* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Network Security Analysis Prepared By: cowave Communication
Survey
Document related concepts
Information security wikipedia , lookup
Cyberwarfare wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Unix security wikipedia , lookup
Deep packet inspection wikipedia , lookup
Airport security wikipedia , lookup
Wireless security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Mobile security wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Security-focused operating system wikipedia , lookup
Computer security wikipedia , lookup
Transcript
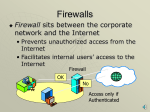
Client and workstation Security Server Security LAN/WAN monitoring Developing a Security Plan on firewalls, proxy servers and border routers Computer network security Aspects The computer-related assets are accessed only by authorized parties. Network integrity is to maintain the data validity by the users from making illegal changing / deleting of data. Data availability means that computer assets are accessible to authorized parties Computer Network Security analysis 1. Select best of computer configurations with inbuilt security covers with customized solutions. 2. Security solutions should be one of the best who release update regularly. METHODS OF DEFENSE: prevent it, by firewall blocking the attack. Deflect it, by making another target more attractive by put them in time consuming loops. Types of Attacks: Attacks against Intern Protocol Internet protocol hacking Network security Threats Data Destruction. Stay updated with current with relevant operating system. Regularly make security updates to protect from threats. One dedicated staff to work as security experts. Build internal and external firewalls Types of firewalls Application Gateways: The first firewalls were application gateways, and are sometimes known as proxy gateways. Hybrid System is an: The security application layer gateways with the flexibility and speed of packet filtering. Conclusions Network security is all terms levels of risk. The key for building a secure organization network is to understand what data security means to your organization. Data and Network security is everybody's responsibility in the company and everyone's needs to be contributed by not allowing any malicious programs to run.