The Simple Economics of Approximately Optimal Auctions
... Yan (2011) that are approximately optimal for single-dimensional agents are approximately optimal for general agents (in the same service constrained environment) and the same approximation factor is guaranteed. Moreover, these sequential posted pricing bounds give another bound on the approximation ...
... Yan (2011) that are approximately optimal for single-dimensional agents are approximately optimal for general agents (in the same service constrained environment) and the same approximation factor is guaranteed. Moreover, these sequential posted pricing bounds give another bound on the approximation ...
The Extent of the Market and the Optimal Degree of Specialization∗
... of the market (ρ) when ρ is small but is independent of ρ when ρ is large. The explanation is as follows. When ρ is large, the society is able to detect defections easily. With the potential punishment of autarky to defections, the social planner can implement the unconstrained social optimum, wher ...
... of the market (ρ) when ρ is small but is independent of ρ when ρ is large. The explanation is as follows. When ρ is large, the society is able to detect defections easily. With the potential punishment of autarky to defections, the social planner can implement the unconstrained social optimum, wher ...
Measuring Inconsistency through Minimal Inconsistent Sets
... Against this background, it is interesting to note that the use of minimal inconsistent subsets of a belief base has received much less attention as the basis for defining inconsistency measures. So in this paper, we explore the nature of some interesting measures of inconsistency based on minimal i ...
... Against this background, it is interesting to note that the use of minimal inconsistent subsets of a belief base has received much less attention as the basis for defining inconsistency measures. So in this paper, we explore the nature of some interesting measures of inconsistency based on minimal i ...
The Fixed-Price Auction
... for combinatorial auctions with single-minded bidders (LehmannO’callaghan-Shoham). ...
... for combinatorial auctions with single-minded bidders (LehmannO’callaghan-Shoham). ...
Mechanism Design for Daily Deals
... to the classical knapsack problem [9], which can be viewed as our special case by setting li = ui and K = 1. While some recent work on stochastic knapsack problem [10] consider items with stochastic volumes, the allocation of an item is binary (i.e., pack it or not). Our work is different in the sen ...
... to the classical knapsack problem [9], which can be viewed as our special case by setting li = ui and K = 1. While some recent work on stochastic knapsack problem [10] consider items with stochastic volumes, the allocation of an item is binary (i.e., pack it or not). Our work is different in the sen ...
1 Model with Time-Consistent Agents
... cm , ym , cm , ym θm ∈Θ is truthfully implementable by a direct betting mechanism if the allocation satisfies the incentive compatibility constraints (7) and the executability constraints (8). Note that since β̂ = 1, the incentive compatibility constraints (7) are the same for the TC and TI agents. ...
... cm , ym , cm , ym θm ∈Θ is truthfully implementable by a direct betting mechanism if the allocation satisfies the incentive compatibility constraints (7) and the executability constraints (8). Note that since β̂ = 1, the incentive compatibility constraints (7) are the same for the TC and TI agents. ...
Probabilistic Aspects of Computer Science
... message sent by p is always the list of predecessors with possible repetition if the length is greater than the size of the ring. The three functions have in common that at least for one symmetrical configuration, every process must receive a trace of length n − 1 before deciding the value of the fu ...
... message sent by p is always the list of predecessors with possible repetition if the length is greater than the size of the ring. The three functions have in common that at least for one symmetrical configuration, every process must receive a trace of length n − 1 before deciding the value of the fu ...
A Payment Rules through Discriminant
... There are, however, significant challenges associated with this classical approach. First, it can be analytically cumbersome to derive optimal mechanisms for domains that are multidimensional, in the sense that each agent’s private information is described through more than a single number, and few ...
... There are, however, significant challenges associated with this classical approach. First, it can be analytically cumbersome to derive optimal mechanisms for domains that are multidimensional, in the sense that each agent’s private information is described through more than a single number, and few ...
Notes on The Principal-Agent Model
... - Recall that in the symmetric information case, the type 1 (low cost) agent and the type 2 (high cost) agent preferred the contract that was written for the type 2 agent. - This means that if a menu consisted of the symmetric information contracts, then both agents would choose the type 2 contract. ...
... - Recall that in the symmetric information case, the type 1 (low cost) agent and the type 2 (high cost) agent preferred the contract that was written for the type 2 agent. - This means that if a menu consisted of the symmetric information contracts, then both agents would choose the type 2 contract. ...
Lecture 11
... lattice, i.e., the algorithm needs to visit the grand coalition and all the CSs composed of 2 coalitions. The bound improves each time a new level is visited. An empirical study of different strategies for visiting the other levels is presented in [56]. Three different algorithms are empirically tes ...
... lattice, i.e., the algorithm needs to visit the grand coalition and all the CSs composed of 2 coalitions. The bound improves each time a new level is visited. An empirical study of different strategies for visiting the other levels is presented in [56]. Three different algorithms are empirically tes ...
Incentivizing Exploration - Cornell Computer Science
... exploration process. This trade-off comes up in different guises across a surprisingly wide range of domains. Crowdsourced information discovery. Social news readers or similar sites, which promote stories or pages of interest to their readers, typically rely on readers themselves to discover and sh ...
... exploration process. This trade-off comes up in different guises across a surprisingly wide range of domains. Crowdsourced information discovery. Social news readers or similar sites, which promote stories or pages of interest to their readers, typically rely on readers themselves to discover and sh ...
DYCOM: A Dynamic Truthful Budget Balanced - EXPLORE-2017
... Wurman et al. [26] presented a dynamic two-sided solution incentivizing truthful reporting from either the buyers or the sellers but not simultaneously from both. A different dynamic solution given by Blum et al. [2] maximizes the SWF of buyers and non-selling sellers in the single commodity unit de ...
... Wurman et al. [26] presented a dynamic two-sided solution incentivizing truthful reporting from either the buyers or the sellers but not simultaneously from both. A different dynamic solution given by Blum et al. [2] maximizes the SWF of buyers and non-selling sellers in the single commodity unit de ...
Automated online mechanism design and prophet inequalities
... underlying allocation problem admits an online algorithm with competitive ratio 1. (Parkes & Singh 2003) have studied VCG-based online mechanisms also under a weaker notion of incentive compatibility, Bayes-Nash equilibrium, adopting the framework of Markov Decision Processes. The setting for this w ...
... underlying allocation problem admits an online algorithm with competitive ratio 1. (Parkes & Singh 2003) have studied VCG-based online mechanisms also under a weaker notion of incentive compatibility, Bayes-Nash equilibrium, adopting the framework of Markov Decision Processes. The setting for this w ...
optimal allocation with ex-post verification and limited penalties
... The optimal allocation rule is different when the number of agents is large. It can be described as a shortlisting procedure. Agents report whether their values are above or below a single threshold. The former are shortlisted with certainty, while the latter are shortlisted with a probability of le ...
... The optimal allocation rule is different when the number of agents is large. It can be described as a shortlisting procedure. Agents report whether their values are above or below a single threshold. The former are shortlisted with certainty, while the latter are shortlisted with a probability of le ...
http://cep.lse.ac.uk/seminarpapers/10-03-16-PM.pdf
... (2011) proved analogous results for environments with multiple copies. In the large market setting of the present paper, Che and Kojima (2010) showed asymptotic equivalence of two mechanisms: Random Priority and Probabilistic Serial.12 Furthermore, by proving the equivalence of these two mechanisms, ...
... (2011) proved analogous results for environments with multiple copies. In the large market setting of the present paper, Che and Kojima (2010) showed asymptotic equivalence of two mechanisms: Random Priority and Probabilistic Serial.12 Furthermore, by proving the equivalence of these two mechanisms, ...
Bayesian incentive compatibility via matchings.
... This approach to mechanism design sits well with a standard paradigm for algorithm design wherein a practitioner might fine-tune their algorithm to the actual workload they face rather than optimize for the worst case. Furthermore, in the Internet applications that motivate this field, protocols are ...
... This approach to mechanism design sits well with a standard paradigm for algorithm design wherein a practitioner might fine-tune their algorithm to the actual workload they face rather than optimize for the worst case. Furthermore, in the Internet applications that motivate this field, protocols are ...
Our Inoculation Strategies for Victims of Viruses and the Sum
... OPT: The cost of the optimum solution for the inoculation problem,then there exists a polynomial time approximation algorithm that finds a solution with cost at most O(log1.5n)OPT Algorithm Courses ...
... OPT: The cost of the optimum solution for the inoculation problem,then there exists a polynomial time approximation algorithm that finds a solution with cost at most O(log1.5n)OPT Algorithm Courses ...
Tetris Game-playing Agents in Python
... table taking up significant amounts of memory and slowing down the entire system that the game was running on. This is consistent with other work in the field such as in [2] where state based q-learning performed sub optimally to other methods in solving Tetris due to the state space size. The featu ...
... table taking up significant amounts of memory and slowing down the entire system that the game was running on. This is consistent with other work in the field such as in [2] where state based q-learning performed sub optimally to other methods in solving Tetris due to the state space size. The featu ...
On the Interaction between Computer Science and Economics
... to race, and give $100 to the winner. Why is this procedure successful? Well, Charles has created a situation in which both Ann and Bob have an incentive to make their horse run as fast as possible. The situation can be represented by a strategic game, a detailed discussion can be found in [?]. On t ...
... to race, and give $100 to the winner. Why is this procedure successful? Well, Charles has created a situation in which both Ann and Bob have an incentive to make their horse run as fast as possible. The situation can be represented by a strategic game, a detailed discussion can be found in [?]. On t ...
Theory of Mechanism Design - Assignment 3 1. We consider the
... Solution. The unique efficient matching in this profile is man mi is matched to woman wi for all i ∈ {1, . . . , n}. Hence, both the versions of the deferred acceptance algorithm must terminate at this matching. 3. Consider the house allocation model with three agents N = {1, 2, 3} and three object ...
... Solution. The unique efficient matching in this profile is man mi is matched to woman wi for all i ∈ {1, . . . , n}. Hence, both the versions of the deferred acceptance algorithm must terminate at this matching. 3. Consider the house allocation model with three agents N = {1, 2, 3} and three object ...
The Least Square Nucleolus is a Normalized Banzhaf Value
... According to the Banzhaf value, we observe that there are two weak (but not symmetric) players, 1 and 2, and three strong players, 3, 4, and 5. In this case, the additive normalization of the Banzhaf value proposes a payoff below the first agent’s standalone worth. Consequently, Bt differs from Ba . ...
... According to the Banzhaf value, we observe that there are two weak (but not symmetric) players, 1 and 2, and three strong players, 3, 4, and 5. In this case, the additive normalization of the Banzhaf value proposes a payoff below the first agent’s standalone worth. Consequently, Bt differs from Ba . ...
Yao minmax.pdf
... the expected cost of a randomized algorithm on the worst case input, is no better than a worst-case worst random probability distribution of the deterministic algorithm which performs best for that distribution. Thus, to establish a lower bound on the performance of randomized algorithms, it suffice ...
... the expected cost of a randomized algorithm on the worst case input, is no better than a worst-case worst random probability distribution of the deterministic algorithm which performs best for that distribution. Thus, to establish a lower bound on the performance of randomized algorithms, it suffice ...
Reconnecting Cost with Value July 17, 2009 ACC Northeast
... combined with a decision to drive value in process. • What is it that you need to move from intellectual agreement with the theory to practical applications you can begin to implement? • Change management can be both radical and incremental – it can be planned and collaborative • The real risk (for ...
... combined with a decision to drive value in process. • What is it that you need to move from intellectual agreement with the theory to practical applications you can begin to implement? • Change management can be both radical and incremental – it can be planned and collaborative • The real risk (for ...
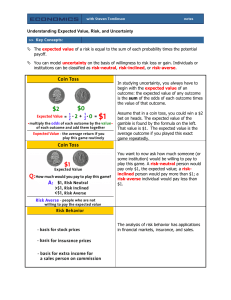
Understanding Expected Value, Risk, and Uncertainty The expected
... You can model uncertainty on the basis of willingness to risk loss or gain. Individuals or institutions can be classified as risk-neutral, risk-inclined, or risk-averse. In studying uncertainty, you always have to begin with the expected value of an outcome: the expected value of any outcome is the ...
... You can model uncertainty on the basis of willingness to risk loss or gain. Individuals or institutions can be classified as risk-neutral, risk-inclined, or risk-averse. In studying uncertainty, you always have to begin with the expected value of an outcome: the expected value of any outcome is the ...