* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Security and Ethical Challenges
Survey
Document related concepts
Cracking of wireless networks wikipedia , lookup
Security-focused operating system wikipedia , lookup
Information security wikipedia , lookup
Trusted Computing wikipedia , lookup
Information privacy law wikipedia , lookup
Cyberwarfare wikipedia , lookup
Medical privacy wikipedia , lookup
Mobile security wikipedia , lookup
Cyber-security regulation wikipedia , lookup
International cybercrime wikipedia , lookup
Cyberattack wikipedia , lookup
Computer security wikipedia , lookup
Transcript
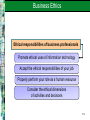
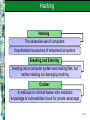
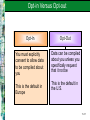
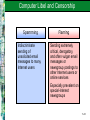
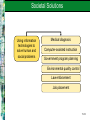
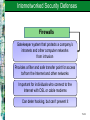
Chapter 11 Security and Ethical Challenges McGraw-Hill/Irwin Copyright © 2010 by the McGraw-Hill Companies, Inc. All rights reserved. Learning Objectives Identify several ethical issues regarding how the use of information technologies in business affects – Employment – Individuality – Working conditions – Privacy – Crime – Health – Solutions to societal problems 11-2 Learning Objectives Identify several types of security management strategies and defenses – Explain how they can be used to ensure the security of business applications of information technology Propose ways that business managers and professionals can help lessen the harmful effects, and increase the beneficial effects, of the use of information technology 11-3 Case 1: Ethics, Moral Dilemmas, Tough Decisions The pervasive use of IT in organizations and society present individuals with new ethical challenges and dilemmas If companies don’t set ethical policies and guidelines, or don’t make sure that employees know what they are and understand them, companies cannot hold workers accountable for their unethical behavior 11-4 Case Study Questions Companies are developing ethical policies and guidelines for legal reasons, but also to clarify what is acceptable and what is not – Do you think any of the issues raised in the case required clarification? – Would you take exception to any of them being classified as inappropriate behavior? – Why do you think these things happen anyway? 11-5 Case Study Questions In the first example (Bryan’s), it is apparent that he did not believe justice had been ultimately served by the decision his company made – Should he have taken the issue to the authorities? – Or, was it enough that he reported the problem through the proper channels and let the organization handle it, as recommended by Linn Hynds? 11-6 Case Study Questions In the case, Gary chose not to stop his boss from installing unlicensed software, although he refused to do it himself – If installing unlicensed software is wrong, is there any difference between refusing to do it versus not stopping somebody else? – Do you buy his argument that it was not really going to hurt anybody? Why or why not? 11-7 IT Security, Ethics, and Society Information technology has both beneficial and detrimental effects on society and people Manage work activities to minimize the detrimental effects Strive to optimize the beneficial effects 11-8 Business Ethics Ethical responsibilities of business professionals Promote ethical uses of information technology Accept the ethical responsibilities of your job Properly perform your role as a human resource Consider the ethical dimensions of activities and decisions 11-9 IT Security, Ethics, and Society 11-10 Categories of Ethical Business Issues 11-11 Corporate Social Responsibility Theories Stockholder Theory Managers are agents of stockholders. Their ethical responsibility is to increase profits without violating laws or engaging in fraud Social Contract Theory Stakeholder Theory Companies have an ethical responsibility to all members of society Managers have an ethical responsibility to manage a firm for the benefit of all its stakeholders 11-12 Principles of Technology Ethics 11-13 Ethical Guidelines of the AITP 11-14 Responsible Professional Guidelines A responsible professional Acts with integrity Increases personal competence Sets high standards of personal performance Accepts responsibility for his/her work Advances the health, privacy, and general welfare of the public 11-15 Computer Crime – Unauthorized use, access, modification, or destruction of hardware, software, data, or network resources – The unauthorized release of information – The unauthorized copying of software – Denying an end user access to his/her own hardware, software, data, or network resources – Using or conspiring to use computer or network resources illegally to obtain information or tangible property 11-16 Corporate Protection Mechanisms 11-17 Hacking Hacking The obsessive use of computers Unauthorized access/use of networked computers Breaking and Entering Hacking into a computer system and reading files, but neither stealing nor damaging anything Cracker A malicious or criminal hacker who maintains knowledge of vulnerabilities found for private advantage 11-18 Common Hacking Tactics 11-19 Cyber Theft Many computer crimes involve theft of money Most are “inside jobs” that involve unauthorized network entry and alteration of databases to cover the tracks of the employees involved Many attacks occur through the Internet Most companies don’t reveal that they have been targets or victims of cyber crime 11-20 Cyberterrorism The leveraging of an organization’s or government’s computers and information – Particularly through the Internet – To cause physical, real-world harm or severe disruption of infrastructure Can have serious, large-scale influence – Can weaken a country’s economy – Can affect Internet-based businesses 11-21 Cyberterrorism Examples of Cyberterrorism Life-support at Antarctic research station turned off Release of untreated sewage into waterways Nonessential systems shut down in nuclear power plants Estonian government ministry and banks knocked offline No successful attacks reported yet in the U.S. 11-22 Unauthorized Use at Work Unauthorized use of computer systems and networks is time and resource theft – Doing private consulting – Doing personal finances – Playing video games – Unauthorized use of Internet or company networks Sniffers – Monitor network traffic or capacity to find evidence of improper use 11-23 Internet Abuses in the Workplace General email abuses Unauthorized use and access Copyright infringement Plagiarism Newsgroup postings Transmission of confidential data Moonlighting Use of external ISPs Leisure use of Internet Pornography Non-work-related downloads or upload Hacking 11-24 Software Piracy Software Piracy – Unauthorized copying of computer programs Licensing – Purchasing software is really a payment for a license for fair use – Site license allows a certain number of copies – Public domain software is not copyrighted A third of the software industry’s revenues are lost to piracy 11-25 Theft of Intellectual Property Intellectual Property – Copyrighted material – Includes music, videos, images, articles, books, and software Copyright Infringement is Illegal – Peer-to-peer networking techniques have made it easy to trade pirated intellectual property Publishers Offer Inexpensive Online Music – Illegal downloading of music and video is down and continues to drop 11-26 Viruses and Worms A virus is a program that cannot work without being inserted into another program – A worm is a distinct program that can run unaided These programs copy annoying or destructive routines into networked computers – Copy routines spread the virus Commonly transmitted through – – – – The Internet and online services Email and file attachments Disks from contaminated computers Shareware 11-27 Top Five Virus Families of all Time My Doom, 2004 – Spread via email and over Kazaa file-sharing network – Installs a back door on infected computers – Infected email poses as returned message or one that can’t be opened correctly, urging recipient to click on attachment – Opens up TCP ports that stay open even after termination of the worm – Upon execution, Notepad is opened, filled with nonsense characters 11-28 Top Five Virus Families of all Time Netsky, 2004 – Mass-mailing worm that spreads by emailing itself to all email addresses found on infected computers – Tries to spread via peer-to-peer file sharing by copying itself into the shared folder – Renames itself to pose as one of 26 other common files along the way 11-29 Top Five Virus Families of all Time SoBig, 2003 – Mass-mailing email worm that arrives as an attachment Examples: Movie_0074.mpg.pif, Document003.pif – Scans all .WAB, .WBX, .HTML, .EML, and .TXT files looking for email addresses to which it can send itself – Also attempts to download updates for itself 11-30 Top Five Virus Families of all Time Klez, 2002 – Mass-mailing email worm that arrives with a randomly named attachment – Exploits a known vulnerability in MS Outlook to auto-execute on unpatched clients – Tries to disable virus scanners and then copy itself to all local and networked drives with a random file name – Deletes all files on the infected machine and any mapped network drives on the 13th of all even-numbered months 11-31 Top Five Virus Families of all Time Sasser, 2004 – Exploits a Microsoft vulnerability to spread from computer to computer with no user intervention – Spawns multiple threads that scan local subnets for vulnerabilities 11-32 The Cost of Viruses, Trojans, Worms Cost of the Top Five Virus Families 115 million computers in 200 countries infected in 2004 Up to 11 million computers permanently infected Total economic damage was $166 to $202 billion in 2004 Average damage per computer is $277 to $366 11-33 Adware and Spyware Adware Spyware 1. Software that purports to serve a useful purpose, and often does 1. Adware that uses an Internet connection in the background, without the user’s permission or knowledge 2. Allows advertisers to display pop-up and banner ads without the consent of the computer user 2. Captures information about the user and sends it over the Internet 11-34 Spyware Problems Spyware can steal private information and… – Add advertising links to Web pages – Redirect affiliate payments – Change a users home page and search settings – Make a modem randomly call premium-rate phone numbers – Leave security holes that let Trojans in – Degrade system performance Spyware often can’t be eliminated 11-35 Privacy Issues The power of information technology to store and retrieve information can have a negative effect on every individual’s right to privacy – Personal information is collected with every visit to a Web site – Confidential information stored by credit bureaus, credit card companies, and the government has been stolen or misused 11-36 Opt-in Versus Opt-out Opt-In Opt-Out You must explicitly consent to allow data to be compiled about you Data can be compiled about you unless you specifically request that it not be This is the default in Europe This is the default in the U.S. 11-37 Additional Privacy Issues Violation of Privacy – Accessing individuals’ private email conversations and computer records – Collecting and sharing information about individuals gained from their visits to Internet websites Computer Monitoring – Always knowing where a person is – Mobile and paging services are becoming more closely associated with people than with places 11-38 Privacy Issues Computer Matching – Using customer information gained from many sources to market additional business services Unauthorized Access of Personal Files – Collecting telephone numbers, email addresses, credit card numbers, and other information to build customer profiles 11-39 Protecting Your Privacy on the Internet Ways to protect your privacy – Encrypt email – Send newsgroup postings through anonymous remailers – Ask your ISP not to sell your name and information to mailing list providers and other marketers – Don’t reveal personal data and interests on online service and website user profiles 11-40 Computer Matching and Profiling Problems caused by mistakes in profiling and computer matching of personal data Individuals mistakenly arrested and jailed Unauthorized information about you sold to information brokers or other companies Barrage of unsolicited promotional material and sales contacts Privacy violations 11-41 Privacy Laws Electronic Communications Privacy Act and Computer Fraud and Abuse Act – Prohibit intercepting data communications messages, stealing or destroying data, or trespassing in federal computer systems U.S. Computer Matching and Privacy Act – Regulates the matching of data held in federal agency files to verify eligibility for federal programs 11-42 Privacy Laws Other laws impacting privacy and how much a company spends on compliance Sarbanes-Oxley Health Insurance Portability & Accountability Act (HIPAA) Gramm-Leach-Bliley USA PATRIOT Act California Security Breach Law Securities and Exchange Commission rule 17a-4 11-43 Computer Libel and Censorship The opposite side of the privacy debate… – Freedom of information, speech, and press Biggest battlegrounds – Bulletin boards – Email boxes – Online files of Internet and public networks Weapons used in this battle – Spamming – Flame mail – Libel laws – Censorship 11-44 Computer Libel and Censorship Spamming Indiscriminate sending of unsolicited email messages to many Internet users Flaming Sending extremely critical, derogatory, and often vulgar email messages or newsgroup postings to other Internet users or online services Especially prevalent on special-interest newsgroups 11-45 Cyberlaw Laws intended to regulate activities over the Internet via electronic communication devices Encompasses a wide variety of legal and political issues Includes intellectual property, privacy, freedom of expression, and jurisdiction 11-46 Cyberlaw The intersection of technology and the law is controversial – Some feel the Internet should not be regulated – Encryption and cryptography make traditional form of regulation difficult – The Internet treats censorship as damage and simply routes around it Cyberlaw only began to emerge in 1996 – Debate continues regarding the applicability of legal principles derived from issues that had nothing to do with cyberspace 11-47 Other Challenges Employment – IT creates new jobs and increases productivity – It can also cause significant reductions in job opportunities, as well as requiring new job skills Computer Monitoring – Using computers to monitor the productivity and behavior of employees as they work – Criticized as unethical; it monitors individuals, not just work, and is done constantly – Criticized as invasion of privacy because many employees do not know they are being monitored 11-48 Other Challenges Working Conditions IT has eliminated monotonous or obnoxious tasks But, some skilled craftsperson jobs have been replaced by jobs requiring routine, repetitive tasks or standby roles Individuality Dehumanizes and depersonalizes activities because computers eliminate human relationships Inflexible systems 11-49 Health Issues Cumulative Trauma Disorders (CTDs) Disorders suffered by people who sit at a PC or terminal and do fast-paced repetitive keystroke jobs Carpal Tunnel Syndrome Painful, crippling ailment of the hand and wrist Typically requires surgery to cure 11-50 Ergonomics Designing healthy work environments Safe, comfortable, pleasant place for people to work Increases employee morale and productivity Also called human factors engineering 11-51 Ergonomic Factors 11-52 Societal Solutions Using information technologies to solve human and social problems Medical diagnosis Computer-assisted instruction Government program planning Environmental quality control Law enforcement Job placement 11-53 Societal Solutions Detrimental effects of information technology – Often caused by individuals or organizations not accepting ethical responsibility for their actions 11-54 Security Management of IT The Internet was developed for inter-operability, not impenetrability – Business managers and professionals alike are responsible for the security, quality, and performance of business information systems – Hardware, software, networks, and data resources must be protected by a variety of security measures 11-55 Case 2: Raymond James Financial, BCD Travel… Leakage of sensitive customer data or proprietary information is a new priority Companies are starting to focus on keeping sensitive information within their boundaries Companies are deploying Outboard content management tools to monitor outgoing information Companies must monitor email messages plus an explosion of alternative communication mechanisms employees use (instant messaging, blogs, FTP transfers, Web mail, message boards) 11-56 Case Study Questions Barring illegal activities, why do you think that employees in the featured organizations failed to realize the dangers of loosely managing proprietary and sensitive information? – Would you have thought of these issues? How should organizations strike the right balance between monitoring and invading their employees’ privacy, even if it was legal for them to do so? – Why is it important to achieve this balance? – What would be the consequences of being too biased to one side? 11-57 Case Study Questions The IT executives in the case all note that outbound monitoring and management technologies are only part of an overall strategy, and not their primary defense – What should the other components of this strategy be? – Which weight would you give to human and technological factors? 11-58 Security Management The goal of security management is the accuracy, integrity, and safety of all information system processes and resources 11-59 Internetworked Security Defenses Encryption – Data is transmitted in scrambled form – It is unscrambled by computer systems for authorized users only – The most widely used method uses a pair of public and private keys unique to each individual 11-60 Public/Private Key Encryption 11-61 Internetworked Security Defenses Firewalls Gatekeeper system that protects a company’s intranets and other computer networks from intrusion Provides a filter and safe transfer point for access to/from the Internet and other networks Important for individuals who connect to the Internet with DSL or cable modems Can deter hacking, but can’t prevent it 11-62 Internet and Intranet Firewalls 11-63 Denial of Service Attacks The victim’s website Denial of service attacks depend on three layers of networked computer systems The victim’s ISP Zombie or slave computers commandeered by cyber criminals 11-64 Defending Against Denial of Service At victim’s Website Create backup servers and network connections At the ISP Monitor & block traffic spikes At Zombie machines Set/enforce security policies Scan for vulnerabilities 11-65 Internetworked Security Defenses Email Monitoring – Use content monitoring software to scan for troublesome words Virus Defenses – Centralize the updating and distribution of antivirus software – Use a security suite that integrates virus protection with firewalls, Web security, and content blocking features 11-66 Other Security Measures Security Codes – Multilevel password system – Encrypted passwords – Smart cards with microprocessors Backup Files – Duplicate files of data or programs Security Monitors – Monitor the use of computers and networks – Protects them from unauthorized use, fraud, and destruction 11-67 Other Security Measures Biometrics Computer devices measure physical traits that make each individual unique Voice recognition, fingerprints, retina scan Computer Failure Controls Prevents computer failures or minimizes its effects Preventive maintenance Arrange backups with a disaster recover organization 11-68 Other Security Measures In the event of a system failure, fault-tolerant systems have redundant processors, peripherals, and software – Fail-over: shifts to back up components – Fail-safe: the system continues to operate at the same level – Fail-soft: the system continues to operate at a reduced but acceptable level 11-69 Other Security Measures A disaster recovery plan contains formalized procedures to follow in the event of a disaster Which employees will participate What their duties will be What hardware, software, and facilities will be used Priority of applications that will be processed Use of alternative facilities Offsite storage of databases 11-70 Information System Controls 11-71 Auditing IT Security IT Security Audits – Performed by internal or external auditors – Review and evaluation of security measures and management policies – Goal is to ensure that that proper and adequate measures and policies are in place 11-72 Protecting Yourself from Cyber Crime 11-73 Case 3: Cyber Scams, Cyber Criminals Cyber scams are today’s fastest-growing criminal niche – 87 percent of companies surveyed reported a security incident – The U.S. Federal Trade Commission says identity theft is its top complaint – eBay has 60 people combating fraud; Microsoft has 65 – Stolen credit card account numbers are regularly sold online 11-74 Case Study Questions List several reasons why “cyber scams are today’s fastest growing criminal niche” – Explain why these reasons contribute to the growth of cyber scams What security measures could be implemented to combat the spread of cyber scams? – Explain why your suggestions would be effective 11-75 Case Study Questions Which of the four top cyber criminals described in this case poses the biggest threat to businesses? To consumers? – Explain the reasons for your choices, and describe how businesses and consumers can protect themselves from these cyber scammers 11-76