* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Guide to Firewalls and Network Security with Intrusion Detection and
Computer and network surveillance wikipedia , lookup
Deep packet inspection wikipedia , lookup
Unix security wikipedia , lookup
Computer security wikipedia , lookup
Stingray phone tracker wikipedia , lookup
Trusted Computing wikipedia , lookup
Security-focused operating system wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Wireless security wikipedia , lookup
Quantum key distribution wikipedia , lookup
One-time pad wikipedia , lookup
Cryptanalysis wikipedia , lookup
Mobile security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Distributed firewall wikipedia , lookup
Pretty Good Privacy wikipedia , lookup
Public-key cryptography wikipedia , lookup
Digital signature wikipedia , lookup
Diffie–Hellman key exchange wikipedia , lookup
Certificate authority wikipedia , lookup
Cryptography wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
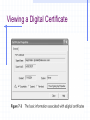
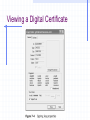
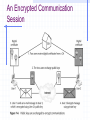
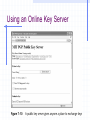
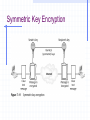
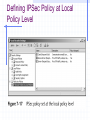
Encryption and Firewalls Chapter 7 Learning Objectives Understand the role encryption plays in firewall architecture Know how digital certificates work and why they are important security tools Analyze the workings of SSL, PGP, and other popular encryption schemes Enable Internet Protocol Security (IPSec) and identify its protocols and modes Encryption Process of encoding and decoding information to: Preserve its integrity Maintain privacy Ensure identity of users participating in the encrypted data session Why Firewalls Need to Use Encryption Hackers take advantage of a lack of encryption Encryption: Preserves data integrity Increases confidentiality Is relied upon by user authentication Plays a fundamental role in enabling VPNs Hackers Take Advantage of a Lack of Encryption Hackers Take Advantage of a Lack of Encryption The Cost of Encryption CPU resources and time Bastion host that hosts the firewall should be robust enough to manage encryption and other security functions Encrypted packets may need to be padded to uniform length to ensure that some algorithms work effectively Can result in slowdowns Monitoring can burden system administrator Preserving Data Integrity Even encrypted sessions can go wrong as a result of man-in-the-middle attacks Encryption can perform nonrepudiation using a digital signature Maintaining Confidentiality Encryption conceals information to render it unreadable to all but intended recipients Authenticating Network Clients Firewalls need to trust that the person’s claimed identity is genuine Firewalls that handle encryption can be used to identify individuals who have “digital ID cards” that include encrypted codes Digital signatures Public keys Private keys Enabling VPNs As an integral part of VPNs, encryption: Enables the firewall to determine whether the user who wants to connect to the VPN is actually authorized to do so Encodes payload of information to maintain privacy Digital Certificates and Public and Private Keys Digital certificate Electronic document that contains a digital signature (encrypted series of numerals and characters), which authenticates identity of person sending certificate Keys Basis of digital certificates and signatures Enable holders of digital certificates to encrypt communications (using their private key) or decrypt communications (using sender’s public key) Digital Certificates Transport encrypted codes (public and private keys) through the firewall from one host to another Help ensure identity of the individual who owns the digital certificate Provide another layer of security in firewall architecture Aspects of Digital Certificates Establishment of an infrastructure for exchanging public and private keys Need to review and verify someone’s digital certificate Difference between client- and server-based digital certificates The Private Key Infrastructure Lightweight Directory Access Protocol (LDAP) Publicly available database that holds names of users and digital certificates Public-Key Infrastructure (PKI) Enables distribution of digital certificates and public and private keys Underlies many popular and trusted security schemes (eg, PGP and SSL) Viewing a Digital Certificate Viewing a Digital Certificate Types of Digital Certificates a Firewall Will Encounter Client-based digital certificates Obtained by users from a Certification Authority (CA), which issues them and vouches for owner’s identity Server-based digital certificates Issued by a CA to a company that issues them to individuals Keys Value generated by an algorithm that can also be processed by an algorithm to encrypt or decrypt text Length of the key determines how secure the level of encryption is Aspects of Keys That Pertain to Firewall-Based Encryption Public and private keys Need to generate public keys Need to securely manage private keys Need to use a key server either on network or Internet Differences between private and public key servers Public and Private Keys Private key Secret code generated by an algorithm Never shared with anyone Public key Encoded information generated when private key is processed by the same algorithm Can be exchanged freely with anyone online A Public Key Generated by PGP An Encrypted Communication Session Choosing the Size of Keys Generating Keys Managing Keys Manual distribution Use of a CA Use of a Key Distribution Center (KDC) Using a Key Server That Is on Your Network Using an Online Key Server Analyzing Popular Encryption Schemes Symmetric key encryption Asymmetric key encryption Pretty Good Privacy (PGP) Secure Sockets Layer (SSL) Symmetric Encryption Use of only one key to encrypt information, rather than a public-private key system Same key is used to encrypt/decrypt a message Both sender and recipient must have same key Not scalable Symmetric Key Encryption Asymmetric Encryption Uses only one user’s public key and private key to generate unique session keys that are exchanged by users during a particular session Only the private key must be kept secret Scales better than symmetric encryption Disadvantages Slower Only a few public key algorithms are available (eg, RSA and EIGamal) that are secure and easy to use for both encryption and key exchange Asymmetric Key Encryption PGP Hybrid system that combines advantages of asymmetric (scalability) and symmetric (speed) encryption systems PGP Process File/message is encrypted Session key is encrypted using public key half of asymmetric public-private key pair Recipient of encrypted message uses his/her private key to decode the session key Session key is used to decode message/file Encryption schemes used to generate public and private key pairs Rivest-Shamir-Adleman (RSA) encryption Diffie-Hellman encryption Using PGP Using PGP X.509 Standard set of specifications for assembling and formatting digital certificates and encrypting data within them A commonly used type of PKI Widely used and well trusted X.509 and PGP Compared X.509 Perception of trust PGP Does not make use of the CA concept Gives users ability to wipe files from hard disk (and delete permanently) Available both in freeware and commercial versions X.509 and PGP Compared SSL Secure way to transmit data Uses both symmetric and asymmetric keys Asymmetric keys start an SSL session Symmetric keys are dynamically generated for the bulk of the transfer Using Internet Protocol Security (IPSec) Encryption Creates a secure IP connection between two computers Operates under the Application layer Transparent to users Understanding IPSec Set of standards and software tools that encrypt IP connections between computers Allows a packet to specify a mechanism for authenticating its origin, ensuring data integrity, and ensuring privacy Modes of IPSec Transport mode Tunnel mode Choice depends on type of network and whether it uses NAT Transport Mode IPSec authenticates two computers that establish a connection Can optionally encrypt packets Does not use a tunnel Tunnel Mode IPSec encapsulates IP packets and can optionally encrypt them Encrypts packet headers rather than the data payload Incompatible with NAT IPSec Protocols Authentication Header (AH) Encapsulation Security Payload (ESP) Authentication Header (AH) Adds a digital signature to packets to protect against repeat attacks, spoofing, or other tampering Verifies that parts of packet headers have not been altered between client and IPSecenabled host Incompatible with NAT AH Encapsulation Security Payload (ESP) More robust than AH; encrypts data part of packets as well as the headers Provides confidentiality and message integrity Can cause problems with firewalls that use NAT Components of IPSec Two modes: transport and tunnel Two protocols: AH and ESP IPSec driver Internet Key Exchange (IKE) Internet Security Association Key Management Protocol (ISAKMP) Oakley IPSec Policy Agent Choosing the Best IPSec Mode for Your Organization Choosing the Best IPSec Mode for Your Organization ESP plus tunnel mode provides best level of protection ESP conceals IP header information Tunnel mode can both encapsulate and encrypt packets Enabling IPSec Select group policy security setting for computers that need to communicate with enhanced security Define at group policy level in Windows 2000 Define at local policy level if not in Windows 2000 Predefined IPSec policy levels in Windows 2000 or XP: Client (Respond only) Server (Request Security) Secure Server (Require Security) Defining IPSec Policy at Local Policy Level Limitations of IPSec If machine that runs IPSec-compliant software has been compromised, communications from that machine cannot be trusted Encrypts IP connection between two machines— not the body of e-mail messages or content of other communications Not an end-to-end security method Authenticates machines, not users Doesn’t prevent hackers from intercepting encrypted packets Chapter Summary How and why encryption is used in a network How to use encryption to complement the firewall’s activities Encryption applications PGP SSL IPSec Schemes that can form part of a firewall architecture