* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download layering
Survey
Document related concepts
Computer security wikipedia , lookup
Network tap wikipedia , lookup
Deep packet inspection wikipedia , lookup
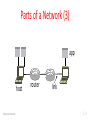
Wake-on-LAN wikipedia , lookup
Airborne Networking wikipedia , lookup
Computer network wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
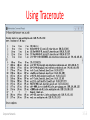
TCP congestion control wikipedia , lookup
Zero-configuration networking wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Transcript
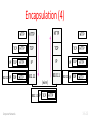
Network Technologies essentials Week 1: Network structures Compilation made by Tim Moors, UNSW Australia Original slides by David Wetherall, University of Washington ISBN-10: 0133766624 © 2014 For the book A. Tanenbaum and D. Wetherall: Computer Networks, 5th ed, Prentice-Hall, 2011 About Essentials • Reflect Tim’s view of the most important slides of the week. • Use as an introductory overview, shorter than viewing everything, or review • Somewhat biased towards slides that give details rather than introduce concepts • Bottom right corner identifies each slide’s source in the form w-v.s, where – w=week, – v=video # from week w – s=slide # from w-v Computer Networks 0-0.0 2 Statistical Multiplexing • Sharing of network bandwidth between users according to the statistics of their demand – (Multiplexing just means sharing) – Useful because users are mostly idle and their traffic is bursty • Key question: – How much does it help? Computer Networks 1-2.6 3 Statistical Multiplexing (2) • Example: Users in an ISP network – Network has 100 Mbps (units of bandwidth) – Each user subscribes to 5 Mbps, for videos – But a user is active only 50% of the time … • How many users can the ISP support? – With dedicated bandwidth for each user: 5 100 ... ISP 5 5 – Probability all bandwidth is used: (assuming independent users) Computer Networks 1-2.7 4 Statistical Multiplexing (3) • With 30 independent users, still unlikely (2% chance) to need more than 100 Mbps! – Binomial probabilities → Can serve more users with the same size network – Statistical multiplexing gain is 30/20 or 1.5X – But may get unlucky; users will have degraded service Computer Networks 1-2.8 5 The Value of Connectivity • “Metcalfe’s Law” ~1980: Bob Metcalfe – The value of a network of N nodes is proportional to N2 – Large networks are relatively more valuable than small ones : © 2009 IEEE Computer Networks 1-2.14 6 The Value of Connectivity (2) • Example: both sides have 12 nodes, but the left network has more connectivity vs Computer Networks + 1-2.15 7 Parts of a Network (3) app host Computer Networks router link 1-3.4 8 Types of Links • Full-duplex – Bidirectional • Half-duplex – Bidirectional • Simplex – unidirectional Computer Networks 1-3.6 9 Wireless Links • Message is broadcast – Received by all nodes in range – Not a good fit with our model Computer Networks 1-3.7 10 Network Boundaries (3) • Cloud as a generic network app host Computer Networks router link 1-3.17 11 Traceroute (3) ... 1 hop Local Host Computer Networks 2 hops 3 hops N-1 hops N hops Remote Host 1-5.5 12 Using Traceroute Computer Networks 1-5.6 13 Protocols and Layers • Protocols and layering is the main structuring method used to divide up network functionality – Each instance of a protocol talks virtually to its peer using the protocol – Each instance of a protocol uses only the services of the lower layer Computer Networks 1-6.4 14 Protocols and Layers (4) • Set of protocols in use is called a protocol stack Computer Networks 1-6.7 15 Encapsulation • Encapsulation is the mechanism used to effect protocol layering – Lower layer wraps higher layer content, adding its own information to make a new message for delivery – Like sending a letter in an envelope; postal service doesn’t look inside Computer Networks 1-6.10 16 Encapsulation (4) HTTP HTTP HTTP TCP HTTP TCP TCP IP TCP HTTP IP IP 802.11 IP TCP HTTP 802.11 802.11 (wire) 802.11 IP TCP Computer Networks HTTP TCP HTTP IP TCP HTTP 802.11 IP TCP HTTP HTTP 1-6.13 17 Encapsulation (5) • Normally draw message like this: – Each layer adds its own header 802.11 IP First bits on the wire TCP HTTP Last bits • More involved in practice – Trailers as well as headers, encrypt/compress contents – Segmentation (divide long message) and reassembly Computer Networks 1-6.14 18 Demultiplexing (2) • Done with demultiplexing keys in the headers SMTP TCP port number HTTP TCP DNS UDP IP protocol field IP Ethertype value Ethernet Host Ethernet IP Computer Networks ARP TCP Incoming message HTTP 1-6.16 19 Advantage of Layering (4) • Using information hiding to connect different systems Browser Server HTTP IP TCP HTTP HTTP TCP TCP IP IP IP IP 802.11 802.11 Ethernet Ethernet 802.11 Computer Networks IP TCP HTTP Ethernet IP TCP HTTP 1-6.20 20 Internet Reference Model (3) • IP is the “narrow waist” of the Internet – Supports many different links below and apps above 7 Application 4 Transport 3 Internet 2/1 Link Computer Networks SMTP HTTP RTP TCP DNS UDP IP Ethernet Cable DSL 3G 802.11 1-7.6 21 Layer-based Names (2) • For devices in the network: Repeater (or hub) Switch (or bridge) Router Computer Networks Physical Physical Link Link Network Network Link Link 1-7.9 22 END © 2013 D. Wetherall Slide material from: TANENBAUM, ANDREW S.; WETHERALL, DAVID J., COMPUTER NETWORKS, 5th Edition, © 2011. Electronically reproduced by permission of Pearson Education, Inc., Upper Saddle River, New Jersey Computer Networks 23




























![Computer Networks [Opens in New Window]](http://s1.studyres.com/store/data/001432217_1-c782ef807e718d5ed80f4e9484b1006a-150x150.png)