). The encryption on the endpoint may be handled in hardware (if the endpoint possesses the correct hardware) or in software using the main CPU for the encryption and decryption. The Cisco switch has the ability to force encryption, make e ...
... endpoint (such as the Cisco AnyConnect Network Access Manager). The encryption on the endpoint may be handled in hardware (if the endpoint possesses the correct hardware) or in software using the main CPU for the encryption and decryption. The Cisco switch has the ability to force encryption, make e ...
VLSM and CIDR
... Classful and Classless IP Addressing Classes of IP addresses are identified by the decimal number of the 1st octet Class A address begin with a 0 bit Range of class A addresses = 0.0.0.0 to 127.255.255.255 Class B address begin with a 1 bit and a 0 bit Range of class B addresses = 128.0.0.0 to 19 ...
... Classful and Classless IP Addressing Classes of IP addresses are identified by the decimal number of the 1st octet Class A address begin with a 0 bit Range of class A addresses = 0.0.0.0 to 127.255.255.255 Class B address begin with a 1 bit and a 0 bit Range of class B addresses = 128.0.0.0 to 19 ...
PDF - This Chapter (1.28 MB)
... and sends it to the Supervisor. The Supervisor caches all the items locally. When the SNMP client queries the docsIf3CmtsCmRegStatusMacAddr.2 later, the information is available in the Supervisor cache directly instead of sending another IPC message to interface card. The number N depends on the sin ...
... and sends it to the Supervisor. The Supervisor caches all the items locally. When the SNMP client queries the docsIf3CmtsCmRegStatusMacAddr.2 later, the information is available in the Supervisor cache directly instead of sending another IPC message to interface card. The number N depends on the sin ...
ITE PC v4.0 Chapter 1
... • If signals are then detected that show another device was transmitting at the same time, all devices stop sending and try again later • While Ethernet networks are designed with CSMA/CD technology, with today’s intermediate devices, collisions do not occur and the processes utilized by CSMA/CD are ...
... • If signals are then detected that show another device was transmitting at the same time, all devices stop sending and try again later • While Ethernet networks are designed with CSMA/CD technology, with today’s intermediate devices, collisions do not occur and the processes utilized by CSMA/CD are ...
Cisco Unified Presence Server
... standardizing VoIP protocols were too immature to replicate PBX features. Cisco had to develop SCCP protocol to address the difficult issues and build that IP-PBX. At the same time, we also have focused on the IETF standards body solving the difficult SIP problems (SIP and SIPING WG leads, RFCs, etc ...
... standardizing VoIP protocols were too immature to replicate PBX features. Cisco had to develop SCCP protocol to address the difficult issues and build that IP-PBX. At the same time, we also have focused on the IETF standards body solving the difficult SIP problems (SIP and SIPING WG leads, RFCs, etc ...
Network Layer and Path Determination
... • Routers pass traffic from all routed protocols over the internetwork CSE: Networking Fundamentals—OSI Model ...
... • Routers pass traffic from all routed protocols over the internetwork CSE: Networking Fundamentals—OSI Model ...
Cisco Systems
Cisco Systems, Inc. is an American multinational technology company headquartered in San Jose, California, that designs, manufactures, and sells networking equipment. The stock was added to the Dow Jones Industrial Average on June 8, 2009, and is also included in the S&P 500 Index, the Russell 1000 Index, NASDAQ-100 Index and the Russell 1000 Growth Stock Index.Cisco is the worldwide leader in networking for the Internet. 85 percent of Internet traffic travel across Cisco's systems, and it supports, manages and operates business systems for various and major third parties.