Cryptanalysis of Stream Cipher
... No security reduction but easy to analyze Not resistant to nonce reuse No incremental tags Flexible implementation sizes: 128/256 Performance: speed/size ...
... No security reduction but easy to analyze Not resistant to nonce reuse No incremental tags Flexible implementation sizes: 128/256 Performance: speed/size ...
MIS409_DB_Security_Auth_Encrypt
... Allowing access to a resource if and only if rules exist that allow a given user to access the resource difficult to manage used for highly sensitive information rules or sensitivity labels make it mandatory. ...
... Allowing access to a resource if and only if rules exist that allow a given user to access the resource difficult to manage used for highly sensitive information rules or sensitivity labels make it mandatory. ...
iPhone iPad Essential - 5 S2017.key
... SMS is now understood to be messaging from one mobile phone to another. ...
... SMS is now understood to be messaging from one mobile phone to another. ...
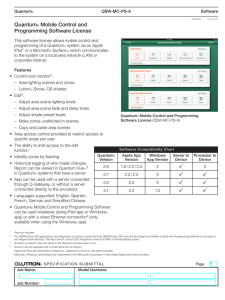
Quantum Mobile Control and Programming Software License
... Q-Admm is used to view the report in the Quantum versions prior to 3.2. Device must be equipped with a wired ethernet connection. Apple and iPad are trademarks of Apple Inc., registered in the U.S. and other countries. Microsoft, Windows, and Surface are trademarks of the Microsoft Corporation in th ...
... Q-Admm is used to view the report in the Quantum versions prior to 3.2. Device must be equipped with a wired ethernet connection. Apple and iPad are trademarks of Apple Inc., registered in the U.S. and other countries. Microsoft, Windows, and Surface are trademarks of the Microsoft Corporation in th ...
Phone Clone — Moving Phone Data at the
... When switching to a new phone, one of the biggest headaches is moving the data from the old phone to the new phone. This is especially true for moving data between phones from different manufacturers using different systems. When switching phones, most people use their SD card. They first move their ...
... When switching to a new phone, one of the biggest headaches is moving the data from the old phone to the new phone. This is especially true for moving data between phones from different manufacturers using different systems. When switching phones, most people use their SD card. They first move their ...
Notification
... owners. Cyber criminals could also use an FTP server in anonymous mode and configured to allow "write" access to store malicious tools or launch targeted cyber attacks. In general, any misconfigured or u nsecured server operating on a business network on which sensitive data is stored or processed e ...
... owners. Cyber criminals could also use an FTP server in anonymous mode and configured to allow "write" access to store malicious tools or launch targeted cyber attacks. In general, any misconfigured or u nsecured server operating on a business network on which sensitive data is stored or processed e ...
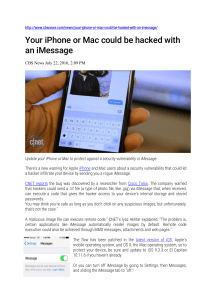
Your iPhone or Mac could be hacked with an iMessage
... http://www.cbsnews.com/news/your-iphone-or-mac-could-be-hacked-with-an-imessage/ ...
... http://www.cbsnews.com/news/your-iphone-or-mac-could-be-hacked-with-an-imessage/ ...
2-3 Using Matrices to Model Real-World Data
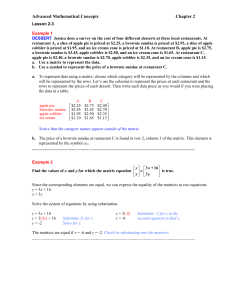
... a. Use a matrix to represent the data. b. Use a symbol to represent the price of a brownie sundae at restaurant C. a. To represent data using a matrix, choose which category will be represented by the columns and which will be represented by the rows. Let’s use the columns to represent the prices at ...
... a. Use a matrix to represent the data. b. Use a symbol to represent the price of a brownie sundae at restaurant C. a. To represent data using a matrix, choose which category will be represented by the columns and which will be represented by the rows. Let’s use the columns to represent the prices at ...
Examples 2.3 - IHMC Public Cmaps (3)
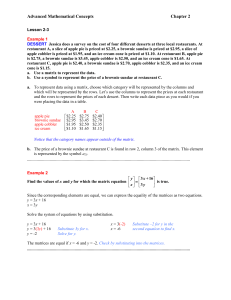
... a. Use a matrix to represent the data. b. Use a symbol to represent the price of a brownie sundae at restaurant C. a. To represent data using a matrix, choose which category will be represented by the columns and which will be represented by the rows. Let’s use the columns to represent the prices at ...
... a. Use a matrix to represent the data. b. Use a symbol to represent the price of a brownie sundae at restaurant C. a. To represent data using a matrix, choose which category will be represented by the columns and which will be represented by the rows. Let’s use the columns to represent the prices at ...
iPads Everywhere!
... • Send suggested apps for users to op-in • Manage Apple Volume Purchase Program codes and distribute them based on various criteria • Managed apps and data can be removed protecting personal data • Prevent backups of managed app data ...
... • Send suggested apps for users to op-in • Manage Apple Volume Purchase Program codes and distribute them based on various criteria • Managed apps and data can be removed protecting personal data • Prevent backups of managed app data ...
acitve and passive voice
... 6. If the subject in the active voice sentence is unknown or unimportant or obvious, by + object is omitted. We make butter from cow’s milk. Butter is made from cow’s milk. 7. If the verb in the active voice sentence has a modal in it, the verb is changed to – modal + be + the past participle. e.g. ...
... 6. If the subject in the active voice sentence is unknown or unimportant or obvious, by + object is omitted. We make butter from cow’s milk. Butter is made from cow’s milk. 7. If the verb in the active voice sentence has a modal in it, the verb is changed to – modal + be + the past participle. e.g. ...