* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Security
Secret sharing wikipedia , lookup
Trusted Computing wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Authentication wikipedia , lookup
Cross-site scripting wikipedia , lookup
Information security wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Cyber-security regulation wikipedia , lookup
One-time pad wikipedia , lookup
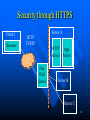
Quantum key distribution wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Unix security wikipedia , lookup
Distributed firewall wikipedia , lookup
Electronic authentication wikipedia , lookup
Mobile security wikipedia , lookup
Secure multi-party computation wikipedia , lookup
Wireless security wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Computer security wikipedia , lookup
Public-key cryptography wikipedia , lookup
Cryptanalysis wikipedia , lookup
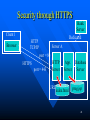
Digital signature wikipedia , lookup
Security-focused operating system wikipedia , lookup
Web of trust wikipedia , lookup
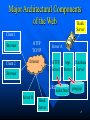
Cryptography wikipedia , lookup
Diffie–Hellman key exchange wikipedia , lookup
History of cryptography wikipedia , lookup
Certificate authority wikipedia , lookup
Security and Authentication Daniel L. Silver, Ph.D. Acadia & Dalhousie Univs. Objectives To introduce the basics E-Commerce security issues and web entity authentication 2 Outline Why is security such an issue? Physical security IT Security Basics – Firewalls Public Key Cryptography SSL – Secure Socket Layer SET – Secure Electronic Transactions 3 Why is Security an Issue? The Internet lets you travel outside of your network and others travel in – Those travelers are not all friendly! Critical and private information can be snooped — sniffed Information can be deleted or destroyed The Internet provides an opportunity for anonymous and rapid theft of lots of money 4 How many categories/classes of security invasions/breaches can you find? User/password – shoulder surfing Trojan horses Password breaking (various strategies) Denial of service attacks – flood the server with requests Packet sniffing on net (wire tap, wireless recon.) Spoofing websites Dumpster diving – garbage search 5 Components of Security Diagram by Konstantin Beznosov 7 Five Major Requirements of a Secure Transaction Privacy – how to ensure information has not been captured by a third party Integrity – how to ensure the information has not been altered in transit Authentication – how to ensure the identity of the sender and receiver Authorization – how to ensure a user has the authority to access / update information Non-repudiation – how do you legally prove that a message was sent or received 8 Physical Security Large mainframe systems have always had adequate physical security The transition from LAN to WAN to Internet has caused new interest in these methods Physical security means locked doors and security personnel Options are to host on a secure ISP/ASP (InternetHosting.com) 9 IT Security Basics Avoidance – preventing a security breach – Using a firewall system to frontend your intranet (or LAN) to the Internet Minimization – early warning signals and action plans so as to reduce exposure – Attempted to access secure directories Recovery - regular backups should be made and recovery periodically tested 10 Using a Firewall – A firewall server or router acts as an electronic security cop – No machine other than firewall is directly accessible from Internet – May also function as a “proxy” server allowing intranet systems to access only portions of the Internet – Internet security methods are focused at the firewall reducing cost and admin overhead 11 Security through HTTPS Client 1 Browser Server A HTTP TCP/IP HTTP Server Fire Wall Server App. Server Server B Server C 12 IT Security Basics Passwords (and potentially User Ids) should be forced to change periodically Passwords should be difficult to guess – Try to create passwords such as: To Be or Not To Be 2bon2b Databases should be secured in terms of access rights to data (usually by individual or group) 13 IT Security Basics Software, particularly low layer components such as the operating system and DBMS, should be kept to recent patch levels Access from dial-in lines should be limited and if possible call-back systems can be used 14 Cryptography Cryptography or ciphering is an ancient method of encoding a message — only a receiver with a key can decipher the content A single (symmetric) secret key is used to encrypt and decrypt Requires the communication of the key between sender and receiver! Basis of nuclear war-head command and control security 15 Public Key Cryptography In 1976 Diffie & Hellman at Stanford U. developed public-key cryptography Asymmetric: – Private key – kept secret by owner – Public key – distributed freely to all who wish to send – Generated by computer algorithm, so a mathematical relation exists between them ... however ... – It is computationally difficult to determine the private key from the public key, even with knowledge of the encryption algorithm 17 Public Key Cryptography The keys come in the form of tightly coupled pairs which anyone can generate using methods such as RSA, SHA-1, DSA (RSA is most common) – Javascript demo: http://shop-js.sourceforge.net/crypto2.htm There is only one public key corresponding to any one private key and vice versa Sender encodes data using public key of receiver Receiver decodes data using unique private key, no one else can do the same This ensures integrity of the data 18 Authentication How can you be sure that the person sending the encrypted data is who they say they are This requires some method of authenticating the identity of the sender The solution is for the sender to “sign” the data using his/her private key – the data is encrypted using the sender’s private key The receiver validates (decrypts the data) the “signature” using the sender’s public key This will work as long as receiver can be sure the sender’s public key belongs to the sender and not an imposter … enter PKI 19 Integrity and Authentication Example: Consider a merchant wants to send a secure message to a customer: – Merchant encrypts message using customer’s public key – Merchant then signs message by encrypting with their private key – Customer decrypts using the merchants public key to prove authenticity of sender – Customer decrypts using their private key to ensure integrity of message 20 PKI – Public Key Infrastructure Integrates PK cryptography with digital certificates and certificate authorities (CA) Digital certificate = issued by a CA, includes user name, public key, serial number, expiration date, signature of trusted CA (message encrypted by CA’s private key) Receipt of a valid certificate is proof of identity – can be checked at CAs sight www.verisign.com is major player 21 Model for Network Security Sender Message Trusted Third Party Authentication or Certificate Authority Receiver Message Information Channel Secret Information Secret Information Opponent 22 Security and HTTPS Certificate is an entity’s public key plus other identification (name, CA signature) SSL – Secure Socket Layer – Lies between TCP/IP and HTTP and performs encryption HTTPS is the HTTP protocol that employs SSL – it uses a separate server port (default = 443) 23 Security through HTTPS Bank Server Dedicated Client 1 Browser HTTP TCP/IP Server A port = 80 HTTPS port = 443 HTTP Server URL App. Server index.html Database Server prog.jsp 24 SSL – Secure Socket Layer 1. 2. 3. 4. 5. 6. Client makes HTTPS connection to server Server sends back SSL version and certificate Client checks if certificate from CA Client creates session “premaster secret”, encrypts it and sends it to server and creates “master secret” Server uses its private key to decrypt “premaster secret” and create the same “master secret” The master secret is used by both to create session keys for encryption and decryption 25 SET – Secure Electronic Transfer Developed by Visa & Mastercard Designed to protect E-Comm transactions SET uses digital certificates to authenticate customer, merchant and financial institution Merchants must have digital certificate and special SET software Customers must have digital certificate and SET e-Wallet software 26 Major Architectural Components of the Web Bank Server Client 1 Browser Client 2 HTTP TCP/IP Internet Browser Server A HTTP Server URL Server B App. Server index.html Database Server prog.jsp Bank Server 27 Resources / References RSA demos: http://cisnet.baruch.cuny.edu/holowczak/classes/9444/rsademo/ http://islab.oregonstate.edu/koc/ece575/02Project/Mor/ 28