IOSR Journal of Electrical and Electronics Engineering (IOSR-JEEE)
... Due to above factors the traditional power flow methods used in transmission systems, such as the Gauss seidel method and Newton Raphson methods, fail to meet the requirements in both performance and robustness aspects in the distribution system applications. In particular, the assumptions necessary ...
... Due to above factors the traditional power flow methods used in transmission systems, such as the Gauss seidel method and Newton Raphson methods, fail to meet the requirements in both performance and robustness aspects in the distribution system applications. In particular, the assumptions necessary ...
N0254_LL-Status_WG7_meeting_2009-01
... 1.5.1 Leveraging Existing Commercial Standards It is a goal to avoid having redundant and possibly contradictory specifications that exist in conjunction with the ISO/IEEE 11073 series of Transport specifications. There are many commercial Transport standards available that are widely implemented an ...
... 1.5.1 Leveraging Existing Commercial Standards It is a goal to avoid having redundant and possibly contradictory specifications that exist in conjunction with the ISO/IEEE 11073 series of Transport specifications. There are many commercial Transport standards available that are widely implemented an ...
Design and Implementation of an Avionics Full Duplex Ethernet
... Alberto Perez, Technical Manager, System Test & Integration John Hildin, Director of Network Systems John Roach, Vice President of Network Products Division Teletronics Technology Corporation Newtown, PA USA ...
... Alberto Perez, Technical Manager, System Test & Integration John Hildin, Director of Network Systems John Roach, Vice President of Network Products Division Teletronics Technology Corporation Newtown, PA USA ...
IOSR Journal of Electrical and Electronics Engineering (IOSR-JEEE)
... Different definitions of DG have been proposed by Ackermann ect.al in 2001.According to them distributed generation can be defined as the installation and operation of electric power generation units connected directly to the distribution network or connected to the network on the customer side of m ...
... Different definitions of DG have been proposed by Ackermann ect.al in 2001.According to them distributed generation can be defined as the installation and operation of electric power generation units connected directly to the distribution network or connected to the network on the customer side of m ...
modul 3 LOCAL AREA NETWORK
... Topology: Logic bus (physically may be bus or star) Transmit: Only one can transmit at any time, all others receive transmission Speed: 10Mbps, 100Mbps (fast Ethernet) and 1000Mbps (gigabit Ethernet) Status: Most popular LAN and widely used History: Invented at Xerox (Palo Alto Research Center) in 1 ...
... Topology: Logic bus (physically may be bus or star) Transmit: Only one can transmit at any time, all others receive transmission Speed: 10Mbps, 100Mbps (fast Ethernet) and 1000Mbps (gigabit Ethernet) Status: Most popular LAN and widely used History: Invented at Xerox (Palo Alto Research Center) in 1 ...
IEEE C80216m-08/880r3 Project Title
... When transmitting RNG-RSP, BS can further ensure confidentiality in either one of two ways. One, would be for BS to transmit the hashed MAC address in RNG-RSP message. It is then up to the SS/MS to verify the hashed MAC address upon receiving the RNG-RSP. The other method would be for the BS to not ...
... When transmitting RNG-RSP, BS can further ensure confidentiality in either one of two ways. One, would be for BS to transmit the hashed MAC address in RNG-RSP message. It is then up to the SS/MS to verify the hashed MAC address upon receiving the RNG-RSP. The other method would be for the BS to not ...
II. General presentation of Voice over IP
... of placing long distance calls using voice over IP known as toll bypass; however this required setting up a connection between the telephone network (PSTN) and the data network, a task performed by so called Gateways [6]. The result has been additional application for VoIP including: PC-to-phone, ...
... of placing long distance calls using voice over IP known as toll bypass; however this required setting up a connection between the telephone network (PSTN) and the data network, a task performed by so called Gateways [6]. The result has been additional application for VoIP including: PC-to-phone, ...
ppt
... Multicast On Ethernet • Half of addresses reserved for multicast • Network interface card – Always accepts unicast and broadcast – Can accept zero or more multicast addresses ...
... Multicast On Ethernet • Half of addresses reserved for multicast • Network interface card – Always accepts unicast and broadcast – Can accept zero or more multicast addresses ...
Chapter_4_Sec3 - ODU Computer Science
... queuing: if datagrams arrive faster than forwarding rate into switch fabric Network Layer 4-4 ...
... queuing: if datagrams arrive faster than forwarding rate into switch fabric Network Layer 4-4 ...
Wireless Local Area Networks
... Each station is only connected to each of its two nearest neighbors. Data in the form of packets pass around the ring from one station to another in uni-directional way. Advantages : (1) Access method supports heavy load without degradation of performance because the medium is not ...
... Each station is only connected to each of its two nearest neighbors. Data in the form of packets pass around the ring from one station to another in uni-directional way. Advantages : (1) Access method supports heavy load without degradation of performance because the medium is not ...
Intro to Controller Area Network (CAN) (Part 2)
... CAN signaling is bit synchronized across the entire network during the Sync portion which is the time required for each node to synchronize with the leading edge of a recessive to dominant edge transition. The Signal Propagation is the time for the bit signal to propagate throughout the network. Lon ...
... CAN signaling is bit synchronized across the entire network during the Sync portion which is the time required for each node to synchronize with the leading edge of a recessive to dominant edge transition. The Signal Propagation is the time for the bit signal to propagate throughout the network. Lon ...
HP ProCurve Switch 2424M
... • VLAN tagging: provides multiple VLANs over the same physical link • VLAN support: provides security between workgroups • Port monitoring: lets you monitor traffic using a switched port so you can view several ports at one time with an RMON probe • Web interface: lets you monitor your whole network ...
... • VLAN tagging: provides multiple VLANs over the same physical link • VLAN support: provides security between workgroups • Port monitoring: lets you monitor traffic using a switched port so you can view several ports at one time with an RMON probe • Web interface: lets you monitor your whole network ...
Chapter 15 - William Stallings, Data and Computer
... minute detail in the official British Naval History, and should be studied with its excellent charts by those who are interested in its technical aspect. So complicated is the full story that the lay reader cannot see the wood for the trees. I have endeavored to render intelligible the broad effects ...
... minute detail in the official British Naval History, and should be studied with its excellent charts by those who are interested in its technical aspect. So complicated is the full story that the lay reader cannot see the wood for the trees. I have endeavored to render intelligible the broad effects ...
Bridges
... minute detail in the official British Naval History, and should be studied with its excellent charts by those who are interested in its technical aspect. So complicated is the full story that the lay reader cannot see the wood for the trees. I have endeavored to render intelligible the broad effects ...
... minute detail in the official British Naval History, and should be studied with its excellent charts by those who are interested in its technical aspect. So complicated is the full story that the lay reader cannot see the wood for the trees. I have endeavored to render intelligible the broad effects ...
network topology
... Bus Topology is a bus pattern connecting the computers and other devices to the same communication line. All devices are connected in a line to a central cable, called the bus or backbone. There is no central computer or server. The data transmission is bidirectional. ...
... Bus Topology is a bus pattern connecting the computers and other devices to the same communication line. All devices are connected in a line to a central cable, called the bus or backbone. There is no central computer or server. The data transmission is bidirectional. ...
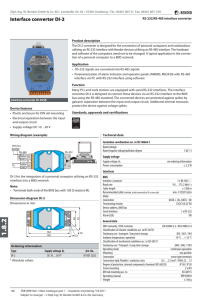
Interface converter DI-2
... utilising an RS-232 interface with Bender devices utilising an RS-485 interface. The hardware and software of the computers need not to be changed. A typical application is the connection of a personal computer to a BMS network. Application • RS-232 signals are converted into RS-485 signals • Parame ...
... utilising an RS-232 interface with Bender devices utilising an RS-485 interface. The hardware and software of the computers need not to be changed. A typical application is the connection of a personal computer to a BMS network. Application • RS-232 signals are converted into RS-485 signals • Parame ...
WiFi Robocar with Network Camera
... human operators have all been taken into account in different works across the literature. Most of them consider Internet as the interconnection network between telecontrolled systems and control stations. IEEE 802.11 Wireless standards can be utilized for many applications depending on characterist ...
... human operators have all been taken into account in different works across the literature. Most of them consider Internet as the interconnection network between telecontrolled systems and control stations. IEEE 802.11 Wireless standards can be utilized for many applications depending on characterist ...
Slide 1
... 1) Protocol stacks are an example of using abstraction to hide complexity. 2) TCP/IP is used for WANs, but LANs use a protocol stack appropriate for the lower latency and higher bandwidths. 3) Although the 802.11 LAN standard is wireless like the cell phone, there is little commonality between the t ...
... 1) Protocol stacks are an example of using abstraction to hide complexity. 2) TCP/IP is used for WANs, but LANs use a protocol stack appropriate for the lower latency and higher bandwidths. 3) Although the 802.11 LAN standard is wireless like the cell phone, there is little commonality between the t ...
Application of Artificial Neural Networks to the Identification of
... Priddy and Keller [7] stated that normalizing the input data for the data collection is important because normalization can minimize the bias within the neural network. Hence, an accurate forecast output results will be obtained. Data normalization can also speed up training time because the trainin ...
... Priddy and Keller [7] stated that normalizing the input data for the data collection is important because normalization can minimize the bias within the neural network. Hence, an accurate forecast output results will be obtained. Data normalization can also speed up training time because the trainin ...
Chapter 4
... • Delineation of Data – A data link protocol must define or delineate where the data portion of the transmitted message begins and ends. This can be accomplished in two basic ways: by framing the data with certain control characters or by using a standard message format wherein data is identified by ...
... • Delineation of Data – A data link protocol must define or delineate where the data portion of the transmitted message begins and ends. This can be accomplished in two basic ways: by framing the data with certain control characters or by using a standard message format wherein data is identified by ...
MP3/WAV Recording/Playback
... a line-in header to use an external audio source instead of the microphone. Most projects using this device will require some form of mass-storage, such as an SD card module. ...
... a line-in header to use an external audio source instead of the microphone. Most projects using this device will require some form of mass-storage, such as an SD card module. ...
Guide to Networking Essentials, Fifth Edition
... FireWire — A high-speed, external serial bus that supports bandwidths up to 400 Mbps and can connect up to 63 devices; also known as IEEE 1394. FireWire is used for streaming video and multimedia, networking, and attaching video devices to computers. hexadecimal — A mathematical notation for rep ...
... FireWire — A high-speed, external serial bus that supports bandwidths up to 400 Mbps and can connect up to 63 devices; also known as IEEE 1394. FireWire is used for streaming video and multimedia, networking, and attaching video devices to computers. hexadecimal — A mathematical notation for rep ...
Layer One Networking
... validity and integrity of the transmission. The transmitted bits are divided into frames; for example, an Ethernet, Token Ring or FDDI frame in local area networks. Layers 1 and 2 are required for every type of communications. ...
... validity and integrity of the transmission. The transmitted bits are divided into frames; for example, an Ethernet, Token Ring or FDDI frame in local area networks. Layers 1 and 2 are required for every type of communications. ...
VMEbus

VMEbus (Versa Module Europa bus) is a computer bus standard, originally developed for the Motorola 68000 line of CPUs, but later widely used for many applications and standardized by the IEC as ANSI/IEEE 1014-1987. It is physically based on Eurocard sizes, mechanicals and connectors (DIN 41612), but uses its own signalling system, which Eurocard does not define. It was first developed in 1981 and continues to see widespread use today.