* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Internet Vulnerabilities & Criminal Activities
Survey
Document related concepts
Network tap wikipedia , lookup
Distributed firewall wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Computer network wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Communication protocol wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Transcript
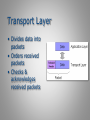
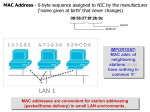
Internet Vulnerabilities & Criminal Activities 1.2 – 9/12/2011 Structure of Internet Communications Computer Data • Binary format – All data represented by only 2 signals – 0’s and 1’s for representation • 5 means of representation – – – – – Electric current Voltage Iron particles “Pits” and “Land” Electron grid • Fragile • Intangible – Must have means of interpreting Protocol The “language” or rules used to transmit data over a network. Common Protocols • HTTP - Hypertext Transfer Protocol • FTP - File Transfer Protocol • SMTP - Simple Mail Transfer Protocol • IP - Internet Protocol • TCP - Transmission Control Protocol • UDP - User Datagram Protocol Packet The unit of data sent from a source to a destination on the Internet Packet format • Header – Information about the packet being sent • Payload – Actual data • Trailer – End of data signal – Also used for error checking Port Virtual ports are part of TCP/IP networking. These ports allow software applications to share hardware resources without interfering with each other. Computers and routers automatically manage network traffic traveling via their virtual ports. Network firewalls additionally provide some control over the flow of traffic on each virtual port for security purposes. Common Port Numbers • 20, 21 - FTP (File Transfer) • 22 - SSH (Secure Shell) • 25 - SMTP (Mail) • 53 - DNS (Domain Name System) • 80 - HTTP (Web Pages) Internet Protocol Number Numerical identification number used by a node on the Internet IP Number Format • IPv4 - 32 bits, 4 bytes long • Each byte separated by a . (dot) • Example - 64.252.150.126 • Divided in to classes by first octet – Class A , 1-126 – Class B, 128-191 – Class C, 192-223 – 127.0.0.1, loopback IPv6 • Succeeds IPv4 • Many more unique numbers available • 128 bit addresses – 2128 possible addresses • Eliminates need for NAT • Offers more features than IPv4 • Typical IPv6 address:2001:0db8:85a3:000 0:0000:8a2e:0370:7334 Domain Name System (DNS) A server that converts domain names into their associated IP number 64.252.150.126 = snet.net OSI - Open Systems Interconnection • Model of network protocols • Created by the ISO • Protocol stack • Each layer responsible for specific processing • Layers only communicate with layer above & layer below • Communications – Outgoing - each layer adds new data – Receiving - each layer strips off data 7 - Applications Layer • Interface between applications program and protocol stack • Layer contacted by application program • Examples - http, ftp, smtp 6 - Presentation Layer • Also called translation layer • Converts data received from application layer to format used by protocol stack • Can be used for compression & encryption 5 - Session Layer • Allows two programs within different computers to establish a communication session • Sets communication markers (not on all networks) 4 - Transport Layer • Interface between application layers and network layers • Protocols - tcp, udp • On sending machine: – Divides data sent by Session layer into packets • On receiving machine: – Puts packets into order – Checks data integrity – Sends acknowledgement 3 - Network Layer • Handles packet addressing • Converts logical address to physical address • Sets route packets will follow from source to destination • Protocol - IP 2 - Data Link Layer • Sending machine – Converts packets into frames – Adds physical address of source and destination machines – Calculates checksum • Receiving machine – Recalculate checksum – Send acknowledgement if checksums match 1 - Physical Layer • Sending machine – Converts Data Link Layer frames into transmission signals • Electronic signal • Luminous signal • Electromagnetic signal • Receiving machine – Converts physical signal into 1’s & 0’s OSI - How it works • Sending machine each layer adds a header • Receiving machine each layer removes a header • Layer only sees header added by same layer on sending machine TCP/IP • Fewer layers than OSI • Different protocols working on different level • May have more than one protocol on the same level Application Layer • Communicates between application programs & transport layer • Protocol selected • Port number assigned Transport Layer • Divides data into packets • Orders received packets • Checks & acknowledges received packets Transport Layer Protocols • TCP - Transmission Control Protocol – Reliable – Used for SMTP, HTTP, FTP • UDP - User Datagram Protocol – Unreliable – Used for DNS Internet Layer • Determines path packet should take from source to destination • Every router on the path is called a hop • Router uses its router table to determine packet’s path • No acknowledgement on this level Network Interface Layer • Most common physical network - Ethernet • Logic Link Control (LLC) Layer – Adds information on Internet layer protocol • Media Access Control (MAC) Layer – Add source & destination MAC address • Physical Layer - same as OSI model Physical Layer Network Interface Frame • Data to be transmitted or received has now been converted to a frame • Each layer adds a header when sending • Each layer removes a header when receiving Communications Log Languages of the Web - HTML • HyperText Markup Language – File extensions: .html, .htm, .html4 – Comprised of elements which tells receiving browser how to display those elements – Hyperlink: link from a web page element to another file or web page – Some elements can pose security risks – Related: Dynamic HTML (DHTML), XML, XHTML Languages of the Web - Perl • Practical Extraction and Report Language – File extension: .pl – High level programming language – Portable, free – Robust & flexible – Server-side actions – Security risk from inputs Languages of the Web - PHP • Personal Home Page – File extensions: .php, .php3 – Server-side scripting language – Used for database applications – Security risk from inputs Languages of the Web - ColdFusion • ColdFusion – File extension: .cfm – Three major components • ColdFusion Application Server - server-side processor of ColdFusion page requests • ColdFusion Markup Language - similar to HTML • ColdFusion Studio - integrated development environment (IDE) • Can be used for database connectivity Languages of the Web - ASP • Active Server Pages – File extension: .asp – Server-side scripting environment – Default language is VBScript – Can be used for database connectivity – ActiveX - used for dynamic web page content Languages of the Web - CGI • Common Gateway Interface – File extensions: .cgi, .pl – Oldest standard for passing information from web server to another program (such as Perl) – Set of guidelines used with many web languages Languages of the Web - Java • Java – File extension: none – Client-based • Scripting languages – Javascript - connected to Java by name only – Jscript - Microsoft’s Javascript clone – Server-based • Java Server Pages (JSP) – File extension: .jsp – Used for dynamic content & database connectivity • JHTML – File extension: .jhtml – HTML with Java Sources • “The OSI Reference Model for Network Protocols” by Gabriel Torres. Hardware Secrets. (2007) http://www.hardwaresecrets.com/article/431 • “How TCP/IP Protocol Works - Part 1” by Gabriel Torres. Hardware Secrets. (2007) http://www.hardwaresecrets.com/article/433 • “How TCP/IP Protocol Works - Part 2” by Gabriel Torres. Hardware Secrets. (2007) http://www.hardwaresecrets.com/article/435 • “Languages of the Web” by Stuart McClure, Saumil Shah, and Shreeraj Shah. Web Hacking: Attacks and Defenses (2003)