* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Ch10 - Protection Mechanism
Survey
Document related concepts
Proxy server wikipedia , lookup
Cross-site scripting wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Access control wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Denial-of-service attack wikipedia , lookup
Security-focused operating system wikipedia , lookup
Computer security wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Network tap wikipedia , lookup
Mobile security wikipedia , lookup
Deep packet inspection wikipedia , lookup
Wireless security wikipedia , lookup
Cybercrime countermeasures wikipedia , lookup
Unix security wikipedia , lookup
Transcript
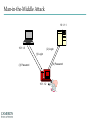
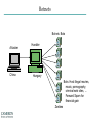
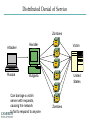
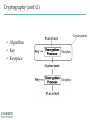
INFORMATION SECURITY MANAGEMENT CHAPTER 10: PROTECTION MECHANISMS You got to be careful if you don’t know where you’re going, because you might not get there. – Yogi Berra Windows XP Zero days turn to "forever days" http://windows.microsoft.com/enus/windows/end-support-help Hacking Networks Phase 1: Reconnaissance Physical Break-In Registrant: Microsoft Corporation One Microsoft Way Redmond, WA 98052 US Dumpster Diving Domain name: MICROSOFT.COM Google, Newsgroups, Web sites Social Engineering Phishing: fake email Pharming: fake web pages WhoIs Database Domain Name Server Interrogations Administrative Contact: Administrator, Domain [email protected] One Microsoft Way Redmond, WA 98052 US +1.4258828080 Technical Contact: Hostmaster, MSN [email protected] One Microsoft Way Redmond, WA 98052 US +1.4258828080 Registration Service Provider: DBMS VeriSign, [email protected] 800-579-2848 x4 Please contact DBMS VeriSign for domain updates, DNS/Nameserver changes, and general domain support questions. Registrar of Record: TUCOWS, INC. Record last updated on 27-Aug-2006. Record expires on 03-May-2014. Record created on 02-May-1991. Domain servers in listed order: NS3.MSFT.NET 213.199.144.151 NS1.MSFT.NET 207.68.160.190 NS4.MSFT.NET 207.46.66.126 NS2.MSFT.NET 65.54.240.126 NS5.MSFT.NET 65.55.238.126 Hacking Networks Phase 2: Scanning War Driving: Can I find a wireless network? War Dialing: Can I find a modem to connect to? Network Mapping: What IP addresses exist, and what ports are open on them? Vulnerability-Scanning Tools: What versions of software are implemented on devices? Passive Attacks Eavesdropping: Listen to packets from other parties = Sniffing Traffic Analysis: Learn about network from observing traffic patterns Footprinting: Test to determine software installed on system = Network Mapping Hacking Networks: Phase 3: Gaining Access Network Attacks: Sniffing (Eavesdropping) IP Address Spoofing Session Hijacking System Attacks: Buffer Overflow Password Cracking SQL Injection Web Protocol Abuse Denial of Service Trap Door Virus, Worm, Trojan horse, Some Active Attacks Denial of Service: Message did not make it; or service could not run Masquerading or Spoofing: The actual sender is not the claimed sender Message Modification: The message was modified in transmission Packet Replay: A past packet is transmitted again in order to gain access or otherwise cause damage Man-in-the-Middle Attack 10.1.1.1 10.1.1.3 (2) Login (1) Login (4) Password (3) Password 10.1.1.2 Hacking Networks: Phase 4: Exploit/Maintain Access Control system: system commands, log keystrokes, pswd Backdoor Trojan Horse Useful utility actually creates a backdoor. Replaces system User-Level Rootkit executables: e.g. Login, ls, du Bots Slave forwards/performs commands; spreads, list email addrs, DOS attacks Spyware/Adware Spyware: Collect info: keystroke logger, collect credit card #s, AdWare: insert ads, filter search results Replaces OS kernel: Kernel-Level e.g. process or file Rootkit control to hide Botnets Botnets: Bots Attacker China Handler Hungary Bots: Host illegal movies, music, pornography, criminal web sites, … Forward Spam for financial gain Zombies Distributed Denial of Service Zombies Attacker Russia Handler Victim Bulgaria United States Can barrage a victim server with requests, causing the network to fail to respond to anyone Zombies Introduction • Threats -> Vulnerabilities -> Risk ->Controls • Technical controls – Must be combined with sound policy and education, training, and awareness efforts • Examples of technical security mechanisms Sphere of Protection Source: Course Technology/Cengage Learning Access Controls • The four processes of access control – – – – Identification Authentication Authorization Accountability • A successful access control approach always incorporates all four of these elements Access Controls – Password Strength Table 10-1 Password power Source: Course Technology/Cengage Learning Acceptability of Biometrics • Note: Iris Scanning has experienced rapid growth in popularity and due to it’s acceptability, low cost, and effective security Firewalls • Any device that prevents a specific type of information from moving between two networks Types: • Packet Filtering • Application Level • Stateful Inspection Firewalls Packet filtering firewalls Simple networking devices that filter packets by examining every incoming and outgoing packet header Application-level firewalls – Consists of dedicated computers kept separate from the first filtering router (edge router) – Commonly used in conjunction with a second or internal filtering router - or proxy server – Implemented for specific protocols Stateful inspection firewalls – Keeps track of each network connection established between internal and external systems using a state table – Can restrict incoming packets by allowing access only to packets that constitute responses to requests from internal hosts Firewall Architectures • Each firewall generation can be implemented in several architectural configurations • Common architectural implementations – Packet filtering routers – Screened-host firewalls Firewall Architectures: Packet filtering routers Most organizations with an Internet connection use some form of router between their internal networks and the external service provider Firewall Architectures: Screened-host firewall systems • Combine the packet filtering router with a separate, dedicated firewall such as an application proxy server Selecting the Right Firewall • • • • Firewall Technology Cost Maintenance Future Growth Managing Firewalls • Any firewall device must have its own configuration • Firewall Rules • Policy regarding firewall use • Firewall best practices – All traffic from the trusted network allowed out – The firewall is never accessible directly from the public network – Email Policies Intrusion Detection and Prevention Systems (IDPS) • The term intrusion detection/prevention system (IDPS) can be used to describe current anti-intrusion technologies • Like firewall systems, IDPSs require complex configurations to provide the level of detection and response desired Intrusion Detection and Prevention Systems (cont’d.) IDPS technologies can respond to a detected threat by attempting to prevent it from succeeding Network or Host Based Protection IDPS – Host vs. Network http://www.windowsecurity.com/articles-tutorials/intrusion_detection/Hids_vs_Nids_Part1.html Signature-Based IDPS • Examines data traffic for something that matches the preconfigured, predetermined attack pattern signatures • Weakness: slow and methodical attacks may slip undetected through the IDPS, as their actions may not match a signature that includes factors based on duration of the events Statistical Anomaly-Based IDPS • First collects data from normal traffic and establishes a baseline – Then periodically samples network activity, based on statistical methods, and compares the samples to the baseline • Advantage: Able to detect new types of attacks, because it looks for abnormal activity of any type Managing IDPS • IDPSs must be configured to differentiate between routine circumstances and low, moderate, or severe threats • A properly configured IDPS can translate a security alert into different types of notifications • Most IDPSs monitor systems using agents • Consolidated enterprise manager Honeypot & Honeynet Honeypot: A system with a special software application which appears easy to break into Honeynet: A network which appears easy to break into Purpose: Catch attackers All traffic going to honeypot/net is suspicious If successfully penetrated, can launch further attacks Must be carefully monitored Firewall Honey Pot External DNS IDS Web Server E-Commerce VPN Server Remote Access Protection • Network connectivity using external connections – Usually much simpler and less sophisticated than Internet connections – Simple user name and password schemes are usually the only means of authentication Managing Connections • Organizations that continue to offer remote access must: – – – – Determine how many connections the organization has Control access to authorized modem numbers Use call-back whenever possible Use token-based authentication if at all possible Wi-Fi security SSID should be a non-default value SSID broadcast should be disabled MAC access control Authentication • Require ID and password, may use a RADIUS server Encryption • WEP (Wired Equivalent Privacy) • WPA (Wireless Protected Access) • WPA2 (superset of WPA, full standard) Managing Wireless Connections • Regulate the wireless network footprint • Select WPA or WPA2 over WEP • Protect preshared keys Scanning and Analysis Tools • Used to find vulnerabilities in systems • Security administrators may use attacker’s tools to examine their own defenses and search out areas of vulnerability • Scanning tools • Footprinting • Fingerprinting Pen Testing Article “What is Penetration Testing?” Port Scanners • Port scanning utilities (port scanners) Vulnerability Scanners • Capable of scanning networks for very detailed information • Identify exposed user names and groups, show open network shares, and expose configuration problems and other server vulnerabilities http://www.tenable.com/products/nessus Packet Sniffers • A network tool that collects and analyzes packets on a network • Connects directly to a local network from an internal location http://www.wireshark.org/ Content Filters • A software program or a hardware/software appliance that allows administrators to restrict content that comes into a network • Common application of a content filter – Restriction of access to Web sites with non-business-related material, such as pornography, or restriction of spam e-mail Examples of Content Filters Trap and Trace • Trap – Describes software designed to entice individuals who are illegally perusing the internal areas of a network • Trace – A process by which the organization attempts to determine the identity of someone discovered in unauthorized areas of the network or systems Managing Scanning and Analysis Tools • The security manager must be able to see the organization’s systems and networks from the viewpoint of potential attackers • Drawbacks: – Tools do not have human-level capabilities – Most tools function by pattern recognition, so they only handle known issues – Some governments, agencies, institutions, and universities have established policies or laws that protect the individual user’s right to access content – Tool usage and configuration must comply with an explicitly articulated policy, and the policy must provide for valid exceptions Cryptography • Encryption – The process of converting an original message into a form that cannot be understood by unauthorized individuals • Cryptology – The science of encryption – Composed of two disciplines: – cryptography – cryptanalysis Cryptography (cont’d.) Cryptosystem • Algorithm • Key • Keyspace Encipher Decipher Cryptography Article